Year in Review: Risk & The Importance of SAP Application Protection

If there is one thing that stands out from our Onapsis Research Labs it is the fact that we are passionate about SAP security. While many defenders are passionate, I would go further to say that this is our calling. It takes special individuals and a collective team to band together to create a safer global economy. We play our part with vulnerability research and threat intelligence, working directly with SAP to patch vulnerabilities and ensure comprehensive SAP application protection. Let me restate that:
As a research team, we truly love helping secure SAP for the greater good.
I recently had the opportunity to sit down with JP, our CTO and Co-founder, to discuss Onapsis Research Labs Year in Review. One of our most popular discussions every year, we kick off first by demonstrating why we’re even in the position to do such a webinar, a sort of display of our ‘street cred’:
- Continually invited to the world’s leading, and epic, security conferences such as Black Hat, DefCon, RSA, Troopers (thank you by the way!)
- Onapsis Research Labs has discovered over 1,000 zero-day vulnerabilities within ERP applications
- 6 of these vulnerabilities warranted CISA issuing Critical Alerts due to their impact
The Importance of SAP Applications
Next up, JP and I start to dive into why SAP is pivotal for global trade, commerce, and our greater good north star. For instance, SAP’s website states:
98 of the 100 largest companies in the world are SAP customers

Many that are new to the world of SAP and ERP Security might be surprised at the volume of companies that rely on SAP applications. The sheer number is not only staggering, but also the scale–SAP customers generate 84% of the total global commerce. In fact, these applications are so critical to our global economy, CISA has added more than 10 SAP vulnerabilities to its Known Exploited Vulnerabilities (KEV) Catalog since 2021. Many CVEs from SAP and Onapsis joint research–like vulnerabilities addressed with our ICMAD research–have been added and most recently, CVE-2019-0344 was added to the KEV in November 2024.
Threat Actors Targeting SAP Applications
Unfortunately, the criminal underworld already knows this as well. We show that in the past two years, 64% of ERP Systems have been breached. And that downtime impacting SAP due to security incidents averaged businesses over $50,000 per hour.
Now we have to ask ourselves, why is SAP being targeted more than ever? Aside from a wide spectrum of threat actors tuning their instruments towards businesses running SAP, our research has discovered criminals are exploiting SAP vulnerabilities for:
- Executing Ransomware
- 400% Increase in Ransomware incidents from 2021 – 2023 that include SAP Data
- Criminals find the business critical data is highly valuable
- Performing Financial Fraud
- Threat Actors such as FIN13 (Elephant Beetle) stole $30,000,000.
- Miscreants are exploiting payment systems to steal money
- Accessing SAP Information
- As highlighted by CISA
- Taking Advantage of the Infrastructure
- To perform cryptocurrency mining
- To deploy malicious software
Exploiting SAP Vulnerabilities
The thing is, it is not only the data or the server that threat actors are interested in, they also want to purchase the highly sought after exploits of SAP vulnerabilities. Here is an example of a remote code execution exploiting SAP bounty seeking $250,000 that JP and I discuss in detail:

Now, patching can be time consuming and manual without the right solutions, so patching right away isn’t always feasible. But, according to our research last year, you NEED to make patching a priority. This report detailed a real world attack by a threat actor, showing something we have written about before:
SAP systems are attacked and exploited quickly.
Here is a timeline of one such attack Onapsis Research Labs analyzed in 2024:
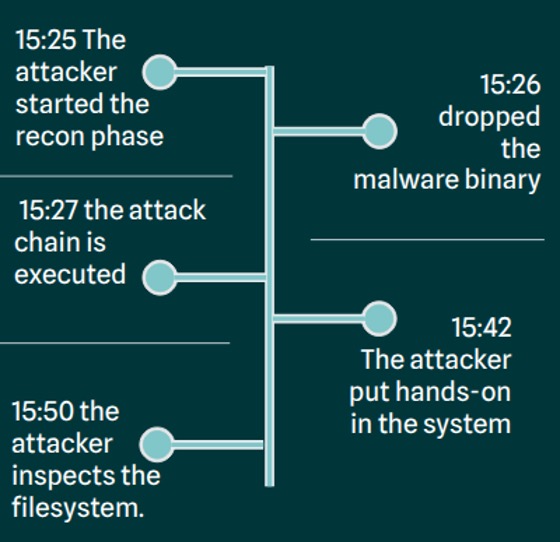
The attacker utilized a well known SAP vulnerability that CISA highlights as active in its KEV catalog, CVE-2010-5326. Moral of the story? Even if you believe your systems are safe and secure–especially because they are behind layered defense protections–criminals can and are getting in. We cannot stress enough, even with zero-day, pre-patch protection: patch SAP, patch it often, and patch it quickly.
Risk & Patching SAP Applications
To help organizations understand the risk to SAP as a risk to the business, JP and I also often point to the following Decision Tree:
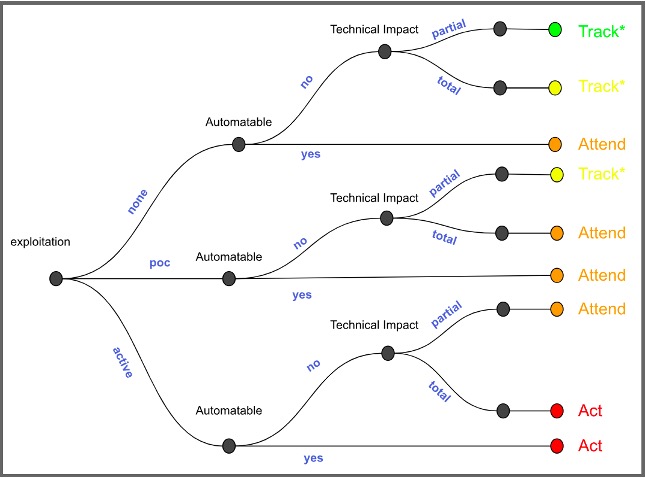
Yes, organizations need to patch SAP quickly. Even if your SAP systems are closed to the public, on Prem, cloud, and hybrid systems are all pieced together using technologies from various supply chain vendors. This makes them connected and increases your attack surface.
Recently, CISA issued an advisory about chaining vulnerabilities, especially those that are end of life and no longer supported, yet businesses are running them. Your SAP systems might be locked down tight from external access, but consider other supply chain technologies that must also be patched, updated, upgraded or replaced. Any of those technologies could be exploited–rendering your external layered defense protecting SAP bypassable.
Ensuring SAP Application Protection
Now that you understand the importance of SAP and that SAP applications are being targeted more than ever, what can you do?
- Stay updated with SAP Security Notes
- Ensure your team is up-to-date with patches, using automation where possible
- Invest in solutions that provide detailed business impact of SAP vulnerabilities
Explore solutions like Onapsis Defend that offer zero-day, pre-patch protection to ensure comprehensive SAP application protection.

