SAP Security Notes: January 2026 Patch Day

New SAP Security year starts with four new HotNews Notes
Highlights of January SAP Security Notes analysis include:
- January Summary – Nineteen new and updated SAP security patches released, including six HotNews Notes and four High Priority Notes
- Critical SQL Injection Vulnerability in S/4HANA – Exploitation can lead to full system compromise by low-privileged users
- Onapsis Research Labs Contribution – Our team supported SAP in patching nine vulnerabilities, covered by seven SAP Security Notes
The new SAP Security year starts with nineteen new and updated SAP Security Notes, including six HotNews Notes and four High Priority Notes. Seven of the seventeen new Security Notes were published in contribution with the Onapsis Research Labs.
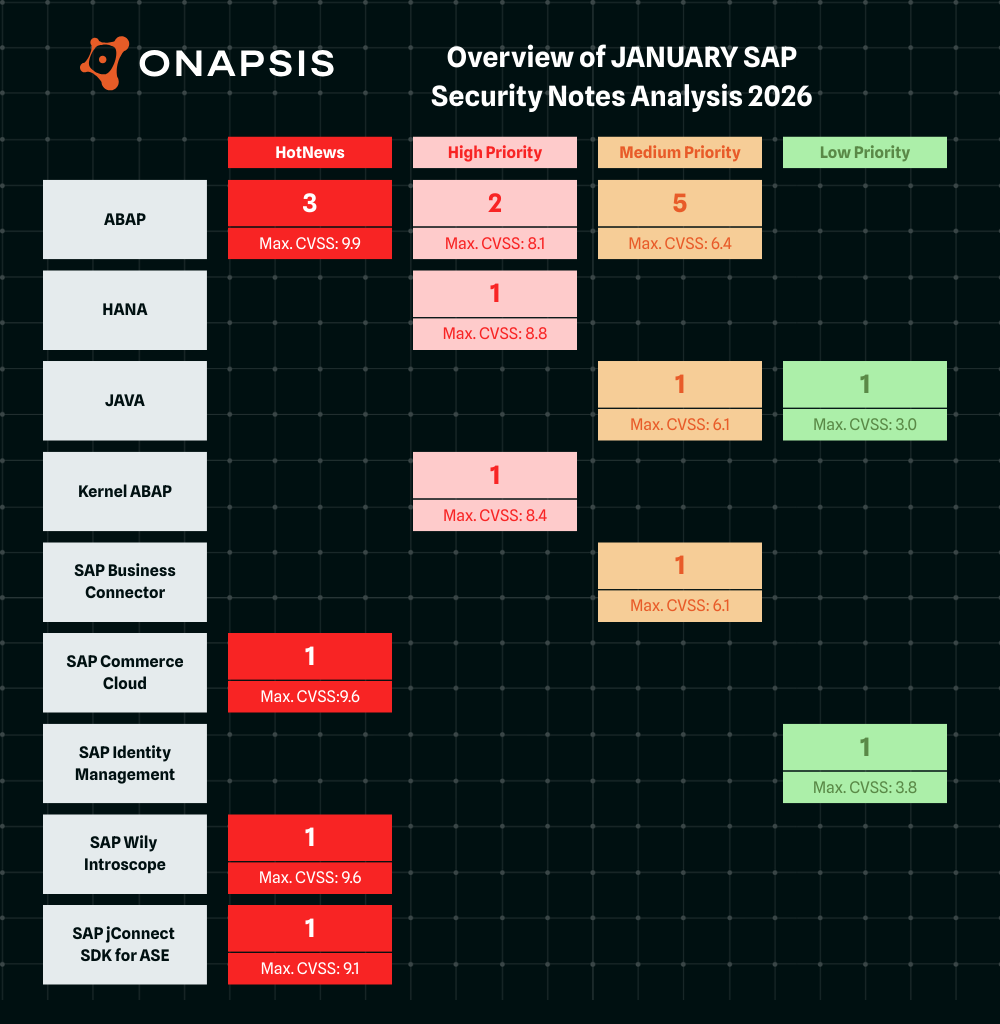
The HotNews Notes in Detail
The Onapsis Research Labs(ORL) supported SAP in patching three of the four new HotNews Notes:
SAP Security Note #3687749, tagged with a CVSS score of 9.9, patches a critical SQL Injection vulnerability in SAP S/4HANA Private Cloud and On-Premise (Financials – General Ledger). The ORL team identified an RFC-enabled function module that uses the ABAP Database Connectivity (ADBC) framework in order to execute a native SQL statement. This SQL statement is provided through an input parameter and allows an attacker to execute arbitrary SQL commands. On successful exploitation, the system can be fully compromised.
