Common Vulnerabilities in SAP Systems

Missing Authorization Checks, Information Disclosure, and Cross-Site Scripting (XSS) were the top three patched vulnerabilities in 2025. Missing Authorization Checks alone accounted for nearly one-third of all security notes, as many SAP functionalities fail to default to protected states. These flaws leave systems exposed to data theft, unauthorized modification, and service disruption, making timely application of SAP Patch Day notes critical for maintaining confidentiality, integrity, and availability.
As organizations review their privacy commitments this week, the data below serves as a technical reality check. Privacy regulations like GDPR and CCPA are unenforceable if the underlying applications fail to verify user permissions. The prevalence of “Missing Authorization Checks” in 2025 highlights a critical gap between corporate privacy policies and the actual security controls protecting sensitive data.
Analyzing the 2025 SAP Vulnerability Landscape
Previous blog posts highlighted the importance of protecting SAP applications due to the strong presence of SAP in the global economy and the high sensitivity of the data that is being manipulated in such systems. With that in mind, we will analyse today the top vulnerabilities patched by SAP in the year 2025 from the perspective of the impact that can be caused by such an attack. Onapsis Research Labs actively participated in this process by providing a significant number of vulnerability findings, leading to the achievement of being mentioned in SAP’s credits each month of 2025, resulting in 23 out of 24 possible mentions in the last 2 years.
The following chart shows the breakdown of last year’s security notes released during the monthly SAP Patch Day. Most common patches are by far associated with Missing Authorization Checks, which represent almost a third of the total vulnerabilities reported. This is due to the broad range of SAP functionalities that should but fail to be protected from unauthorized access. The second and third most commonly patched vulnerabilities are Information Disclosure and Cross-Site Scripting, both of which occupy between 11-12% of the total number of patches. The remainder 48% consists of a selection containing the Critical Deserialization Vulnerability, Path Traversal vulnerabilities, Open Redirect vulnerabilities and others.
While the vulnerabilities discussed today are more likely to appear in a Patch Day post, all SAP clients are strongly advised to follow the recommendations indicated by the notes in order of their specified priority.
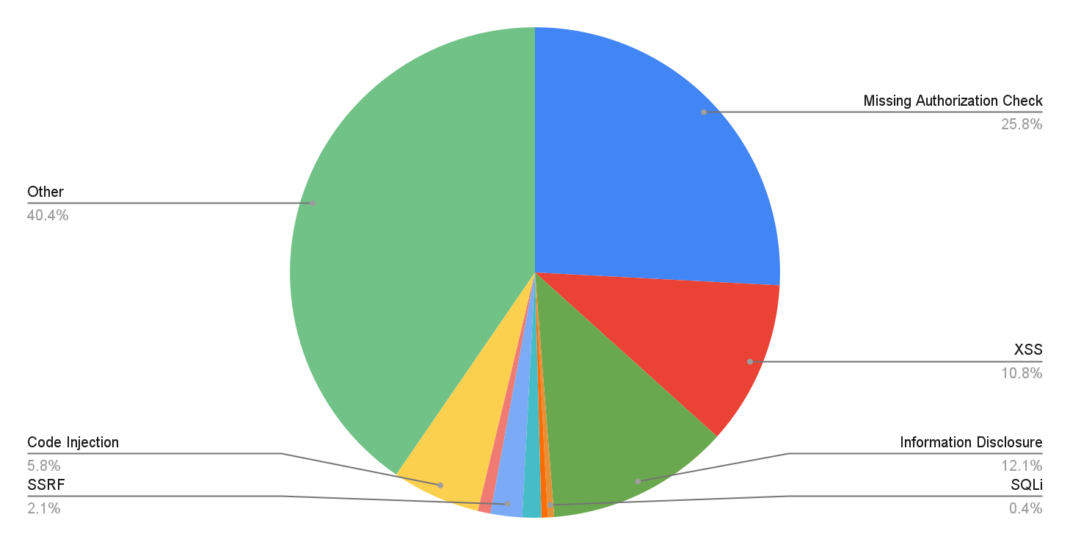
Top 3 most commonly patched SAP vulnerabilities
Missing authorization check
As the name suggests, vulnerabilities of type Missing Authorization Check are described by a lack of proper protection of resources against unintended usage. This directly impacts the CIA triad (Confidentiality, Integrity, Availability) based on the vulnerable functionality. These metrics, as defined by the Common Vulnerability Scoring System (CVSS), describe the impact caused by a successful exploit to the vulnerable component.
