Why the RECON Vulnerability Is a Before and After for SAP Cybersecurity Introduction
Key takeaways:
- RECON is a critical vulnerability affecting thousands of internet-facing applications, as well as internal systems
- With a CVSS score of 10.0, the impact of exploitation is critical to the business and that’s why multiple international CERTs alerted organizations to it
- OS tools are available to test for the vulnerability as well as indicators of compromise
Critical vulnerabilities are discovered, reported and patched continuously. It is a known risk that organizations have to continuously manage. Now, when it comes to the organization’s crown jewels, vulnerabilities can pose additional risks and have to be treated even more seriously, especially the critical ones.
Over the past few years, a broader awareness of the need for cybersecurity controls around SAP applications has been driving attention to vulnerabilities, generating a positive reaction from the SAP BASIS teams who address these risks, but also a negative reaction on the threat actors who are increasingly focused on these vulnerabilities.
More Important Than Ever
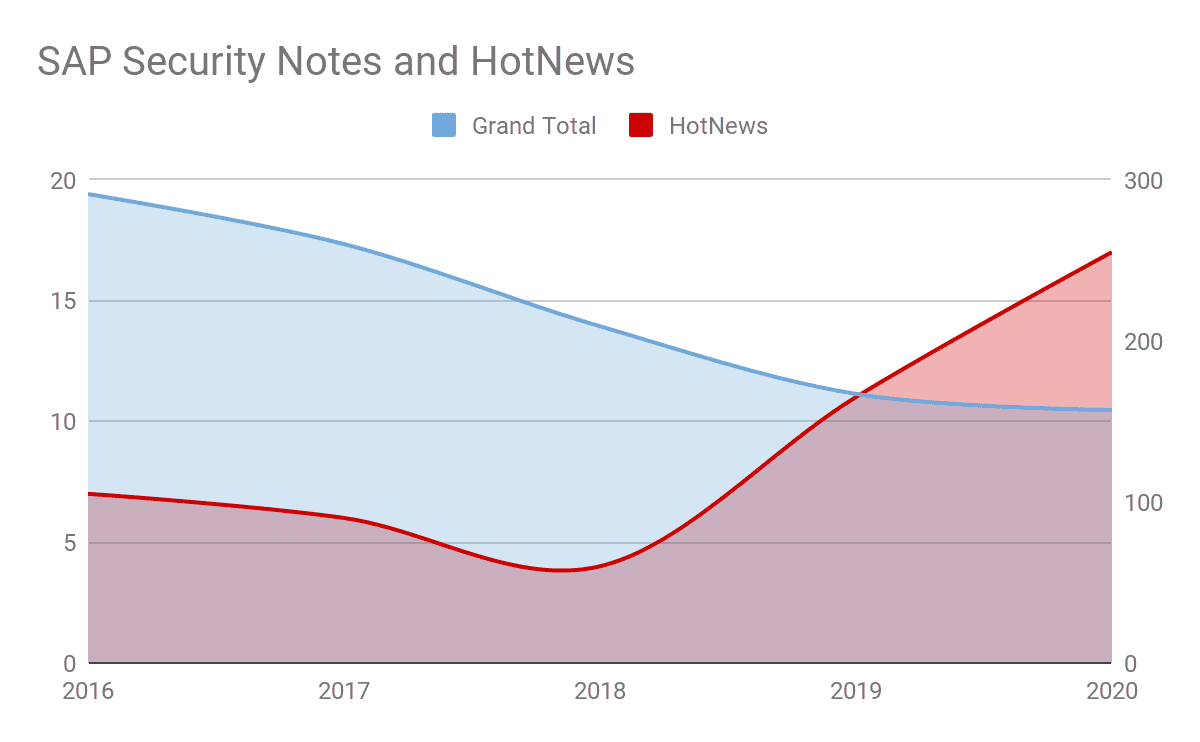
The overall number of SAP Security Notes has been slowly decreasing over the years, due to strategies SAP has implemented to simplify adoption of patches (for example, multiple vulnerabilities fixed through the same patch), but there have been an increasing number of patches addressing critical vulnerabilities (HotNews in the SAP world).
As seen in Figure 1, the evolution of SAP Security Notes shows a decrease in the total number of patches as well as an increase on the HotNews over the past 5 years. This data does not consider the potential upcoming SAP Security Notes or HotNews in the last 4 months of 2020, which could change the trend too.
