Protecting Oracle E-Business Suite: Reducing the Attack Surface
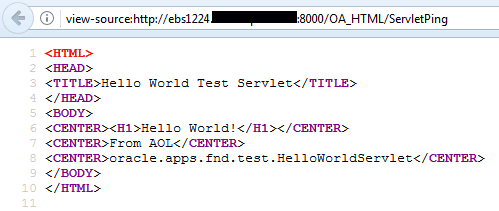
This is the fourth consecutive blog post in our series on how to make Oracle E-Business Suite more secure. In this post, we will focus on reducing the attack surface – something that is a critical component for any successful information security strategy. The more you can reduce the components that are exposed to attackers (and to vulnerabilities), the more you can focus on keeping your exposed systems secure. In Oracle E-Business Suite, this feature is called Allowed JSPs and Allowed resources. In a real attack scenario, the first step for an attacker would be to understand the architecture of the target, and which of these systems is exposed. After the initial setup of Oracle E-Business Suite, all resources and modules will be available, there is no limitation during installation. By default, the exposed components are more than 7800 JSP (Java Server Pages), media files, servlets, forms, business services, java classes called by the some JSP’s and more. The main risk in having these components exposed is that an attacker could use the code to find vulnerabilities and exploit them. In Oracle E-Business Suite, an attacker can use any exposed URL and read the exposed code with right click and then click in View Page Source:
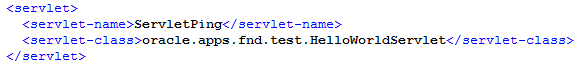
Since a web.xml definition with the s ervlet definition exists in Oracle E-Business Suite exists, an attacker can find the Java classes which implement the servlet functionality in a lab Oracle E-Business Suite:
Given the previous information, an attacker could use all the attack surface to exploit known vulnerabilities or discover new vulnerabilities and exploit them.
Reducing the Attack Surface
As previously shown there are a lot of source code implementations in each service and an attacker could use them to get control of the system. Also, it’s not common for an organization to use all the features in Oracle E-Business Suite, therefore making it a responsible practice to remove the unnecessary JSPs (which as mentioned, are more than 7800). Despite taking proactive steps to protect your infrastructure, it is a bad scenario when an attacker can exploit your systems through some application that you are not even using it. It could be easily solved by disabling this exposure (much easier than patching). The Allowed JSPs feature reduces the attack surface of Oracle E-Business Suite by enabling the creation of a whitelist of JSPs that are allowed access to Oracle E-Business Suite. This feature is only available in versions R12.2. In release 12.2.6 with Patch 24737426:R12.FND.C, the Allowed JSPs feature has been enhanced and is now called Allowed Resources. The Allowed Resources feature reduces the attack surface of Oracle E-Business Suite by enabling the creation of a whitelist of resources, JavaServer Pages (JSPs) and servlets, that are allowed access to Oracle E-Business Suite. As part of the Oracle E-Business Suite Release 12.2.6 update pack (RUP), the Allowed resources feature is ON by default and it is necessary to enable it manually in previous versions. There are only two levels of protection that exist:
- 1. Using it with the shipped configuration provides some level of protection, for minimal effort.
- 2.You can create and use customized whitelists to match your family and product usage. This option is recommended for the best reduction in attack surface.
Enabling Allowed JSPs Feature
The basic strategy for deploying the Allowed JSPs feature starts by evaluating product family usage: you cannot move forward without better knowledge of how do you use the product. After that, you should cross-check restricted JSPs against the access_log (all requests processed byOracle HTTP Server are logged in the access_log file). Finally, ensure allowed JSPs feature is enabled and add custom JSPs as required. Finally, you can continue refining the list after properly monitoring the usage. The main configuration files for this feature are:
- $OA_HTML/WEB-INF/web.xml
- $FND_TOP/secure/allowed_jsps.conf (master configuration file)
- $FND_TOP/secure/allowed_jsps_.conf
- $FND_TOP/secure/allowed_jsps__.conf
Let us take a deeper look to understand how it works.