Impact on the CIA Triad
- Confidentiality: the amount of sensitive information that is exposed to the attacker after a successful exploit. By sensitive information, we indicate the data that should be protected through the appropriate access controls.
- Integrity: the veracity of the information is directly affected, the attacker can exploit the vulnerable component in order to modify sensitive information.
- Availability: the accessibility to the service is restricted or the service is rendered unavailable, causing legitimate users to face issues in accessing sensitive information and/or functionalities.
Real-World Exploitation Scenarios
A malicious actor might be able to perform user enumeration (display a list of valid usernames in the system), as shown in SAP note 3656781, permanently remove data from the system (SAP note 3608991), or read sensitive data with escalated privileges (SAP note 3474590). This is a small set of possible exploitation scenarios that exhibit a wide range of malicious actions that can be performed in the context of improper authorization.
Another important component of impact assessment is whether this malicious actor performs the actions with prior authentication or not. While this is not a direct requirement for exploiting a Missing Authorization vulnerability, it impacts the overall CVS, an unauthenticated attack will always be rated higher due to the removal of the extra steps needed for them to achieve a valid session. This rule applies to any reported vulnerability, regardless of its type.
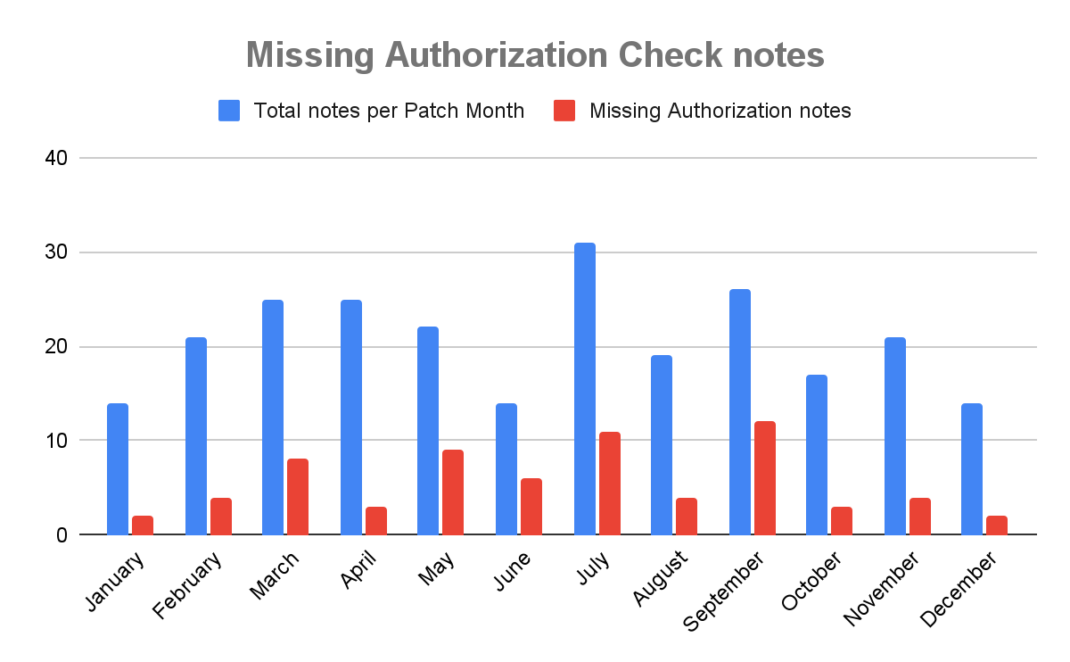
The dispersion of this year’s SAP notes including Missing Authorization Check patches can be seen in the following graph. In months like September, they represent up to half of the total patch notes.
