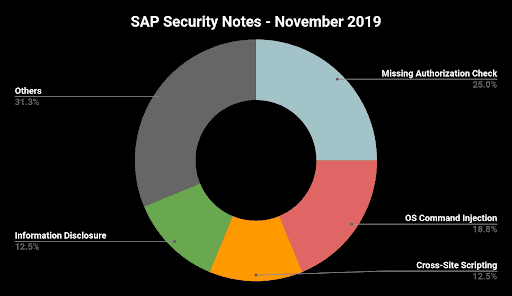
SAP Security Notes November 2019: Vulnerability in SAP Diagnostics Agent, keeps SAP Busy, New HotNews Released
Highlights of November SAP Security Notes analysis include:
- Second Update on SAP Diagnostics Agent issue published—Update addresses an additional attack scenario and replaces former published HotNews Notes
- HotNews Note #2622660 is back—New Google Chromium version released for usage in SAP Business Client
- 2 High Priority Notes published—Vulnerabilities in SAP Internet Pricing and Configurator (IPC) and SAP Business Objects BI Platform fixed
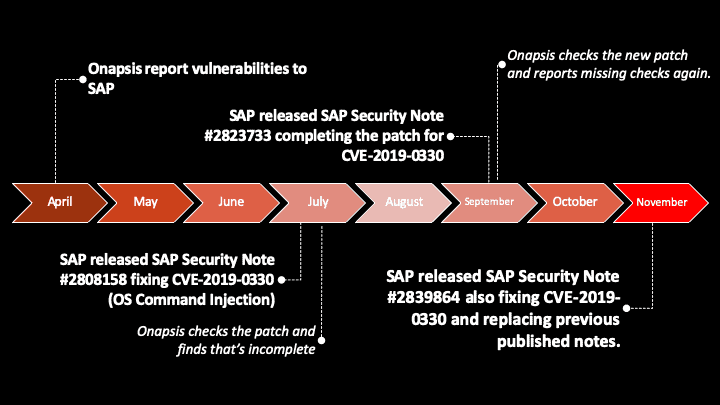
At first glance, readers of the new Security Notes, published on SAP’s November Patch day, might become a bit concerned because of 4 HotNews Notes on the list again, but a closer analysis quickly shows that the situation is less dramatic. SAP Security Notes #2808158 and #2823733 are updates for the vulnerability reported by Onapsis in SAP SMDAgent, that were only updated to confirm that now the whole issue is being solved in SAP Security Note #2839864. This replaces the remaining two HotNews Notes completely. These new notes cover additional attack scenarios that exploit this command injection vulnerability in SAP Diagnostics Agent, found by Onapsis Research Lab earlier this year. In our continuous effort to keep SAP customers protected, we have analyzed the previously released patches and worked with SAP to ensure the new patch covers some scenarios that weren’t in the initial notes.
The other HotNews is SAP Security Note #2622660, the continuously recurring (but nevertheless important) update announcing a new released Chromium version for SAP Business Client. Unfortunately, the newest released Chromium version is 77.0.3865, thus still containing the critical vulnerabilities reported by the Department of Homeland Security on October 31st. So, we can expect another update on note #2622660 very soon.
So, it can be said that there’s only two HotNews Notes to prioritize this month, not four. Keep reading for more details about SMDAgent vulnerability and another two notes to be highlighted—the only one rated as High Priority and another Medium Priority reported by Onapsis Research Labs.
