Preparing Your Business-Critical Applications for a Cloud Migration
The cloud trend is unstoppable. More and more organizations are moving their on-premises business-critical applications to the cloud and starting to use native cloud solutions like SuccessFactors, Salesforce or Workday.
Obviously, companies have different reasons to move to the cloud. They may want to become more agile in terms of new business functionalities, support new business growth opportunities or simply reduce their overall IT costs. All reasons are justified, but one question in times of data privacy, compliance and worldwide cyber threat is, ”how can I securely move into the cloud and ensure secure operations in the cloud?”
Is My Cloud Provider Responsible for All Security Related Issues?
To be clear, just because corporations move into the cloud doesn’t mean they are also able to shift all security-related responsibilities to the cloud provider. Interestingly, that is one of the most common misconceptions, when it comes to understanding SAP cloud security.
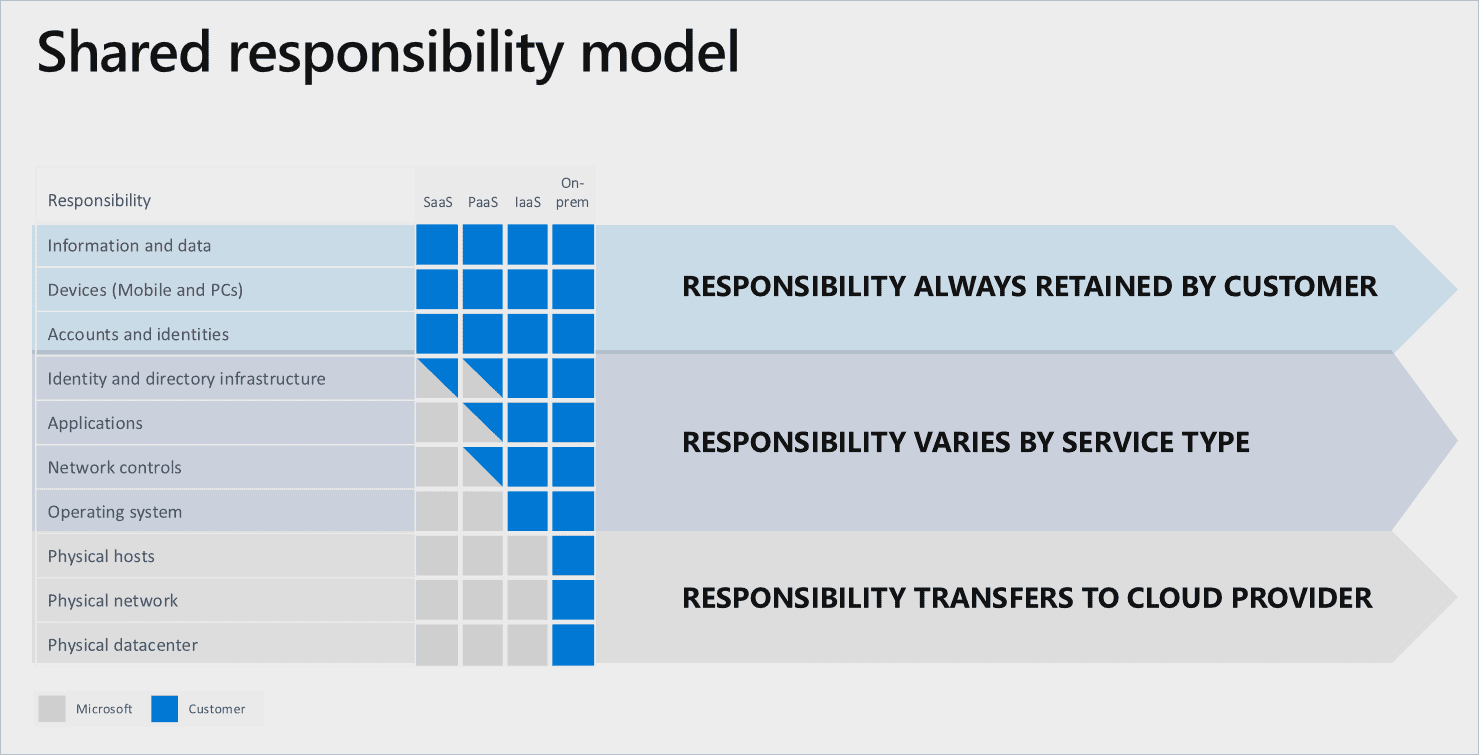
Microsoft has released a very nice and easy to understand shared responsibility model. Obviously, your responsibilities as a customer depend on the cloud deployment you have chosen.