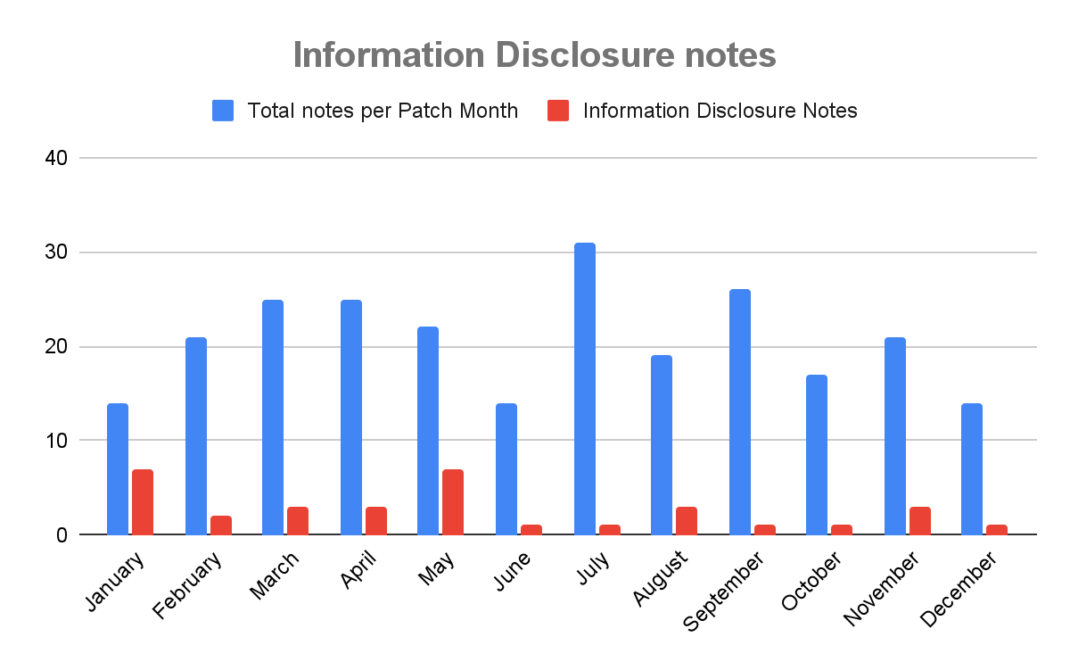
Information Disclosure
The second most commonly talked about vulnerability is described by the leakage of sensitive data . The Confidentiality component of the CVS is impacted; this impact can be classified as Low, when the obtained information does not directly impact the attacked component (as shown in SAP note 3568307), or High, when the information can be used to cause serious damage to the system (SAP note 3601480).
While the exploit of a component vulnerable to Missing Authorization Check often leads to the disclosure of sensitive information, as we have discussed in the previous section, it is not compulsory for Information Disclosure to be a direct cause of Missing Authorization Check. A configuration error, as exemplified by SAP note 3561264, can lead to information leakage. While sometimes the information obtained might not seem relevant, a skilled attacker will utilize any detail to find an entrypoint into the system; in this specific note, the server is configured to respond differently based on the user that performs the operation. This allows an attacker to produce a list of valid usernames that can later be specifically targeted.
