Oracle On Oracle: Business Application Security
On December 4th, we held a webinar in partnership with Oracle discussing the major aspects of addressing security for business applications. We welcomed Elke Phelps, Product Manager in the Oracle eBusiness Suite Applications Technology Group, and Bruce Lowenthal, Leader of the Oracle Security Alerts Group. If you didn’t attend, I highly recommend you drop everything and watch the on-demand recording.
As you may know, The Onapsis Research Labs works very closely with Oracle to report potential security vulnerabilities for Oracle to fix and for Oracle customers to patch. We love to talk about not only the work we do but also the benefits of keeping up with patches and maturing the security posture of your ERP Applications. We reported some of the first vulnerabilities in J. D. Edwards more than 10 years ago, and ever since, we have been working with Bruce and the Oracle security team very professionally through a responsible disclosure process.
Why are ERPs so special?
You may ask, how is a business-critical application different from any other application that you are running in your organization today? Well, there are a couple of attributes that really defined what this application is about:
- A complex architecture
- A layer of customized functionality on top of the application
- A heavy instance of interconnectivity, with data passing back and forth between applications
- And lastly, they’re critical! The business can not function without these applications
Cybercriminals of diverse size and nature are turning their eyes towards business applications more and more, not only because of how critical those applications are to the business operations, but also because of the sensitivity and value of the data that is hosted by these applications.
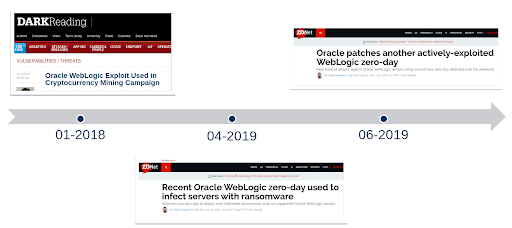
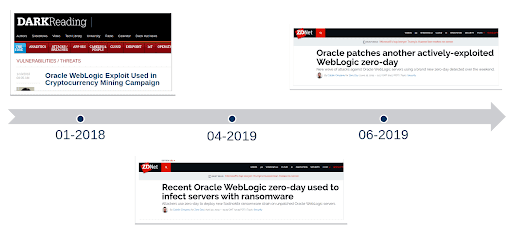
We’ve been focusing on answering two rather complex questions: what are the right controls, and what are the right mechanisms that we need to implement in terms of securing these applications from cyberattacks? This continuous increase in the interest of cyber threat actors around ERP vulnerabilities makes it even more important now to prioritize the security of the crown jewels accordingly.
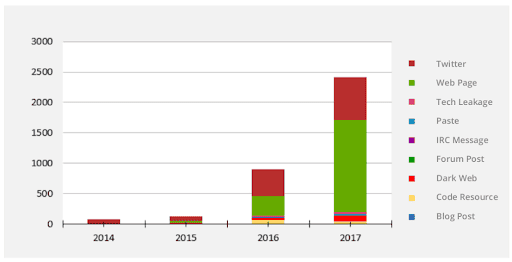
This continuous increase in the interest of cyber threat actors around ERP vulnerabilities makes it even more important now to prioritize the security of the crown jewels accordingly.
Defensive Measures for Oracle EBS
There have been a number of successful exploits against Oracle products. Many of these successful exploits were against interfaces that should not have been internet accessible, meaning that customers didn’t follow the secure deployment instructions that Oracle provides and left many of these interfaces open to the Internet. Nearly all of these would have been prevented by proper patch application and following secure deployment guidelines.
The defensive challenge is understandably tough for customers. The complexity of these applications creates plenty of attack surfaces for exploiters. And the disruption often created by patches and system updates provides a disincentive for performing critical fixes. There has also been a large growth in third party fix releases which dramatically increases the number of security fixes that must be applied.
Moving Forward
So what do we do? In terms of action items, it begins with identifying your business processes but more importantly your business applications. The following questions can help guide the process of identifying what’s most important for you:
- What is the data and which are the processes that are being supported by your business applications?
- How much do these applications really matter to you?
- How much risk do those applications represent to your organization?
- How long is the organization able to survive or not with downtime or a compromise to those applications?
Once we went through that understanding process, then we need to understand what are the processes and controls that we have implemented in all the identified business applications. That should be fairly straight forward but it requires conversations with applications’ owners, cross-business unit owners, IT security teams, IT teams and the Internal Audit organization. Understanding existing controls will give you kind of a heat map on what’s important and what’s the level of risk that you may have in your organization applications.
In the next few months, and after that, make sure that you have the right security program in place, that your security programs also include business applications in terms of vulnerability and patch management, continuous monitoring, compliance automation, and being able to respond to any type of risks in a timely manner.
Final Takeaways
In conclusion, securing Oracle E-Business Suite is a continuous process, it’s not just one and done. A security patch that may seem irrelevant to your system today, could become very relevant tomorrow if attackers begin targeting that area. It’s up to companies running Oracle software and Oracle applications to put the right mechanisms in place and have the right processes to actually address these situations when they arise.
For more detail, watch the full webinar on-demand: Key Steps to Securing Oracle Business-Critical Applications.

