How to know if your SAP systems are affected by WannaCry
IMPLEMENT NEWLY RELEASED SAP SECURITY NOTE: 2473454 TO CONFIRM YOUR SAP SYSTEMS ARE PROTECTED.
Last Friday, the information community was cautioned about a massive ransomware attack taking place around the world. This attack, known as ‘WannaCry’, utilized malware which affected thousands of computers in more than 100 countries. Based on its characteristics, it is able to quickly spread through corporate users through SMB service. Here’s an infection map made by the researcher that discovered (and registered) a queried domain that helped to stop the first version of this attack (there is new versions already reported in the wild):
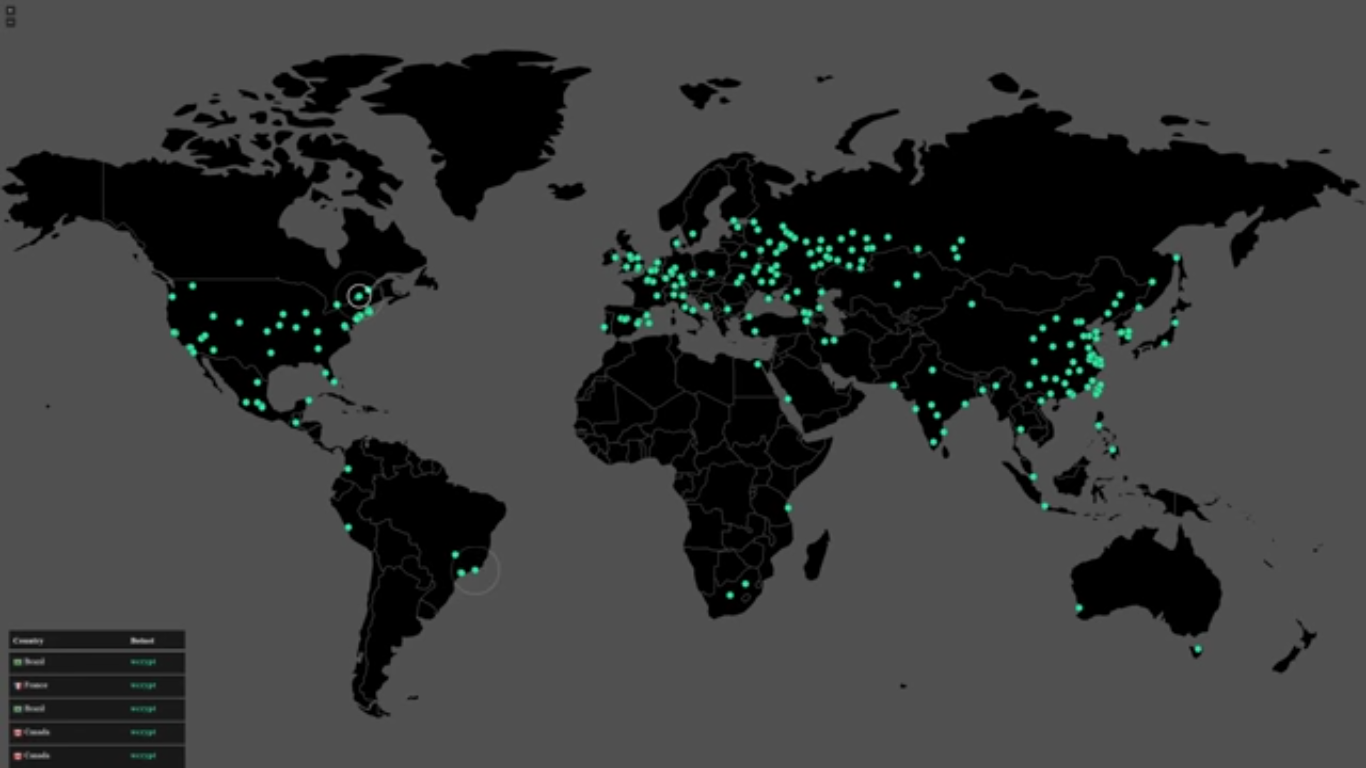
On Friday, several companies around the world, including the biggest telecommunication company in Spain, NHS healthcare facilities in United Kingdom, several Universities as well as large companies such as Hitachi, were reportedly affected. Due to the impact of such large organizations being affected, some ran out of service on Friday, placing thousand of customers or patients in waiting mode for several hours, and in some cases, more than a day.
Today, SAP released SAP Security Note 2473454 that confirms that if infected, SAP Systems won’t be available. The patch confirms that SAP Servers can be affected by this ransomware attack, and that users should upgrade their system urgently. This note does not modify anything in SAP software, and should be executed manually. Additionally, this note includes several links for more information. According to a SAP customer on the SAP Answers site, SAP confirmed that there is “no side effect on SAP applying this OS patch”. Nevertheless, we strongly suggest that proper testing of critical process context be completed, what should mean not to have sensitive delays during this stage.
