How Do You Check Old Hashes in Your ABAP System?
One of the most important things in cybersecurity is safety of the passwords for our systems. In this blog post, we will talk about the report CLEANUP_PASSWORD_HASH_VALUES provided by SAP which allows you to check if your ABAP system contains stored insecure hashes, identifying the records with redundant or insecure hashes on the database and what actions are recommended to take.
This post will focus on analyzing the report “CLEANUP_PASSWORD_HASH_VALUES” that is available from SAP_BASIS 7.00 SP 23 (SAP Note #1458262). It is very useful when you want to check and correct those users who have more than one type of hashes password. As explained in previous posts Checking SAP password strength – part I ABAP and Understanding SAP CODVN H Algorithm, SAP allows you to have more than one type of hashes stored in your system to keep compatibility with older systems. This is possible by setting a parameter called: ‘login/password_downwards_compatibility’. The correct configuration will be explained in the rest of this blog post.
What happens if I have more than one hash type?
SAP updates and improve hashes types because old ones become obsolete and insecure. As we update hash versions in our systems, the old ones are stored by default in our system database. If we don’t delete these old and insecure hashes, our systems are at risk. Configure your systems with the most secure configuration, doesn’t completely ensure that an attacker couldn’t use another hash type stored to take advantage and try to crack the hash to access the system and perform malicious actions.
To make your ABAP systems more secure, SAP provides you with the report: “CLEANUP_PASSWORD_HASH_VALUES”, which can be executed using SE38 transaction.
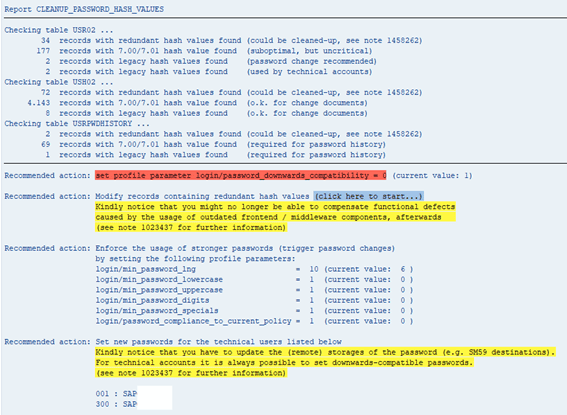
Here, we show the actions that can be performed after running the report. It is important to know that no matter in which client the report runs, the results are cross-client. The report checks three tables on the database: USR02, USH02 and USRPWDHISTORY. The following image shows an example of its output:
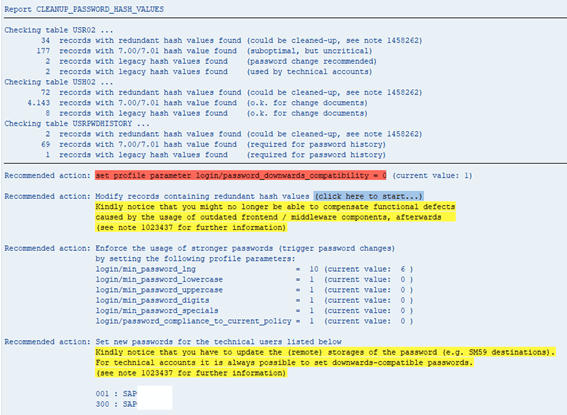
Let’s analyze this line per line to further understand it and determine the next steps we should perform.
Checking Table USR02
Records with redundant hash values
Indicates that there are users with more than one hash type. To know which users are included in these 34 records, query table USR02 with this statement:
SELECT MANDT, BNAME, CODVN
FROM USR02
WHERE CODVN IN (‘G’,’I’)
**Code version “I” is only available for SAP system with 7.02 version or higher.**
Records with suboptimal hash values
Indicates that there are users with hashes not in the last version. In SAP systems version 7.00/7.01 the last hash type available is code version ‘F’. At this moment, the last code version is ‘H’. That is why it indicates that it is suboptimal, but uncritical. To find the users you can execute the next statement:
SELECT MANDT, BNAME, CODVN
FROM USR02
WHERE CODVN = ‘F’
Records with legacy hash values
This first case of legacy hash values indicates that there are users with insecure hashes stored in USR02. The report recommends that you change user passwords, but which users? You can find these users executing this statement:
SELECT MANDT, BNAME, CODVN, USTYP
FROM USR02
WHERE CODVN IN (‘B’,’E’)
AND USTYPE IN (‘A’,’C’)
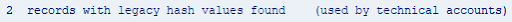
This second case of legacy hash values shows records with insecure hashes that are technical accounts. To find these users, you can execute this statement
SELECT MANDT, BNAME, CODVN, USTYP
FROM USR02 WHERE CODVN IN (‘B’,’E’)
AND USTYPE NOT IN (‘A’,’C’)
Checking Table USH02
This table is used for SAP to store change history for logon data information. Just like the USR02 table, this shows a count of records that have redundant hash values in the USH02 table.
