A Look Back at SAP Vulnerabilities in 2022

2022 was another eventful year for the Onapsis Research Labs team, as we continue to provide impactful threat intelligence for our customers and educate the broader communities on how to protect their SAP applications and organizations from growing threats. All our research and threat intelligence posts can be found here, but for a quick recap of the year’s main highlights, take a scroll through the 2022 timeline below and ensure your organization is protected from these SAP vulnerabilities.
Kicking Off 2022 With Log4j
On December 9, 2021, a critical vulnerability (CVE-2021-44228) in Apache log4j, a widely used Java logging library, was made public. Facing the noise that started after publication and the high number of HotNews Notes that SAP was starting to release just two days after the official SAP December Patch Day, CISOs and SAP Basis teams around the world realized that it was going to become a busy Christmas time and a challenging start into 2022. This was also reflected in the January’s SAP Patch Day statistics which showed a record-breaking number (20) HotNews Notes.
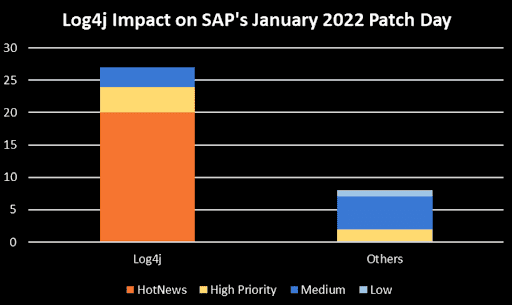
The Onapsis Research Labs (ORL) worked around the clock to understand the impact of this vulnerability on some of the most widely used SAP products. The team used the Onapsis Threat Intelligence Cloud for their analysis, a set of sensors to monitor exploit attempts. The final results of this analysis were published at the end of January. Details can be found here.
The number of exploit attempts shows the importance of patching all affected SAP applications. However, SAP applications are quite complex and taking all available application and system setups into account is a big challenge. This is underlined by another statistic – the number of released Log4j related documents on the SAP Help Portal since the vulnerability was made public. 57 of the 271 documents were last updated in November/December, showing that Log4j is still not over for SAP customers.
|
|
|
|
|
|
|
|
|
|
For further assistance with the Log4j vulnerability and the impact to your SAP systems, contact our team.
The Next Challenge: ICMAD Vulnerabilities
While SAP Basis teams were busy with applying the consecutively released Log4j patches, the next critical CVSS 10.0 vulnerability, dubbed ICMAD (Internet Communication Manager Advanced Desync), was disclosed by SAP in SAP’s February Patch Day. The Onapsis Research Labs and the SAP Product Security Response Team (PSRT) collaborated to discover and patch three critical vulnerabilities affecting SAP’s Internet Communication Manager (ICM). The individual ICMAD vulnerabilities are identified as CVE-2022-22536, CVE-2022-22532, and CVE-2022-22533 – the first of which received the highest possible risk score, a 10 out of 10, while the other two received scores of 8.1 and 7.5, respectively.
The Onapsis Research Labs were able to validate that attackers could use these SAP vulnerabilities in the ICM to exploit and hijack arbitrary SAP user’s requests (including their sessions) and subsequently take over the SAP application. In addition, using new HTTP Response Smuggling techniques, attackers could control responses sent by the SAP application and persist the attack. This means that with a single request, an attacker could be able to steal every victim session and credentials in plain text and modify the behavior of the applications.
