SAP RECON Vulnerability: Ongoing Exploitation & Lessons Learned From Onapsis

Understanding the SAP RECON Vulnerability (CVE-2020-6287)
Nearly five years ago, one of the most critical vulnerabilities in SAP security history, known as SAP RECON (CVE-2020-6287), was publicly disclosed following its patch on July 14, 2020. Just 72 hours after the patch was released, reliable exploits of the vulnerability appeared online. In this post, we’ll focus on this ongoing SAP RECON Vulnerability exploitation, with particular attention to how it’s been targeted in recent years.
Why the SAP RECON Vulnerability Was So Critical
Despite receiving a CVSS score of 10 out of 10, the true severity of RECON stemmed not only from its ease of exploitation but also from its widespread exposure to the internet. The vulnerability was found in “SAP Java NetWeaver,” a common layer used in many SAP solutions (e.g., Solution Manager, PI/PO, Enterprise Portal, CRM). Because these products are built on Java, they are often accessed via HTTP, making them vulnerable to internet exposure. One prime example is the Enterprise Portal, which is one of SAP’s most internet-facing solutions.
At a high level, exploiting RECON will give an attacker the power to create an admin user in a vulnerable system in an anonymous way, and thus have full control over the targeted system. The only requirement is to have access to the HTTP/s port of the targeted system. Onapsis RECON Scanner Tool provides a simple but effective way to determine if a system is vulnerable to RECON without actively exploiting it. Although it may seem reasonable to assume that this vulnerability is no longer a concern, the level of active exploitation might come as a surprise.
Exploitation of RECON: Then and Now
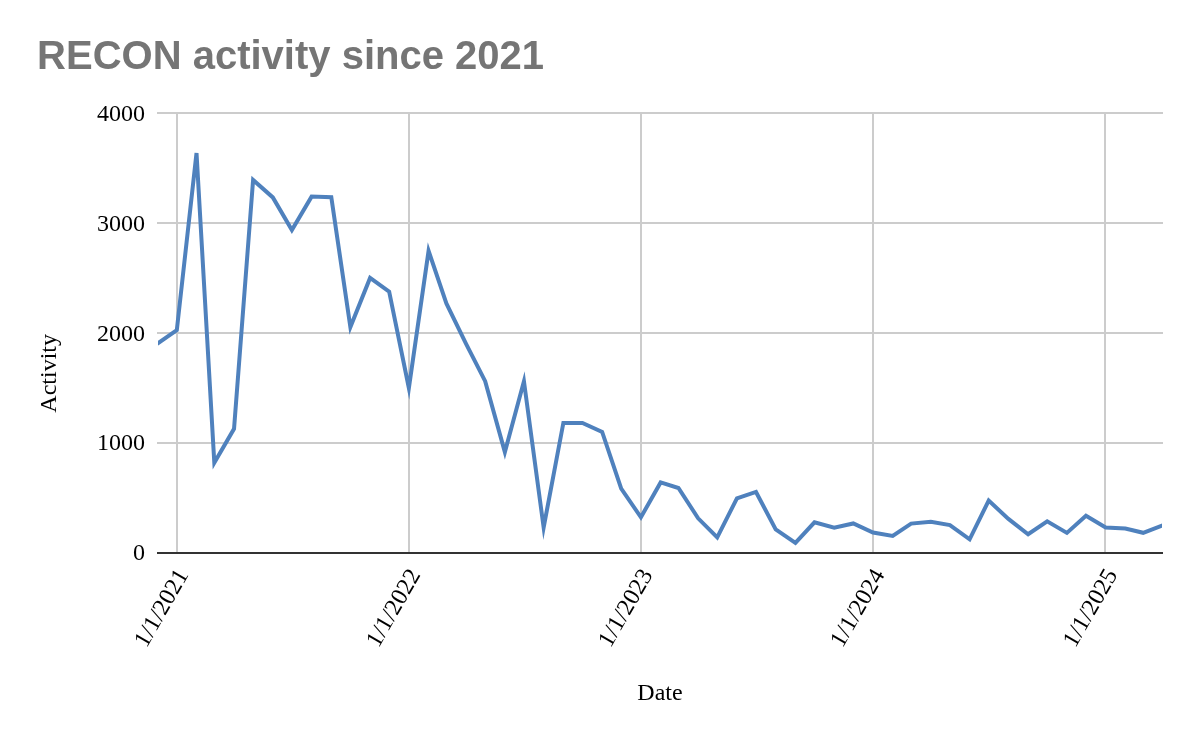
It’s remarkable to note that attackers are still exploiting this and even older vulnerabilities to compromise internet-facing systems. Just a few months ago, at Black Hat Europe 2024, Yvan Genuer, a Senior Security Researcher, demonstrated how attackers from various categories, including sophisticated groups and script kiddies, continue to leverage these vulnerabilities. For a deeper dive into this topic, check out our latest report named CH4TTER, which provides detailed insights and analysis. Nevertheless, the following chat provides a quick overview of how, despite the passage of years, attackers continue to exploit the same vulnerabilities—clearly with less intensity.