Records with more than one hash value stored
To find these records, you can execute this statement:
SELECT MANDT, BNAME, CODVN
FROM USH02
WHERE CODVN IN (‘G’,’I’)
Records with suboptimal hash value
The second line shows the records with hashes not in the last version. It is the same case as the USR02 table. This is the statement that you can execute to view records in detail:
SELECT MANDT, BNAME, CODVN
FROM USH02 WHERE CODVN = ‘F’
Records with legacy hash values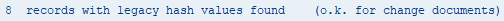
The last line for table USH02 shows records with insecure hashes stored. To find these records in the SAP database, you can execute this statement:
SELECT MANDT, BNAME, CODVN, USTYP
FROM USH02
WHERE CODVN IN (‘B’,’E’)
Checking Table USRPWDHISTORY
Records with more than one hash value stored
The last check analyzes the USRPWDHISTORY table. The checks are the same as the ones for USH02. To visualize these records, this is the statement that you can execute:
SELECT MANDT, BNAME, CODVN
FROM USRPWDHISTORY
WHERE CODVN IN (‘G’,’I’)
Records with not the last hash version type
Find these records with:
SELECT MANDT, BNAME, CODVN
FROM USH02
WHERE CODVN = ‘F’
Records with legacy hash value found
Perform the following query:
SELECT MANDT, BNAME, CODVN, USTYP
FROM USRPWDHISTORY
WHERE CODVN IN (‘B’,’E’)
Recommendations
At the end of the report, we can see different recommended actions that we can follow.
- Set parameter ‘login/password_downwards_compatibility’

The first recommended action is related to ‘login/password_downwards_compatibility’ parameter. If you have configured the parameter with a different value than recommended, the report will show it. To configure with the recommended value, you need enter into RZ10 transaction, change the parameter, save the profile and reboot the application server service.
2. Delete all redundant hashes values

Other recommended actions are about modifying records containing redundant hash values. To perform this action, you only need to click in the message ‘(Click here to start…)’ and then confirm in the pop-up the action.
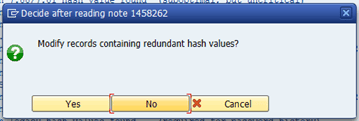
Once the action is confirmed, the report will show you the processed records.
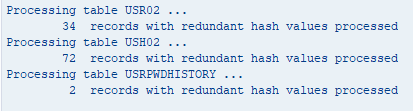
3. Set password policy parameters with recommended values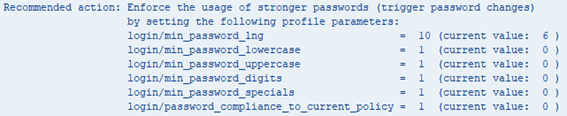
Another action aims to enforce the usage of stronger passwords. This section recommends parameter values and shows the current value that is configured in the system.
4. Set new password for technical accounts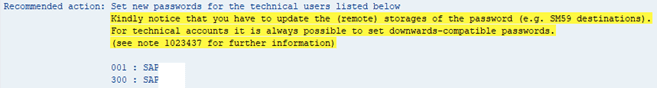
The last one recommends to change or set new passwords for the technical users listed. To set new password to these account users, it is necessary that you previously set with the recommended value ‘login/password_downwards_compatibility’ parameter and have SAP system with the last hash version type.
Conclusion
At Onapsis, we are committed to providing our customers with the best recommendations and solutions for the security of their SAP systems. Therefore, we have a module in the Onapsis Security Platform (OSP) that allows you to identify all those users who have insecure hashes and provide the appropriate solutions for your system.
It is very important to understand the risk of having redundant and unsafe hashes, what can expose our SAP systems to brute force or rainbow table attacks. Perform regular checks to your clients, increase the security in your system and reduce the possibility of the previously mentioned attacks. Do not hesitate to ask us for more information about how OSP can protect your business-critical applications.