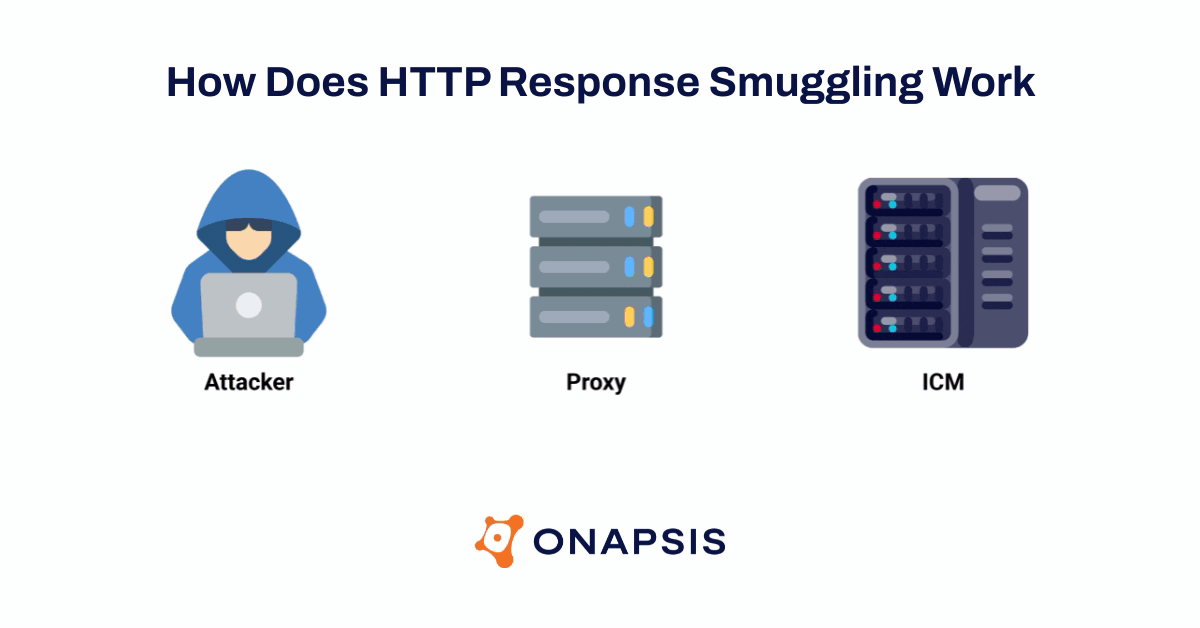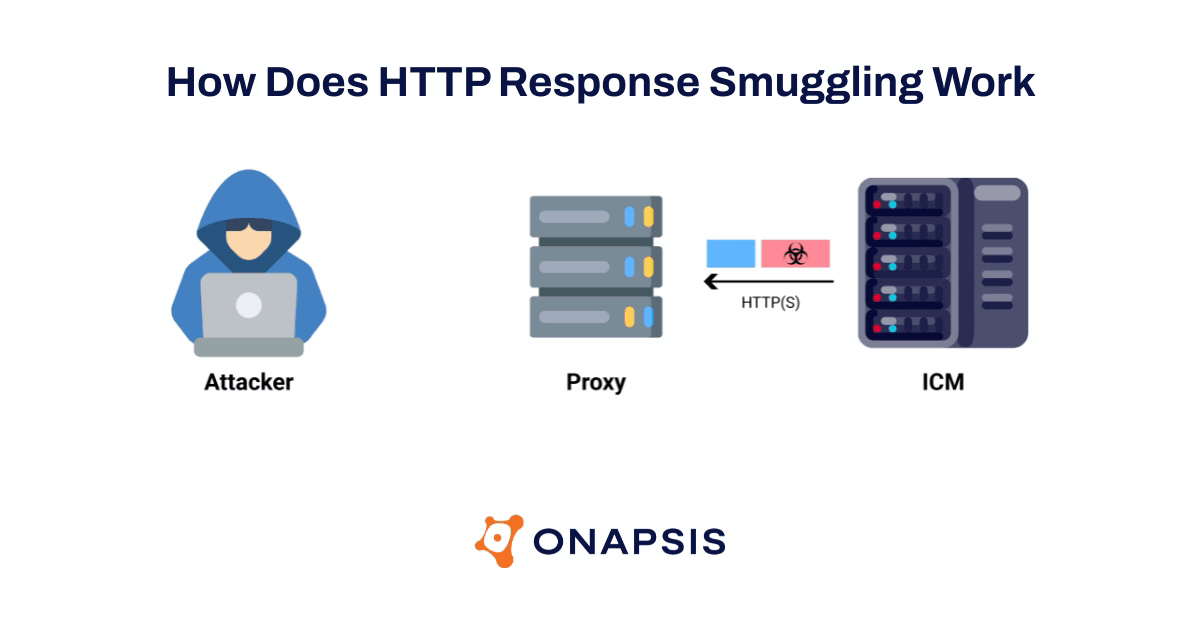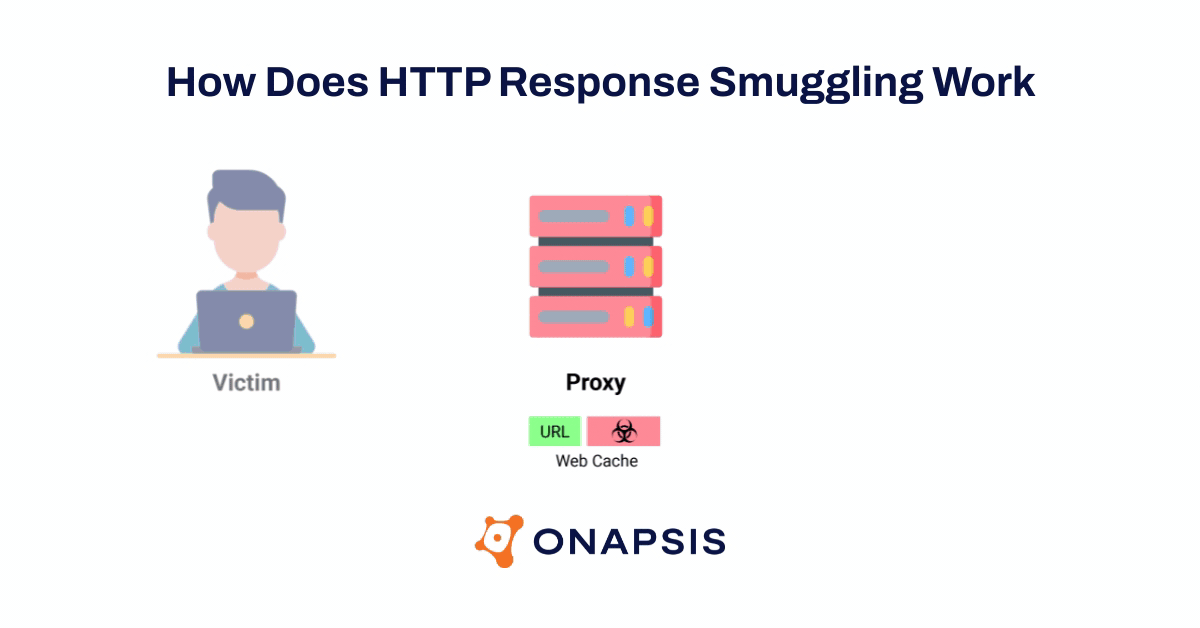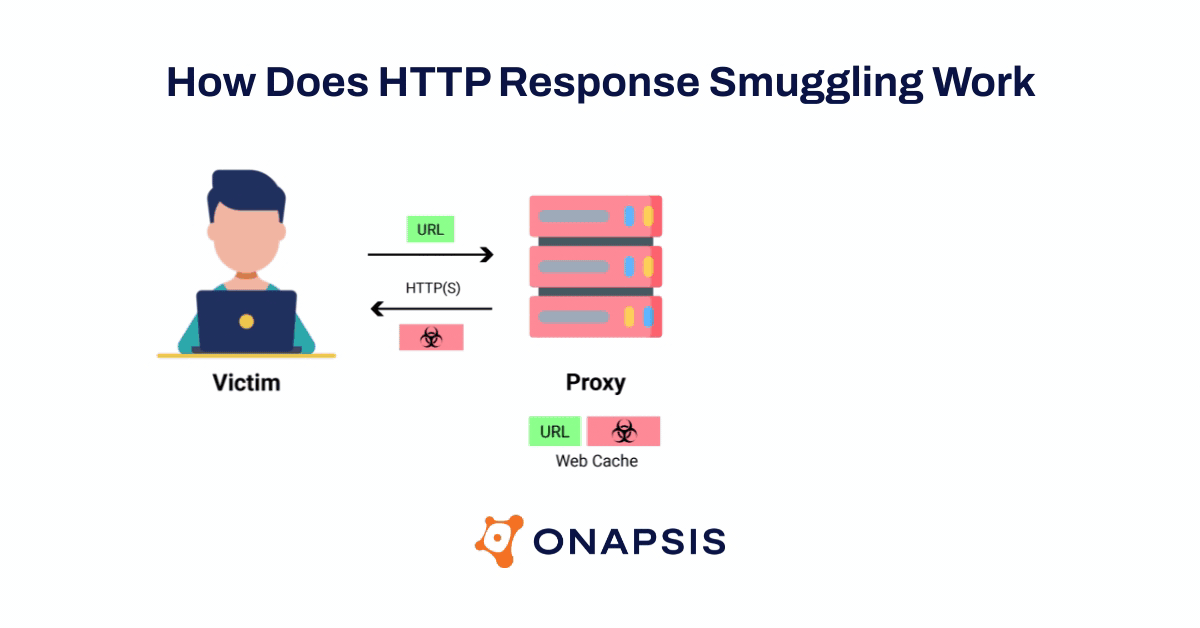
As a result of the potential threats associated with the ICMAD vulnerabilities, numerous global organizations like the Cybersecurity & Infrastructure Security Infrastructure Agency (CISA), the Canadian Center for Cybersecurity, and the German Bundesamt für Sicherheit in der Informationstechnik (BSI) have issued alerts. As part of Onapsis’ responsible outreach to the global SAP community, the Onapsis Research Labs created a free vulnerability scanning tool that allows any SAP customer to scan for applications across their SAP landscape that are affected by these vulnerabilities.
Spring4Shell is No April Fools
On March 30, 2022, information regarding a new zero-day critical vulnerability affecting the Spring Framework core, an extremely widely-used open-source application framework for the Java platform used in enterprise applications, was released on various websites and technical blogs. Fortunately, when looking at the number of affected SAP applications, it didn’t mean another Log4j-like event. SAP