Onapsis Provides All SAP Customers with Free RECON Vulnerability Scanning Tool
Onapsis has released a new free online service and downloadable open source tool for all SAP customers to quickly help organizations assess if SAP systems are vulnerable and detect suspicious activity related to the RECON vulnerability (CVE-2020-6287). The INSTANT RECON service is available for immediate use online or for download from Github to run locally as an open source tool to scan SAP systems and logs for likely indicators of compromise (IoC) and assess if systems may be vulnerable.
Background
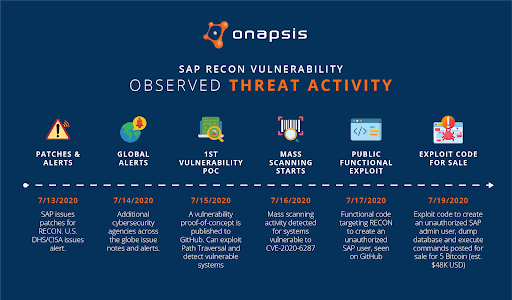
On July 13, SAP patched a critical vulnerability in their NetWeaver Java technology stack. Dubbed RECON (Remotely Exploitable Code On NetWeaver), this vulnerability, discovered by the Onapsis Research Labs, hits the maximum CVSS score of 10.0, meaning it is both trivial to exploit and the potential business impact is high.
Given the severity of this vulnerability, the U.S. Department of Homeland Security issued a US-CERT Alert, AA20-195A, in coordination with BSI CERT-Bund and followed by other global organizations, providing warnings about potential threats associated with this vulnerability.
Observations Since Patch Availability
Since the patch for RECON was released by SAP, Onapsis and the Onapsis Research Labs have been closely monitoring activity around RECON, while continuing our efforts to bring faster, more reliable detection for this vulnerability.
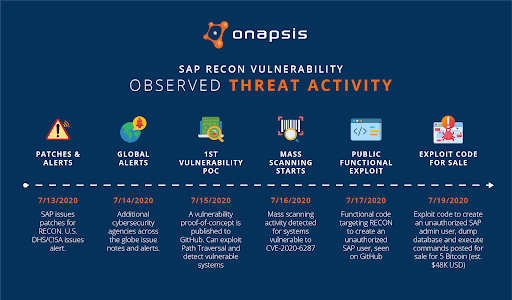
The day following the RECON patches, additional CERT partners and other cybersecurity agencies across the globe issued additional alerts and notes urging businesses to patch their systems. Just two days in, on July 15, a vulnerability proof-of-concept (PoC) was published to Github. The Python script used in this PoC could be used to identify a vulnerable system, but did not carry out any remote code execution or user creation. Noting the speed at which a PoC was published, multiple press articles were published again urging businesses to patch their systems as it would only be a matter of time before a full exploit would be developed.
Following publication of the vulnerability PoC, a high volume of scans were observed. Some initial scans were from security researchers and other individuals using services to gather statistics on potentially vulnerable systems, but these are generally one-off or periodic scans. The mass scans observed on July 15 and 16 were indicative of malicious scans looking to exploit CVE-2020-6287, a.k.a. RECON.
On July 17, Onapsis became aware of a functional exploit for RECON published to Github. Just four days after the original patch was released by SAP, code to exploit the vulnerability was now public.
Accelerated Advancement and Events to Come
With the availability of an exploit PoC on July 17, we have observed multiple iterations of functional exploits, including a post seeking 5 BTC (Approx 48,000 USD) in exchange for a working exploit for CVE-2020-6287 that would create an admin-level user on the target system and allow for database dumps and other malicious actions.
This rapid progression of events is in-line with expectations of a CVSS 10 vulnerability. It is difficult to overstate the magnitude of this threat—it is vital that businesses patch now, most critically those with internet-facing systems. It is only a matter of time before a fully functional exploit is turned into something that can be used on a mass-scale, and we have to assume that advanced threat actors have already weaponized this successfully. Repercussions of a successful attack could result in complete compromise of confidentiality, integrity and availability of SAP mission-critical applications—leading to a cyber breach, disrupting the business and causing serious regulatory compliance violations.
Understanding the urgency of scanning, detecting and patching, Onapsis has worked swiftly to create an online service and downloadable open source tool to help all SAP customers check their systems for the RECON vulnerability and evidence of what may have been from a successful exploit.
Introducing INSTANT RECON
What Is It?
To help organizations identify if their SAP systems are vulnerable, Onapsis has released INSTANT RECON, a free online service and set of open source python scripts that can be run locally. With this service and tool you can scan your internal and public SAP instances to identify if it may be vulnerable to RECON, and to look for likely indicators of compromise (IoC) from successful exploitation of RECON.
Where to Find It?
You can find the online scanner for internet-facing SAP systems here. The local scanner for internal SAP systems is available on our Github repository.
How Do I Use the Online Service?
For the online service, you’ll need an email and the URL of your publicly-accessible SAP instance to scan for the presence of the vulnerability.
Additionally, you can upload SAP NetWeaver JAVA Responses trace and SAP JAVA Application logs to check for IoCs.
Visit our INSTANT RECON page for more information.
How Do I Use the Local Scanner?
The local scanner is a set of open source scripts written in Python. Like the online service, it supports both checking for the RECON vulnerability as well as IoC scanning. Please refer to the readme on the INSTANT RECON Github repository for detailed instructions.
How Do I Use the Results?
Systems that return a positive result for the RECON vulnerability should be patched immediately. Especially for internet-facing instances. If you cannot patch your system, it is recommended to disable the LM Configuration Wizard service as outlined in SAP’s security note.
If log analysis shows an IoC, you should report this immediately to your internal Information Security team for closer analysis and follow established incident procedures. It is highly recommended to perform in-depth scan analysis of affected systems and any inter-connected satellite systems to look for additional indicators and determine the extent of the potential compromise.
Please keep in mind that scans showing that your systems are not vulnerable against RECON and show no IoCs is by no means a guarantee, as blackbox vulnerability assessments and this type of IoC scanning have several known limitations. Still, with an ever-expanding threat landscape, it is vital to continue to patch and monitor your ERP systems for suspicious and atypical activity.
Do I Need to Be an Onapsis Customer to Use This Service?
INSTANT RECON is available to all SAP customers and to the broader SAP security community. While Onapsis customers already have security capabilities through their Onapsis Platform subscription, the increased threat activity compelled us to make this tool and service freely available so that all global organizations could protect themselves.
Can I Scan for Other Vulnerabilities Besides Recon?
This service is built specifically for RECON. The Onapsis cybersecurity and compliance solution for SAP, The Onapsis Platform, provides automated assessments of SAP systems for hundreds of critical vulnerabilities and misconfigurations and continuously monitors for internal and external threats. To check for additional critical vulnerabilities and misconfigurations in SAP, request a complimentary Cyber Risk Assessment from Onapis today.

