Moving SAP to the Cloud? Let Security Be On Your Side
In today’s evolving IT landscape, companies are constantly planning their next steps when it comes to business-critical application security. Specifically, they are planning these steps around their SAP environment which supports core business processes for some of the world’s largest organizations. When it comes to migrating SAP solutions to the cloud, different roadmaps are regularly being assembled and developed in order to properly transfer solutions that were traditionally supported by on premise SAP systems to a diverse range of cloud offerings provided by SAP.
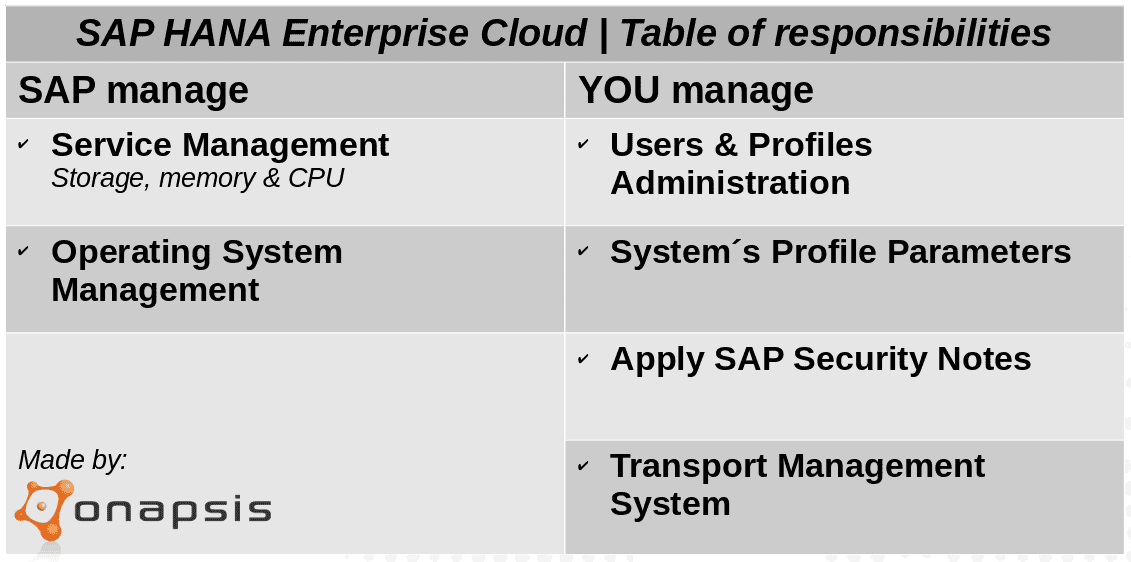
When logistically planning this migration, organizations must have a very transparent migration path. This path should consider tasks that SAP can and will take care of, as well as which actions will fall on internal teams to achieve.
Our goal behind this blog is to provide SAP customers with a pragmatic approach for securly transitioning their SAP solutions to the Cloud. To do so, we will analyze a privately managed cloud environment – the SAP HANA Enterprise Cloud (HEC) – which is one of the most relevant SAP IaaS offerings. Additionally, we will focus on common challenges and common questions our customers are dealing with, on a regular basis.
Starting with service management, organizations will no longer be struggling with the capacity management of their system’s landscapes. Storage, memory and CPU resource usage will be SAP’s responsibility. This means that operational issues, as well as changes and extensions needed based on resource consumption, will no longer be the responsibility of your IT team, and will be handled by SAP. They will also manage data centers, monitor disks and server capacities and will supervise remote connections between the hosted system landscapes and SAP’s support infrastructure. The key part of this is to understand the SLA’s provided by the vendor and how they are able to achieve it.
Contract negotiation is the right tool to ensure the service levels demanded by the organizations. Regarding OS management, servers will most likely be shipped with the latest available security patch level. Depending on your service contract agreements, installation of OS patches and security updates can be on your schedule. On the other hand, creating and maintaining OS users and groups, as well as configuring OS parameters relies on SAP. In addition, troubleshooting operating system problems and monitoring system logs and file systems also rely on SAP. However, the situation changes when speaking about SAP version upgrades. Organizations must program and develop their upgrade work plans, in concordance with their daily work operations. Modification adjustments, as well as functional changes to custom objects must be done by each company to avoid any misunderstanding.
Your SAP Security team is still in charge of SAP user’s administration and assigning authorizations. Definition, maintenance, review and audit of roles and profiles relies on them too. Change control known as application customizing, configuration, maintenance, support and troubleshooting must also be on your side. It’s important to highlight that applying SAP Security Notes to SAP hosted software system is the customer’s responsibility. This work is critical and therefore cannot be delegated. Installation, configuration and patching add-ons are also responsibilities of each customer. SAP is in charge of maintaining SAP systems profile parameters, but we strongly recommend periodically checking them to validate secured values. Something similar happens with the interfaces in between SAP Systems (RFC connections). Although SAP will configure some technical RFC connections to systems managed by them, companies will still configure RFC connections to other systems, such as those that are application-related.