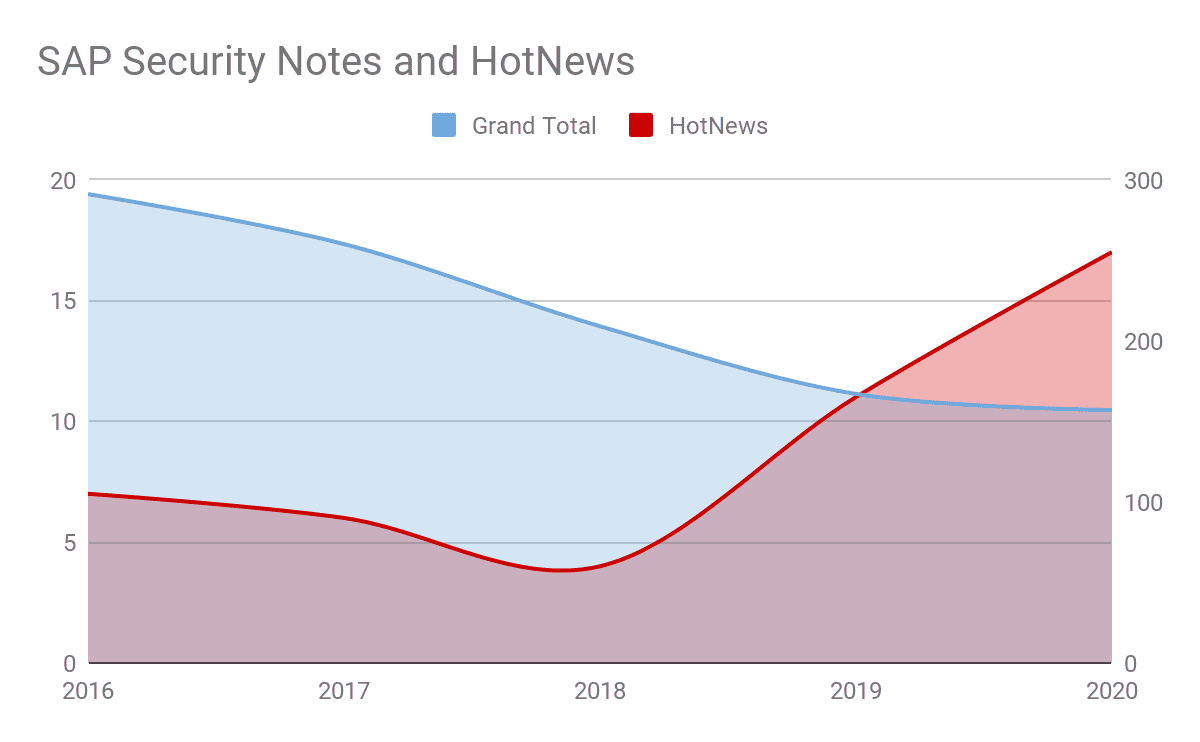
This data point tells us that SAP strategies are helping organizations better consume the patches, but that there is increasing attention and scrutiny from the research community on SAP technology, leading to the discovery of multiple critical vulnerabilities.
The RECON Vulnerability
We are going to cover a very unique vulnerability, the CVE-2020-6287 (also known as the RECON vulnerability), due to the different aspects that make this vulnerability special from other vulnerabilities that were seen before:
- CVSS: 10.0 (Full impact)
- Remotely exploitable through the network
- Exploitable through HTTP(s) protocols
- No privileges required (No user) to exploit the vulnerability
- Ability to perform pretty much anything on the target system, including creating high-privileged users and executing OS commands
- Due to the HTTP-based nature of the vulnerability, a large footprint of internet-facing applications are exposed
A Global Risk
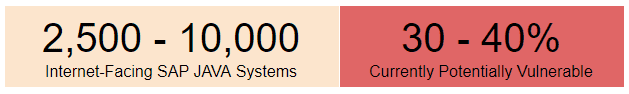
By using internet-facing search engines, it was possible to identify the number of exposed systems at the date of patch release. Different search engines provide different estimations, as it depends on the number of ports that are scanned and the techniques that are being used to identify SAP Netweaver-based applications. All in all, anywhere from 2,500 up to potentially 10,000 internet-facing systems were exposed to RECON at the date of the release of the patch.
Considering those numbers and that approximately 30% to 40% of the systems could still be vulnerable (based on estimations of diverse samples), that provides an enormous attack surface and risk.
