How the Proposed OWASP TOP 10 Changes Would Affect SAP and Oracle
While only in release candidate form, the current proposed changes to the OWASP Top 10 Application Security Risks provide clear guidance for any enterprise that needs to secure and protect their critical enterprise business applications. In general, the OWASP Top 10 and these two additions can be directly applied to an approach and methodology for securing ERP based business applications and systems.
The two additions are:
-
2017-A7: INSUFFICIENT ATTACK PROTECTION:
The majority of applications and APIs lack the basic ability to detect, prevent, and respond to both manual and automated attacks. Attack protection goes far beyond basic input validation, and involves automatically detecting, logging, responding, and even blocking exploit attempts. Application owners also need to be able to deploy patches quickly in order to protect against attacks.
-
2017-A10: UNDERPROTECTED APIS:
Modern applications often involve rich client applications and APIs, such as JavaScript in the browser and mobile apps, that connect to an API of some kind (SOAP/XML, REST/JSON, RPC, GWT, etc.). These APIs are often unprotected and contain numerous vulnerabilities.
These changes are not random or ad-hoc changes, but were made based on data that spans vulnerabilities gathered from hundreds of organizations, and over 50,000 real-world applications and APIs. The Top 10 items are selected and prioritized according to this prevalence data in combination with consensus estimates of exploitability, detectability, and impact.
If we look at both of these changes with the filter of ERP security, we can see how meaningful these controls are to help ensure the secure operation of ERP systems and applications.
2017-A7: Insufficient Attack Protection
The description of this application security risk states “Attack protection goes far beyond basic input validation and involves automatically detecting, logging, responding, and even blocking exploit attempts.” This mirrors the standard security practice of making the appropriate actions and investments to prevent attacks, but also assumes that despite these efforts, the system will ultimately be compromised. Organizations need to have the capability to know they’ve been attacked in order to respond as quickly as possible and mitigate the compromise.
This has been Onapsis’ viewpoint since our inception, and in fact, the description of this risk reads like our mission statement as the Onapsis Security Platform (OSP) was built to enforce these beliefs. OSP analyzes business-critical applications such as SAP and Oracle systems to report on missing security patches and configuration issues that would make a system compromise possible. Beyond that, OSP automatically monitors the system to detect attacks and respond based on rules designed by the enterprise. Through virtual patching, exploit attempts can be blocked before they even reach ERP systems.
2017-A10: Underprotected APIs
Underprotected APIs are a real challenge in the SAP world. The APIs just happen to be called RFC Destinations, these connections allow SAP systems to perform business processes (such as fulfilling business orders, adjusting inventory levels and issuing payments, as examples). However, if these connections were defined without any security review, they can expose the enterprise to a high risk of compromise. The challenge for the enterprise is understanding which APIs are available, and how they are used. Because ERP systems allow for unattended actions, system administrators and business owners are often not aware of the scope and purpose of these API type calls terminating at or initiating from their systems.
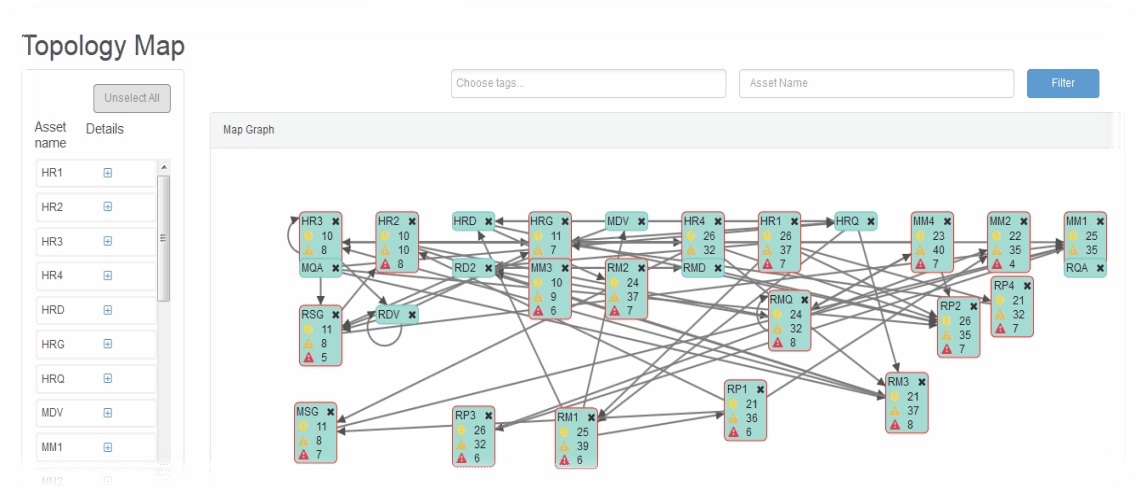
Again, because OSP was built with security and compliance needs of the enterprise in mind, it has the capability to identify and map out all of these connections that exist between ERP systems being monitored by OSP. In addition, OSP provides details about the relative risk of those connections, thus focusing review and remediation efforts on those connections that pose the most risk to the enterprise.
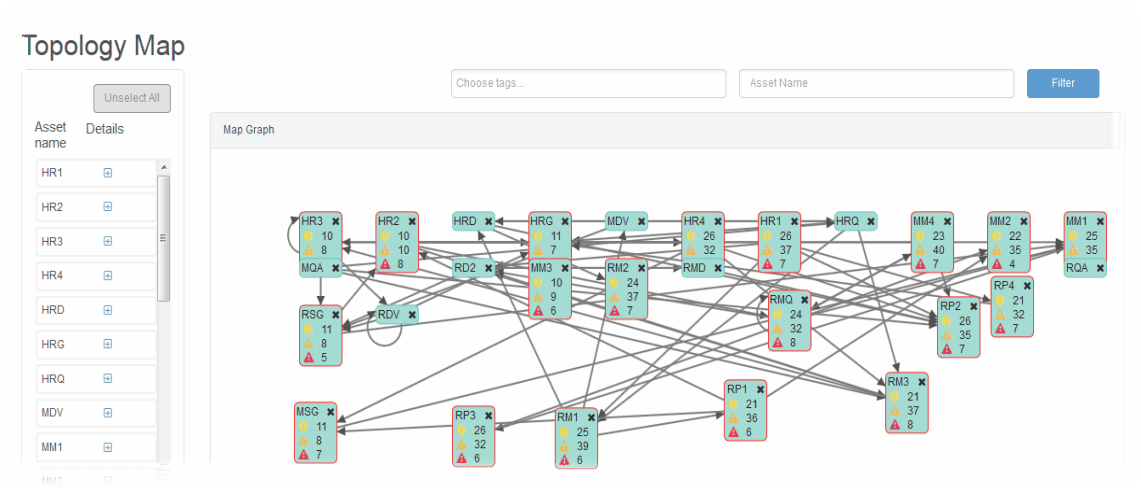
For those tasked with ensuring that ERP systems remain secure and compliant, understanding changes to security frameworks like those proposed by OWASP are important to consider. These proposed changes help to establish that security and audit requirements of the enterprise will match with threats the OWASP community are seeing as the most pressing and critical to applications today.
Fortunately, those leveraging OSP are already receiving coverage of new additions to the OWASP Top Ten. Since OSP is built to meet the security needs of our customers and aligns with the projections of our Research Labs, it is the only product that anticipates forthcoming security trends to always have you covered. As threats facing ERP systems continue to advance, you can have confidence that OSP will always be updated to address new threats to your enterprise applications.