According to a report published last year from the Ponemon Institute, if a SAP system is taken offline, it could lead to $4.5 million average cost for big companies. Below is some additional information about WannaCry to ensure that your SAP infrastructure remains protected.
How the attack works?
WCry or WannaCry, is a ransomware attack which includes some particularities of a worm. As most ransomwares, once it hits you, it will encrypt all your data and ask for money (bitcoins) in order to decrypt it. The most innovative part of Wcry is how it spreads and looks for new targets. Besides using the usual methods of spreading, such as email, it also abuses a vulnerability patched by Microsoft in March 2017 that affects the SMB (Server Message Block) v1 protocol. Once one system is infected, it will scan the entire network looking for hosts running SMB v1 and exploit the aforementioned bug to take control of a new victim. This leads to a massive infection inside companies that are using this vulnerable protocol without proper patching.
First versions of Wcry used a well-known strategy called “Kill Switch” which aims to detect if the malware is inside a sandbox or not. In this case, Wcry tries to make a connection to a certain URL (which wasn’t registered) and if this connection isn’t successful, it will proceed with the encryption of the files. If the connection to this URL is successful, the ransomware will stop and won’t do anything. A security researcher discovered this behavior and registered the URL, deactivating these attacks and avoiding many new infections. However, new versions were seen in the wild without the ‘Kill switch’ strategy, which continue to infect new victims.
MS17-010: the bug behind the attack
On March Patch Day, Microsoft published a critical update in MS17-010, called “Security Update for Microsoft Windows SMB Server,” which detailed that one of the solved vulnerabilities could allow for remote code execution. Initially, it was only available for Windows supported versions, which meant that there wasn’t an update for Windows XP or Windows 8.
A month after the patch publication was released, an exploit called ‘EternalBlue’ was publicly made available by the hacking group ShadowBrokers dump. This exploit is related to MS17-010 and has been used in order to continue spreading this ransomware.
Last saturday, after WannaCry publically hit the news, Microsoft published an emergency update to patch this bug in both Windows XP and Windows 8.
Am I Affected?
As with any other ransomware attack, it is pretty easy to realize that you have been infected: your files will be encrypted and you will see a screen requesting payment. In the case of Wcry malware, it should be a screen like this (or similar):
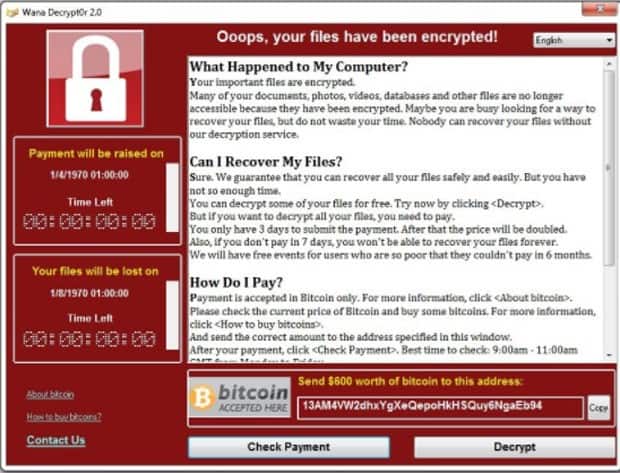
Due to the fact that this vulnerability affects the SMB protocol, only Windows hosts are affected. If your Windows host is supported by the SMB v1 protocol, and you don’t have any security product protecting you, you’ll likely be exposed to this attack.
How do I protect against this?
In order to ensure that you’re protected against Wcry ransomware, the first thing you should do is to immediately install the patchissued by Microsoft. If you are running an older version and it isn’t possible to apply the patch, Microsoft has released some security updates for unsupported versions in this page.
Most Antivirus companies have updated their rules in order to be protected against this attack, so be sure to keep all antivirus software updated too. Also, as a workaround, you can disable the support for SMB v1 to directly block this ports in the firewall.
Generally speaking, when we talk about ransomware, one of the best strategies is to perform backups in order to reduce the damage of the attack, in case you get infected.
Conclusion
Ransomware attacks are becoming a dangerous trend, as they are a quick way for cyberattackers to make money. As previously stated, the most important thing to do in terms of security is to ensure that you have the latest patches applied. People with the MS17-010 patch applied prior to the attack, weren’t affected by the spreading technique used by WCry. It’s very important to reiterate that this patch won’t protect you from downloading an infected file from a location that could be infected by this attack.
WCry will be able to infect your SAP system and encrypt all your data if it’s running on a Windows version which isn’t patched. If your network is not properly secured, the infection of any endpoint of your company could end up encrypting all of your data stored in your SAP system. It is critical to ensure that all the SAP systems have their underlying OS already patched, and if not, it is crucial to develop a plan to patch it immediately.