This file includes a filter to read the Allowed JSPs configuration file and set additional parameters for the configuration. The MASTER_FILE parameter defines the master configuration file name. The default name is $FND_TOP/secure/allowed_jsps.conf. Here’s an example from $OA_HTML/WEB-INF/web.xml:

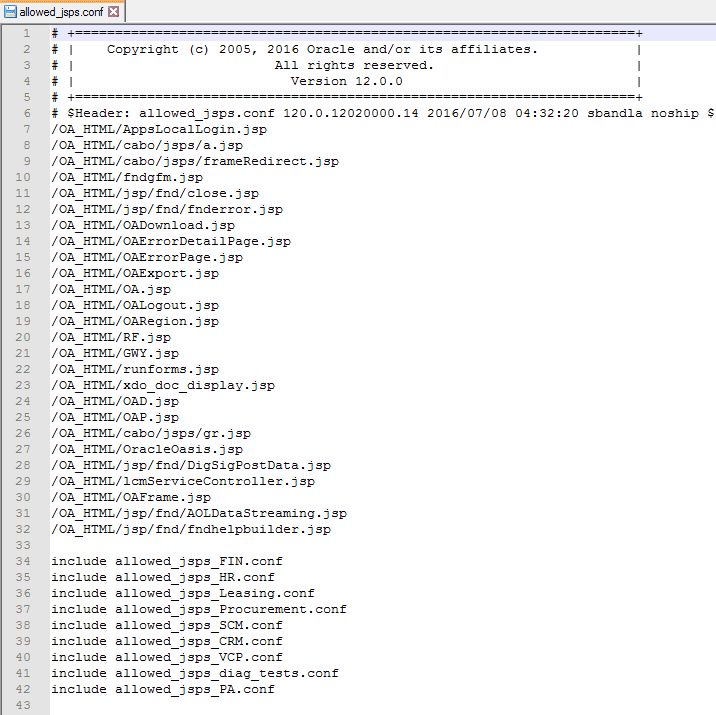
File contents include common JSPs for Oracle E-Business Suite, and product family configuration files (as include files). The following is an example of allowed_jsps.conf file. In this example file you can realize that at the end there are all the include files like allowed_jsps_FIN.conf, allowed_jsps_HR.conf, and more files.

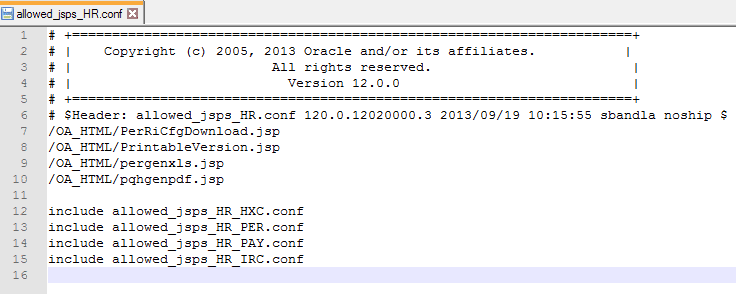
File contents include common JSPs for Oracle E-Business Suite product families, and JSPs that are accessible for a product family. The following is an example of HR jsp family:

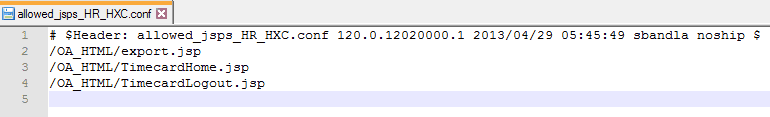
The following is an example of HR jsp family and HXC product:
Creating a Custom Configuration File
You can also create custom configuration files if you want to go deeper on the analysis and have a more detailed configuration. For that purpose, you should create a new custom configuration file (like allowed_jsps_CUSTOM.conf), add it to the custom configuration file (for example /OA_HTML/MyCustomPage.jsp) and, finally, add the corresponding entry in the MASTER_FILE, allowed_jsps.conf. There are three levels of granularity that exist for this feature of Allowed JSP:
- If you are not using any products in a particular product family, comment out that family in the MASTER_FILE.
- To restrict access at the product level, comment out the appropriate product-level JSPs.
- To restrict access at the individual JSP level, comment out the JSPs in question.
Activate Allowed JSPs
Once you have everything properly configured, you should activate this feature. To do so, the profile option ‘Allow Unrestricted JSP Access’ (FND_SEC_ALLOW_JSP_UNRESTRICTED_ACCESS) allows unrestricted access or restricted access to be set. The values for this parameters could be:
- Set as site or server level.
- The value “Yes” allow unrestricted access, which is the unsecure configuration.
- The value of “No” or “Null” enables restricted access if the JSP servlet filter is configured.
There are more features to reduce the attack surface, for example “Allowed redirects” and “Cookie Domain Scoping”. We will be publishing additional posts regarding this feature and will explain how to build a more secure Oracle E-Business Suite. The attack surface topic is a very important task for the security of Oracle E-Business Suite installations. Prior to version 12.2.6 of Oracle E-Business Suite, the system comes with all the services enabled by default. This default configuration is not good for organizations because it exposes the system to a lot of services that the company probably doesn’t use. It is very important to understand which services the business needs and to enable only those services, not more and not less, accordingly to the rule of least privilege.