SMD Agent Brief History
The SAP Solution Manager (SolMan) has a basic functionality to execute some specially crafted and limited commands on the agents through a specific SolMan component. These commands are checked against a whitelist to prevent arbitrary command executions. Onapsis Research Labs has previously found a bypass on one of the allowed commands to execute any other operating system command as the SolMan Admin user. This issue was initially reported in April and the first patch was released in July. Once we reviewed the first patch, we reported back to SAP to ensure they completed patching for other Operating Systems, as they did in September.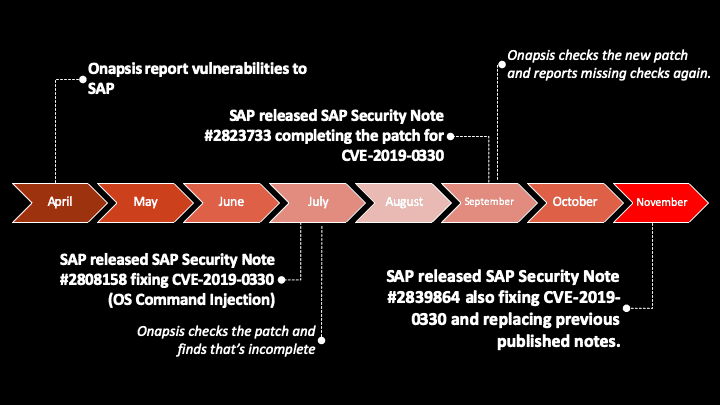
After that, our researchers have found new multiple bypasses over the defined whitelist for Linux/Unix systems, taking advantage of other pre-crafted commands allowed, with several payloads and ways to exploit this vulnerability. This could also allow an attacker to delete, modify or even execute arbitrary commands on the agent. Based on this, SAP has released this month a new note covering all reported scenarios and allowing customers that didn’t patch before only to apply this last released note (#2839864).
SAP has published new patches for Support Packages 6 to 9, and also provides manual steps for patching for older versions. With the latest patch, it is now the customer’s responsibility to maintain commands whitelist, and after applying the patch some diagnostic tasks may stop working since SAP is now replacing the file with a limited amount of commands allowed. It is also the customer’s responsibility to decide which OS commands should be allowed, and you may need to add some of them manually if you have been using it.
As was mentioned in our September SAP Notes Blog Post, although many SolMan admins have admin privileges in other SAP systems, certain scenarios may allow an escalation of privileges to those who don’t, so if these scenarios pertain to you, increasing the urgency to patch should be a priority since it may be one of the most critical patches to pay attention to this year.
High Priority Notes for Customers Using SAP Internet Pricing Configurator and for SAP Business Objects Customers
SAP Security Note #239393, CVSS score of 7.1, addresses a vulnerability in SAP Internet Pricing Configurator (IPC) that can also often be found in customer code. Some RFC enabled function modules were only protected by authority checks on object S_RFC. Due to the complex nature of SAP installations, there usually exists a significant number of users with S_RFC * privileges and thus they automatically have access to all remote enabled function modules, that do not contain explicit authorization checks related to the business context of the function module. SAP has fixed this issue for a set of important IPC-function modules through the introduction of a new switchable authorization scenario, thus allowing customers a smooth transition to more detailed and context related authorization checks.
SAP Security Note #2814007, also rated with CVSS score 7.1, describes the introduction of additional XML validation in SAP Business Objects Business Intelligence Platform as XML documents from untrusted sources were not correctly filtered for malicious content in some specific workflows. Among others, insufficient XML validation can lead to information disclosure as well as to complete system outages due to denial-of-service attacks. Fix for eCatt Service in SAP NW AS JAVA, initiated by Onapsis Research Labs
Fix for eCatt Service in SAP NW AS JAVA, initiated by Onapsis Research Labs
SAP Security Note #2835226, rated with Medium Priority, was also triggered by the Onapsis Research Labs. Without that fix, attackers could exploit the service /ecatt/ecattping of the ECATT framework in order to gather information that could be used for further exploits and attacks. This is caused by a missing authorization check in the affected service. As the provided patch introduces the missing authorization check, it is necessary to create the required role and assign it to the respective users. In general, it is recommended to use the ECATT framework only in test systems.
Summary & Conclusions
With one of (de facto) two HotNews Notes and one Medium Priority Note, the Onapsis Research Labs has once more significantly contributed to making SAP more secure. This underlines our mission to not only prevent our customers from being attacked through the exploitation of known, but unfixed, vulnerabilities in SAP. We also strongly support SAP in always staying one step ahead of potential hackers and data thieves.
As always, the Onapsis Research Labs is already working to update The Onapsis Platform to incorporate these newly published vulnerabilities into the product so that our customers can check missing notes during their security assessments.
For more information about the latest SAP security issues and to stay in tune with our continuous efforts to share knowledge with the security community, subscribe to our monthly Defender’s Digest Onapsis Newsletter.