SAP Security Note #3668679, tagged with a CVSS score of 9.6, describes a Remote Code Execution vulnerability in SAP Wily Introscope Enterprise Manager (WorkStation). The ORL team detected that the application allows an unauthenticated attacker to create malicious JNLP (Java Network Launch Protocol) files accessible by URL. If a victim clicks on the URL, the accessed Wily Introscope Server could execute commands on the victim’s application. This could completely compromise the confidentiality, integrity and availability of the application.
SAP Security Note #3694242, tagged with a CVSS score of 9.1, patches a Code Injection vulnerability in SAP S/4HANA Private Cloud and On-Premise. Our team identified a remote-enabled function module that allows an attacker with admin privileges to arbitrarily modify the source code of existing programs without enforcing essential authentication checks. Among others, this injection can directly lead to OS command execution and thus to a full compromise of the system.
SAP Security Note #3697979, tagged with a CVSS score of 9.1, patches the same vulnerable function module for standalone SAP Landscape Transformation(SLT) servers and other systems where the affected component is shipped as a separate DMIS add-on.
SAP HotNews Notes #3683579 and #3685286 were initially released on SAP’s December Patch Day. SAP has now added a temporary work around solution to note #3683579 and a Knowledge Base Article (KBA) to note #3685286.
The High Priority Notes in Detail
SAP Security Note #3691059, tagged with a CVSS score of 8.8, addresses a Privilege Escalation vulnerability in SAP HANA database. The vulnerability allows an attacker with valid credentials to switch to another user potentially gaining administrative access. A successful exploit could result in a total compromise of the system’s confidentiality, integrity, and availability.
SAP Security Note #3675151, tagged with a CVSS score of 8.4, patches an OS Command Injection vulnerability in SAP Application Server for ABAP and SAP NetWeaver RFCSDK. The vulnerability allows an attacker with administrative access and adjacent network access to upload specially crafted content to the server. If processed by the application, this content enables execution of arbitrary operating system commands. Successful exploitation could lead to full compromise of the system’s confidentiality, integrity, and availability.
A Missing Authorization Check vulnerability in SAP NetWeaver Application Server ABAP and ABAP Platform is patched by SAP Security Note #3688703, tagged with a CVSS score of 8.1. Due to the vulnerability, an authenticated attacker could misuse a remote-enabled function module to execute existing form routines (FORMs) in the ABAP system with possibly high impact on integrity and availability.
SAP Security Note #3565506, tagged with a CVS score of 8.1, patches three vulnerabilities in SAP Fiori App (Intercompany Balance Reconciliation). They are tracked under CVE-2026-0511, CVE-2026-0496, and CVE-2026-0495. The CVSS score 8.1 is determined by a Missing Authorization vulnerability that could result in an escalation of privileges for an authenticated user.
Onapsis Contribution
The Onapsis Research Labs (ORL) contributed significantly to SAP’s first Patch Day in 2026. In addition to three HotNews Notes, the ORL supported SAP in patching three Medium Priority and one Low Priority SAP Security Note:
SAP Security Note #3666061, tagged with a CVSS score of 6.1, references two patches for SAP Business Connector (BC) that need to be implemented to gain full protection against a Cross-Site Scripting (XSS) vulnerability detected by the ORL. The vulnerability allows an unauthenticated attacker to craft a malicious link. When an unsuspecting user clicks this link, the user may be redirected to a site controlled by the attacker. Successful exploitation could allow the attacker to access or modify information related to the webclient, impacting confidentiality and integrity, with no effect on availability.