Lessons Learned and the Path Forward for SAP Security
Although the SAP RECON vulnerability was patched nearly five years ago, its continued exploitation highlights the persistent risk posed by outdated and exposed systems. Despite advancements in security, attackers—ranging from highly skilled groups to less sophisticated actors—continue to exploit these vulnerabilities, showing that older flaws still present valuable entry points. The ongoing exploitation of RECON underscores the critical importance of regular patching, proactive security measures, and constant vigilance. Moving forward, the lessons learned from incidents like this should drive improvements in the security posture of critical infrastructure systems, ensuring better protection against evolving threats.
FAQ
What is the SAP RECON Vulnerability?
The SAP RECON Vulnerability (CVE-2020-6287) is a critical flaw in SAP’s Java NetWeaver systems that allows unauthenticated attackers to create administrative users remotely. This vulnerability can lead to full system compromise if left unpatched.
Why is the SAP RECON Vulnerability still a risk today?
Even though SAP released a patch in 2020, many organizations have outdated, internet-facing SAP systems that remain exposed. As Onapsis research highlights, attackers continue to actively exploit this vulnerability years later, emphasizing the need for continuous patch management and monitoring.
How can organizations check if their SAP systems are vulnerable to RECON?
Organizations should use vulnerability scanning tools to assess exposure. Solutions like the Onapsis Platform allow businesses to automatically detect systems impacted by the SAP RECON Vulnerability without manual testing, enabling faster remediation.
What SAP products are most impacted by the SAP RECON Vulnerability?
Systems based on the SAP Java NetWeaver layer, such as SAP Solution Manager, PI/PO, Enterprise Portal, and CRM, are most affected. These products often have HTTP/S interfaces exposed to the internet, making them prime targets for attackers.
How quickly was the SAP RECON Vulnerability exploited after disclosure?
Exploits for the SAP RECON Vulnerability appeared online within 72 hours after the patch was released in July 2020. This rapid exploitation demonstrates how critical it is to apply SAP security patches immediately.
What steps should organizations take to mitigate SAP RECON Vulnerability risks?
Organizations must patch SAP systems immediately, restrict internet exposure wherever possible, continuously monitor for suspicious activity, and conduct regular SAP-specific security assessments with trusted solutions like those offered by Onapsis.
How does Onapsis help defend against vulnerabilities like SAP RECON?
Onapsis provides automated vulnerability management, real-time monitoring, and threat intelligence tailored for SAP environments. Their tools, including the Onapsis Platform, help organizations proactively defend against vulnerabilities like SAP RECON and maintain SAP system resilience.
What broader lessons does the SAP RECON Vulnerability teach about SAP cybersecurity?
The ongoing exploitation of SAP RECON highlights the importance of regular patching, proactive threat monitoring, minimizing system exposure, and having specialized SAP security strategies in place. Organizations must move from a reactive to a proactive security posture to protect critical business systems.