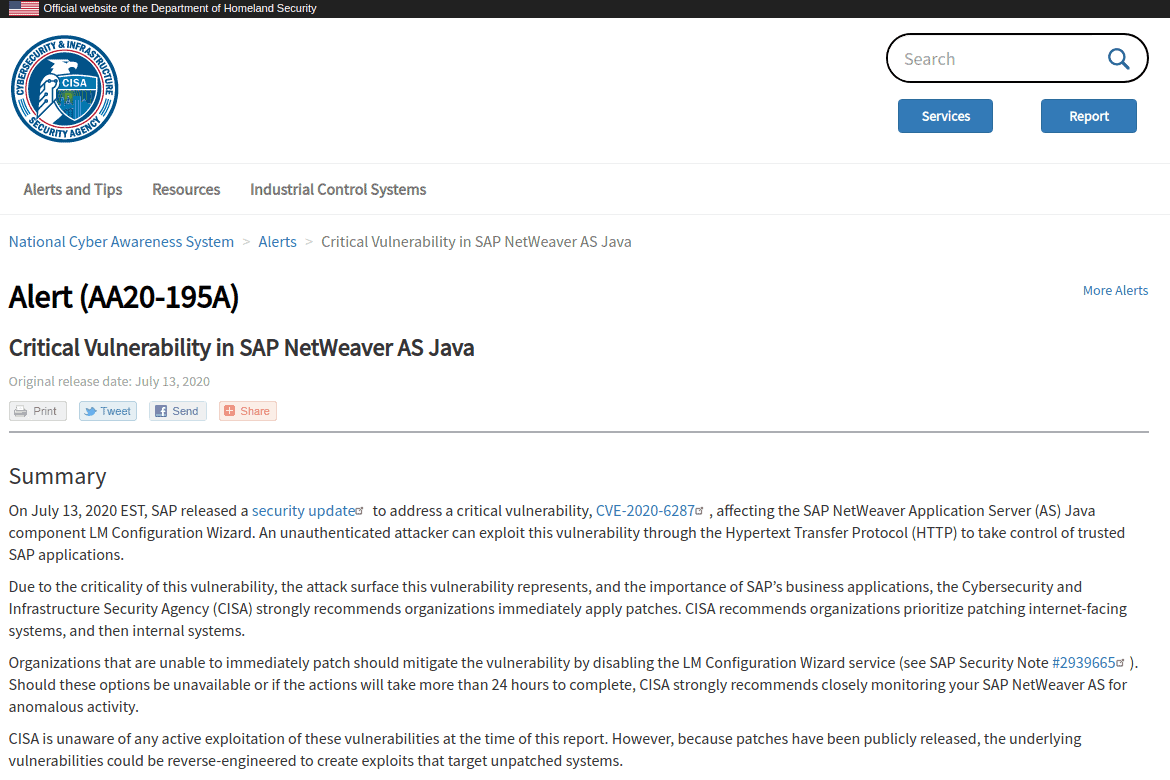
At the same time of the release of the patch, and because of how critical this vulnerability was and the potential attack surface over the Internet, DHS-CISA along with many other global organizations issued CERT (Computer Emergency Response Team) Alerts warning organizations of the need to address RECON vulnerability. This alert was raised by over a dozen of CERTs across the globe for countries such as the U.S, Germany and France, to name a few.
The Onapsis Contribution
Even though Onapsis customers were protected when the patch was released, we understand how critical this vulnerability is for organizations and how difficult it is to understand if applications are exposed to it or not. Because of that, Onapsis released the INSTANT RECON free service and open source tool, which allows SAP customers to scan systems online by analyzing SAP logs and checking internet-facing systems for the RECON vulnerability. It also provides the option to run the tool locally for scanning all SAP systems across their internal networks. Besides applying the official SAP patches, Onapsis strongly recommends that all SAP customers run this service or tool immediately to determine the potential threat exposure and vulnerable systems that must be secured, in order to keep SAP systems and business processes protected and in compliance with important regulatory mandates.
Free access or download the INSTANT RECON service and tool here:
Conclusion
Mission-critical applications host the crown jewels of your organization. Due to the impact and criticality of the RECON vulnerability, combined with an increase of Interest from researchers (and threat actors as covered in other articles), these applications demand more protection than ever.
The RECON Vulnerability Content Series
In July, SAP issued patches for the RECON vulnerability after being identified and disclosed to SAP by the Onapsis Research Labs. Because of its severity and the amount of internet-exposed SAP systems potentially vulnerable, the DHS-CISA, along with many other global organizations, issued CERT Alerts warning organizations of the criticality of the RECON vulnerability. Both SAP and Onapsis urged organizations using SAP applications to apply the patches immediately. In the days following the release of the patches for RECON, the Onapsis Research Labs and other security/threat intelligence organizations and researchers witnessed and reported rapid threat activity including scanning for vulnerable systems and ultimately weaponized exploit code posted publicly. This content is part of a coordinated effort with threat intelligence experts, researchers and organizations to provide further insight, intelligence and actions you should take to ensure your organization is protected from the RECON vulnerability.
Links to each part of this blog series can be found below:
- Part 1: The Vulnerability @Onapsis Blog
- Part 2: The Mitigations @SAP Community Network
- Part 3: Relevance to the Cloud @Cloud Security Alliance
- Part 4: Threat Intelligence @DigitalShadows
- Part 5: Active Scanning @Stratosphere Labs
- Part 6: Vulnerability Threat Context @Blueliv
- Part 7: Active Exploitation @Onapsis Research Labs
- Part 8: Compliance @The Institute of Internal Auditors
- Part 9: Data Privacy @Radical Compliance
- Part 10: Programmatic Approach @Linkedin