Our ORL team identified three ICF services in SAP Supplier Relationship Management that are affected by an Open Redirect vulnerability in the SICF Handler of the SRM Catalog. The vulnerability allows an unauthenticated attacker to craft a malicious URL that, if accessed by a victim, redirects them to an attacker-controlled site. SAP Security Note #3638716, tagged with a CVSS score of 4.7, patches the vulnerability and introduces a positive list of allowed portal domains.
SAP Security Note #3677111, tagged with a CVSS score of 4.3, patches a Missing Authorization check in Business Server Pages Application (Product Designer Web UI). The ORL team reported to SAP that it was able to access non-sensitive information with an authenticated non-administrative user.
SAP Security Note #3657998, tagged with a CVSS score of 3.8, patches an Insufficient Input Handling in JNDI Operations of SAP Identity Management. Staying unpatched, the vulnerability allows an authenticated administrator to submit specially crafted malicious REST requests that are processed by JNDI operations without adequate input neutralization.
Summary & Conclusions
The first SAP Patch Day of the year demonstrates that the mission of our Onapsis Research Labs team has not changed in 2026. With nine reported vulnerabilities, covered by seven SAP Security Notes, the team has once more significantly contributed to greater security for SAP customers.
| SAP Note | Type | Description | Priority | CVSS |
| 3687749 | New | [CVE-2026-0501] SQL Injection Vulnerability in SAP S/4HANA Private Cloud and On-Premise (Financials – General Ledger) FI-GL-GL-G | HotNews | 9.9 |
| 3683579 | Update | Multiple vulnerabilities in Apache Tomcat within SAP Commerce Cloud CEC-SCC-PLA-PL | HotNews | 9.6 |
| 3668679 | New | [CVE-2026-0500] Remote code execution in SAP Wily Introscope Enterprise Manager (WorkStation) SV-SMG-DIA-WLY | HotNews | 9.6 |
| 3685286 | Update | [CVE-2025-42928] Deserialization Vulnerability in SAP jConnect – SDK for ASE BC-SYB-SDK | HotNews | 9.1 |
| 3697979 | New | [CVE-2026-0491] Code Injection vulnerability in SAP Landscape Transformation CA-LT-ANA | HotNews | 9.1 |
| 3694242 | New | [CVE-2026-0498] Code Injection vulnerability in SAP S/4HANA (Private Cloud and On-Premise) CA-DT-ANA | HotNews | 9.1 |
| 3691059 | New | [CVE-2026-0492] Privilege escalation vulnerability in SAP HANA database HAN-DB-SEC | High | 8.8 |
| 3675151 | New | [CVE-2026-0507] OS Command Injection vulnerability in SAP Application Server for ABAP and SAP NetWeaver RFCSDK BC-MID-RFC-SDK | High | 8.4 |
| 3688703 | New | [CVE-2026-0506] Missing Authorization check in SAP NetWeaver Application Server ABAP and ABAP Platform BC-DWB-DIC-F4 | High | 8.1 |
| 3565506 | New | [CVE-2026-0511] Multiple vulnerabilities in SAP Fiori App (Intercompany Balance Reconciliation) FI-LOC-FI-RU | High | 8.1 |
| 3681523 | New | [CVE-2026-0503] Missing Authorization check in SAP ERP Central Component and SAP S/4HANA (SAP EHS Management) EHS-SAF | Medium | 6.4 |
| 3687372 | New | [CVE-2026-0499] Cross-Site Scripting (XSS) vulnerability in SAP NetWeaver Enterprise Portal EP-PIN-NAV | Medium | 6.1 |
| 3666061 | New | [CVE-2026-0514] Cross-Site Scripting (XSS) vulnerability in SAP Business Connector BC-MID-BUS | Medium | 6.1 |
| 3638716 | New | [CVE-2026-0513] Open Redirect Vulnerability in SAP Supplier Relationship Management (SICF Handler in SRM Catalog) SRM-EBP-CAT | Medium | 4.7 |
| 3655229 | New | [CVE-2026-0493] Cross-Site Request Forgery (CSRF) vulnerability in SAP Fiori App (Intercompany Balance Reconciliation) FI-LOC-FI-RU | Medium | 4.3 |