RFC connections must then also be verified systematically. Configuring and maintaining SAP Transport Management System (STMS) setup of transport routes, is on your scope. The transfer and release of transport orders will continue being daily work tasks. It is highly advised that before importing critical transports, you inform SAP and perform the transport as a scheduled activity. You need to provide application communication requirements, determine security requirements, as well as create and maintain security policies. No matter if you’re working in the cloud or on premise, you must determine a security strategy and an implementation plan to monitor and assess your landscape.
Last but not least, configuration and customization of SNC is a must to secure communications on the cloud too. SNC protects the data communication paths between the various client and server components of the SAP system that use the SAP protocols RFC or DIAG. 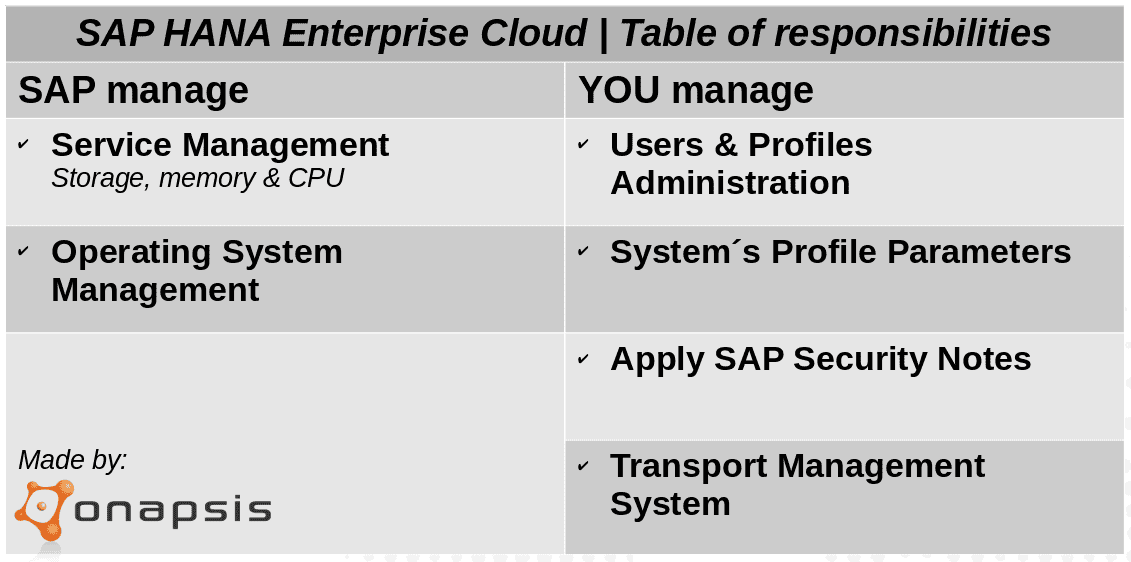
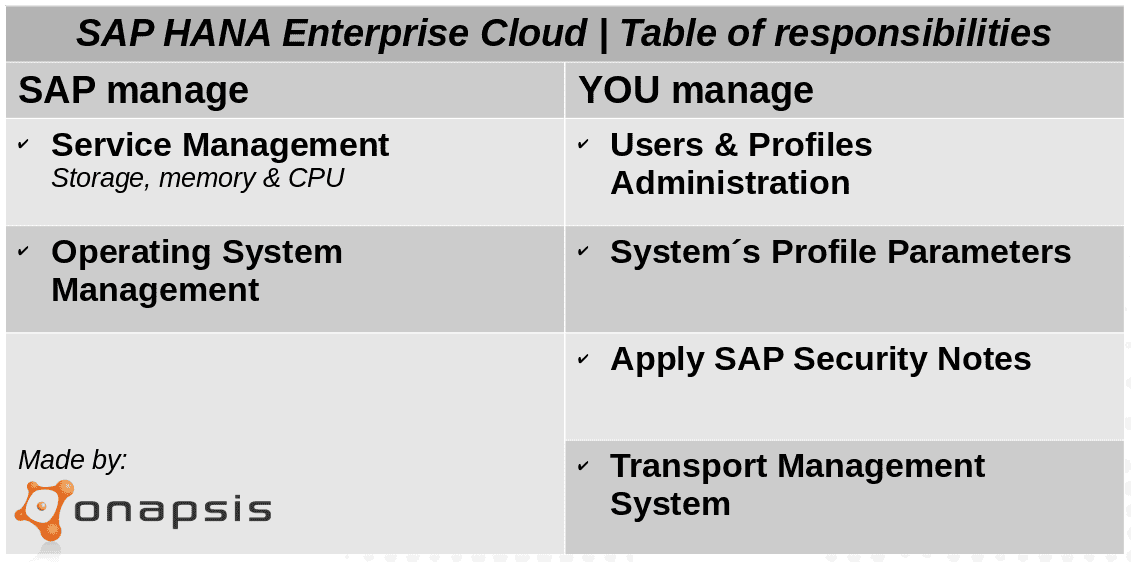
To sum up, migrating SAP applications to the cloud has many operational benefits (such as scalability and resources), but it must be considered that the data hosted in those applications still belongs to the organization, so ultimately, the responsibility of securing these applications relies on the organization. In this sense, most of the security challenges we face in the on-premise scenarios are still applicable in the cloud, so It is extremely important to determine which tasks are critical that must still be executed by the organization itself. The remainder of tasks should still be verified periodically to ensure there are enough controls in place to keep your business-critical data and processes safe.