provided a first patch on its April Patch Day for SAP HANA Extended Application Services. SAP Security Note #3170990 provides a summary of all affected SAP applications (as of December 5):
- SAP HANA Extended Application Services
- SAP Customer Checkout
- PowerDesigner Web
- SAP Customer Profitability Analytics
- SAP Commerce
- SAP Business One Cloud
August: ICMAD Vulnerability Added to CISA’s Known Exploited Vulnerabilities Catalog
On August 18, 2022, The US Cybersecurity and Infrastructure Security Agency (CISA) added the most critical ICMAD vulnerability–CVE-2022-22536–to its Known Exploited Vulnerabilities Catalog (KEV). While federal civilian agencies are bound by BOD 22-01 to address all applicable vulnerabilities in the KEV, CISA highly recommends that all organizations take action immediately if they haven’t already done so.
SAP Patch Day Statistical Trends
The overall number of 211 SAP Security Notes in 2022 corresponds to an increase of 14% compared to 2021. This number was strongly impacted by the large amount of Log4j related Security Notes. When subtracting the notes of this exceptional event, the total number is reduced to 178, which would represent a new all-time low.
Looking at the numbers per priority, it is also worth providing separate statistics – with and without Log4j:
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
The Onapsis Research Labs contributed to patching 22 vulnerabilities, compared to 18 in 2021. This increase is all the more remarkable as the team was involved in a large number of joint initiatives with SAP around Log4j, ICMAD, and Spring4Shell.
Final Thoughts
In the last 25 years, SAP has introduced more and more open source libraries. 2022 has impressively shown the risk that is related to this (necessary) strategy change. This year, SAP customers were confronted with a large number of critical patches that were released relating to just two external libraries. It is all the more important that SAP vulnerabilities are not running out of scope. Our team from the Onapsis Research Labs will continue to work to keep the world’s leading brands steps ahead of would-be malicious attackers. But remember: even the most critical patches are worthless if they are not implemented in a timely manner.
Subscribe to our Defender’s Digest newsletter for the latest in SAP security.