| 3677111 | New | [CVE-2026-0497] Missing Authorization check in Business Server Pages Application (Product Designer Web UI) PLM-PPM-PDN | Medium | 4.3 |
| 3655227 | New | [CVE-2026-0494] Information Disclosure vulnerability in SAP Fiori App (Intercompany Balance Reconciliation) FI-LOC-FI-RU | Medium | 4.3 |
| 3657998 | New | [CVE-2026-0504] Insufficient Input Handling in JNDI Operations of SAP Identity Management BC-IAM-IDM | Low | 3.8 |
| 3593356 | New | [CVE-2026-0510] Obsolete Encryption Algorithm Used in NW AS Java UME User Mapping BC-JAS-SEC-UME | Low | 3.0 |
As always, the Onapsis Research Labs is already updating The Onapsis Platform to incorporate the newly published vulnerabilities into the product so that our customers can protect their businesses.
For more information about the latest SAP security issues and our continuous efforts to share knowledge with the security community, subscribe to our monthly Defender’s Monthly Newsletter.
Frequently Asked Questions
How many Security Notes were released in the January 2026 Patch Day?
There were a total of 19 new and updated SAP Security Notes released this month. This includes six HotNews Notes (the highest criticality) and four High Priority Notes.
Which vulnerability poses the highest risk this month?
The most critical issue is SAP Security Note #3687749, which received a CVSS score of 9.9. This note addresses a critical SQL Injection vulnerability in SAP S/4HANA (Financials – General Ledger). If exploited, it could allow a low-privileged user to execute arbitrary SQL commands and achieve a full system compromise.
What contributions did Onapsis Research Labs make to this patch day?
The Onapsis Research Labs (ORL) played a significant role, contributing to the remediation of nine vulnerabilities covered by seven SAP Security Notes. Specifically, the ORL team assisted SAP in patching three of the four new HotNews Notes released this month.
Are there any critical Remote Code Execution (RCE) vulnerabilities?
Yes. SAP Security Note #3668679 (CVSS 9.6) addresses an RCE vulnerability in SAP Wily Introscope Enterprise Manager. The Onapsis Research Labs discovered that an unauthenticated attacker could create malicious JNLP files; if a victim interacts with the malicious URL, the attacker could execute commands on the victim’s application, compromising its confidentiality, integrity, and availability.
Which SAP S/4HANA vulnerabilities were identified by Onapsis?
In addition to the SQL Injection in Financials (Note #3687749), Onapsis identified a Code Injection vulnerability in SAP S/4HANA Private Cloud and On-Premise, patched in SAP Security Note #3694242 (CVSS 9.1). This vulnerability allows an attacker with admin privileges to modify source code without proper authentication, potentially leading to OS command execution.
Were there any updates to previously released HotNews Notes?
Yes, two HotNews Notes initially released in December were updated:
- Note #3683579 (Apache Tomcat in SAP Commerce Cloud) was updated with a temporary workaround.
- Note #3685286 (Deserialization in SAP jConnect) was updated with a new Knowledge Base Article (KBA).
What other high-priority components are affected?
Other critical patches include:
- SAP HANA Database: Note #3691059 (CVSS 8.8) fixes a Privilege Escalation vulnerability.
- SAP Application Server for ABAP: Note #3675151 (CVSS 8.4) fixes an OS Command Injection vulnerability.
- SAP Fiori App (Intercompany Balance Reconciliation): Note #3565506 (CVSS 8.1) addresses multiple vulnerabilities including Missing Authorization.
