Revisiting CH4TTER: Takeaways One Year After this SAP Threat Landscape Report

It’s been exactly one year since we released our first ever report on threat actors discussing SAP. In conjunction with Flashpoint, this report highlighted trends in the SAP threat landscape. CISA, SAP and Onapsis have been for years warning businesses to patch and stay secure, along with best practices such as monitoring and pentesting their landscapes. We’ve been warning because of the threats to businesses running vulnerable SAP systems. This data supports from the underground what we have been upfront about. The biggest insights are that executives and practitioners are more receptive than ever to actionable threat intelligence and a keen understanding of their actual SAP security coverage.
We wanted to address our key takeaways a year removed from this research:
The Industry is Hungry for this Intelligence
You don’t know what you don’t know. And although we had been communicating to the public about these threats, it wasn’t until the CH4TTER report that we had found chords that resonated with businesses. Perhaps it’s “just in time” or “just the right time” for the message, in the way it was put together, to be received by willing and able executives and practitioners.
Across the board, we received feedback that our research was extremely helpful for our customers to not only understand risk to their SAP applications, but articulate that risk to their board for investment. Particularly the charts around the rise of ransomware as well as the insight into the anatomy of the C2 botnet attack. In general, validation that SAP systems are also exploited as attack vectors is also something our customers shared was helpful in their conversations with their leadership and board teams.
The intelligence that practitioners found that was most actionable for them, they were able to check their landscapes and also ensure they had proper monitoring in place for attacks. The following table comes from the original CH4TTER analysis:
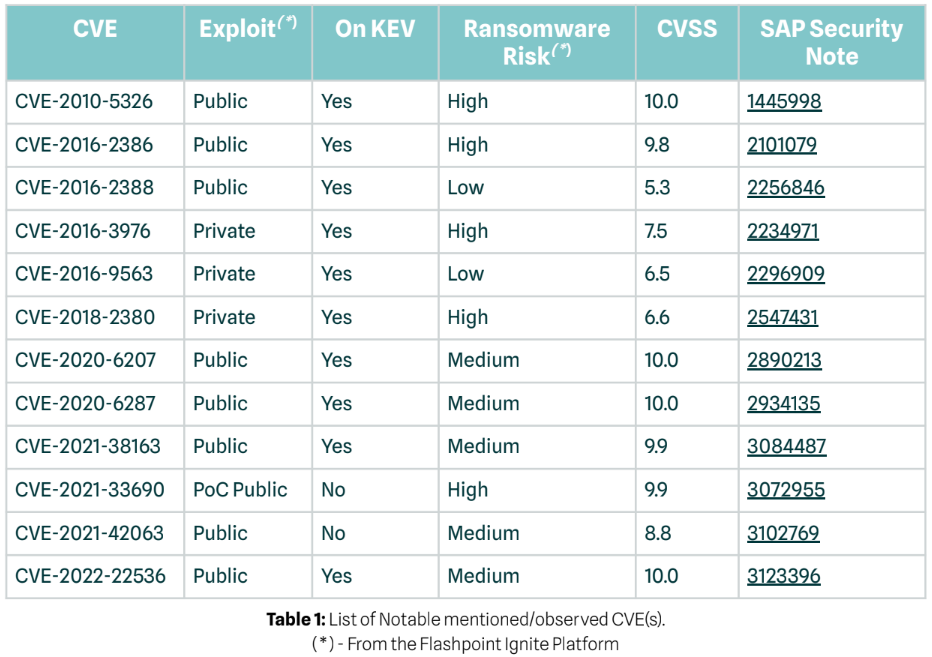
The purpose of this table is to illustrate that CISA recognizes the importance of broad sweeping awareness around these SAP vulnerabilities. We want to avoid the perception that if you patch all of these vulnerabilities in the table above, you are secure. Unfortunately, it’s not as simple as that. Threats to SAP applications are active, dynamic, and defenders need to remain vigilant with current and new threats as they occur. We dive into such an example in the next section, where we can add to this list of current and active attacks against SAP.
Threat Actors Continue to Exploit SAP Vulnerabilities
Consistently since the creation of the Catalog of Known Exploited Vulnerabilities (KEV), multiple vulnerabilities impacting SAP were added to it. We continue to see more attention being paid to this area of security.Recently, CVE-2017-12637 was added to CISA’s KEV in March 2025. This reinforces the threat intelligence chart shown above, that even older SAP vulnerabilities are still targeted by attackers today.
Understanding Attacks to SAP Applications is Helping Organizations Defend Themselves
Last year, the Onapsis Research Labs released the Anatomy of an Attack Research, which provides an understanding of how threat actors are exploiting vulnerabilities and this can inform organizations to better protect their SAP applications. We have warned about traditional targets such as finances and PII, in this scenario the attackers abused the SAP host server to launch attacks on other businesses. This allows the attackers to remain hidden from their target during the attack and instead put the blame on a legitimate business.
Downtime & Ransomware Affecting SAP Applications Impacts Organizations
The impacts of SAP application downtime or, even worse, a ransomware attack that impacts your SAP systems is showing up more often in our news feeds. A recent example is a company filing for bankruptcy, citing a ransomware attack impacting their SAP applications was partially responsible. As seasoned researchers, as well as incident responders and pentesters, we are fully aware of the impact to businesses when their SAP systems are compromised. This past year, we’ve seen one of the largest public impacts to a compromised SAP system: Stoli’s bankruptcy.
What can we do about it?
Enlist Help for Pentesting
Having helped many organizations over the last few years, we have come to learn that there is a huge discrepancy for what a company thinks is secure and what their true SAP security posture looks like.
Interesting data points come from the Penetration Tests (pentests), as we are able to share some anonymized high-level insights learned from the pentests we performed over in the past few years. Here are a few things that are helpful to keep in mind to inform your SAP security strategy:
- Onapsis Research Labs are able to achieve full compromise in nearly every organization on the first try.
- Executives are surprised by the exposure and vulnerability levels of their SAP landscape after presenting pentest results.
- The more organizations are purposeful about securing their SAP landscape, the more fortified the customer landscape becomes. This means investing in SAP cybersecurity.
- Annual pentests are like an annual physical–checking-in can never hurt, only help.
Cybersecurity for SAP from SAP Press
During SAPinsider, we announced the first book solely focused on SAP cybersecurity: Cybersecurity for SAP. We have never had so many positive conversations with customers and industry leaders that this has been a gap for so long. This book is the definitive answer for your SAP cybersecurity questions with lessons from industry leaders JP Perez-Etchegoyen and Gaurav Singh. If this piques your interest, enter to win a free copy here.
As organizations face new threats daily, we are committed to continuing our research to help harden SAP application defenses for the betterment of the global economy.