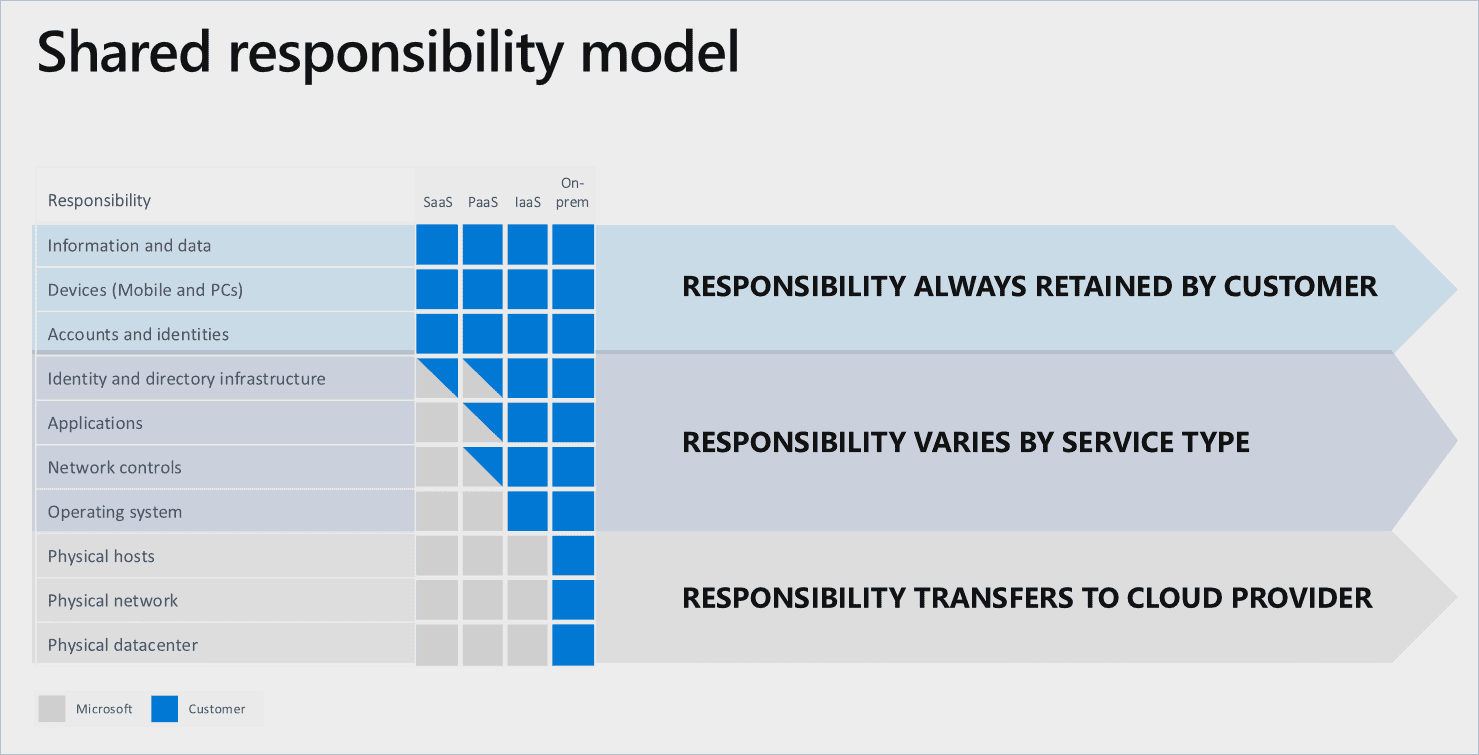
For applications and network controls, for example, the responsibility is transferred to the cloud provider, whenever you are in a Software-as-a-Service scenario.
Areas like physical hosting and physical networks are also in the responsibility of the cloud provider, regardless of which cloud scenario (SaaS, PaaS, IaaS) you are in.
Now let’s take a look at those things that are in your area of responsibility.
You are responsible for:
- Your business processes, data, devices, accounts and identities, no matter in which cloud deployment scenario you’re in.
- Adhering to the law and your own internal compliance mandates, and this is crucial to understand. Just because you’re using a cloud service doesn’t necessarily mean that you don’t have to take care of basic security controls.
Is It More Secure to Use Cloud Services Instead of On-Premises Applications?
The short answer is that you’re not automatically more secure just by using cloud services. You still have many attack vectors. For instance:
1. Your Cloud is Your DMZ
When acting on-premises only, you usually have a “Demilitarized Zone” (short DMZ). The DMZ comprises applications or services such as web servers, mail servers, authentication servers or application gateways. Only these services can be accessed by users from the Internet. Because the DMZ is separated from the internal company network, external users can’t access internal resources. The private network remains protected from attacks via the Internet.
If you now move your critical data into the cloud, the cloud becomes your DMZ. Anybody who has access to your cloud service can do harmful things with your data.
2. Account Hijacking
Everybody has heard of Phishing or hacking accounts by simple password guessing. Having business applications not within your local networks opens up a completely new attack vector from the outside
3. Insecure APIs
Cloud vendors expose a set of interfaces or APIs that customers use to manage and interact with the cloud service.
Obviously, these APIs need to be secured with basics like authentication and access control. If they’re not secured, you are vulnerable to attack.
4. Denial of Service
It’s hard to protect against this one. Hackers seek to make your service unavailable. You can invest a lot of money on securing against Denial of Service attacks, but it seems like attackers always find new ways to force a system to go down.
5. Insider Threats
Insider threats are equally dangerous within on-premises landscapes or in the cloud. The question is, are all activities and events being logged in the cloud? Does the vendor offer even logging capabilities to the full extent so that you are able to detect fraudulent operations?
6. Software and Frameworks
And of course, the vulnerabilities of cloud applications and platforms themselves. Are they always patched? Is anybody regularly pentesting it? Are the frameworks and open source tools maintained and secured? You often have to trust that your vendor is keeping track of all these things.
What Can You Do Now, and Where Should You Start?
To have a full picture of what matters most for cloud security, you can follow the so-called cyber framework, given by the National Institute of Standards and Technology. In a nutshell, the cyber framework provides a set of activities to manage cybersecurity risks. For this framework, you need to implement these five capabilities:
- Identify: you are able to name your business-critical applications, whether they are on-premises or in the cloud. Those applications need to be prioritized for your cybersecurity efforts.
- Protect: you have the right safeguards in place for your business-critical applications, for example a proper Access Control.
- Detect: you are able to recognize attacks and anomalies. Therefore you or your cloud vendor needs the right tools and processes in place to detect attacks.
- Respond: you or your cloud vendor can appropriately respond to an incident by for example mitigation and improvements.
- Recover: you are able to recover and repair any capabilities or services that were impaired due to a cybersecurity event.
Recommendations on How to Start Mastering Cloud Security
There are a lot of different ways to facilitate and implement the cyber framework, for example:
- By using additional cloud access security brokers, that help you to monitor all activities and enforce security policies,
- Zoning, respectively IP Whitelisting, so only predefined IP addresses are able to access your cloud applications,
- The implementation of Governance, Risk & Compliance models,
- Multi-Factor Authentication
- Or the usage of Security Information and Event Management systems
Whenever you need more actionable insights on how to protect your on-premises or cloud applications, Onapsis can help. Let’s talk about how to get cloud-ready as you start moving your most mission-critical applications to the cloud.