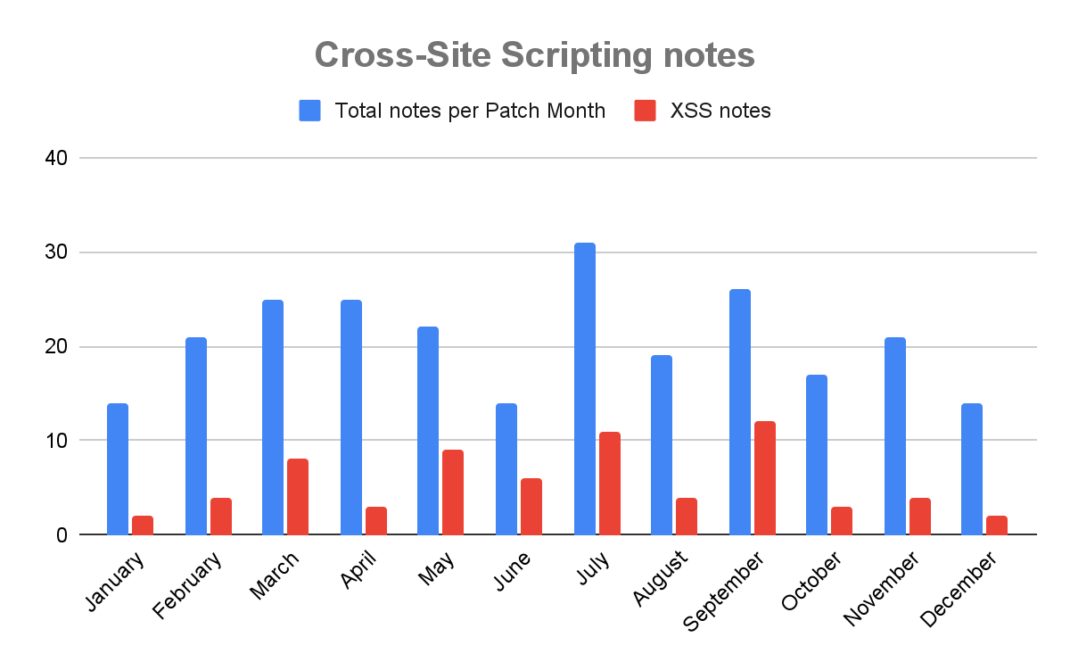
XSS
Cross-Site Scripting, abbreviated as XSS, is the third most patched vulnerability this year by SAP. It is characterised by the possibility of inserting (and successfully executing) malicious scripts into trusted sources.
Consequences of XSS Attacks
By exploiting an XSS, the attacker can access and modify page contents (as described in SAP note 3647098), which can lead to website defacing, where the attacker controls the HTML content of the victim page. A naive user can be tricked into executing malicious requests masked as legitimate.
Conclusions
Onapsis Research Lab continues to support SAP in the process of securing their products by diligently seeking vulnerabilities and crafting exploits mimicking malicious actors. The monthly SAP Patch Day is an important event for security experts as well as SAP customers who are strongly advised to carefully follow any recommendations stated within the patch notes.
Honorable mentions
Deserialization
The most notable vulnerability family of 2025, by criticality, is the Deserialization Zero-Day from the first half of 2025. The campaign rolled out by Onapsis detailed the timeline of the CVE, provided analysis of the public exploits and delivered tools for their customers with the goal of minimising the negative impact. It was a continuous effort to ensure that the patches provided by SAP are sturdy against possible attacks.
Code Injection
A vulnerability from the Code Injection family, as depicted in SAP Note 3685270, can lead to attackers gaining full control over the system. Although not as common as the other discussed vulnerabilities, it is mandatory to follow SAP’s solutions due to the high CVSS score.
Frequently Asked Questions (FAQ)
What was the “NetWeaver Zero-Day” (CVE-2025-31324)?
The NetWeaver Zero-Day was a critical vulnerability discovered in early 2025 affecting the SAP Visual Composer component. It allowed unauthenticated attackers to upload malicious files (webshells) and execute arbitrary commands on the server. Because it required no login credentials and granted full system control (“adm” privileges), it was weaponized by ransomware groups within hours of disclosure.
Why is Insecure Deserialization considered the most dangerous SAP attack vector?
Insecure Deserialization flaws (like CVE-2025-30012) are dangerous because they often carry a perfect CVSS score of 10.0. They allow attackers to manipulate serialized data objects sent to the SAP Java stack, forcing the application to execute malicious code without checking if the user is authorized. These attacks are notoriously difficult for standard Web Application Firewalls (WAFs) to detect because the malicious payload is hidden inside legitimate-looking traffic.
How do attackers exploit SAP RFC interfaces?
Remote Function Call (RFC) interfaces are the “bridges” between SAP systems. Attackers exploit them via “Supply Chain Attacks.” By compromising a less-secure satellite system (or a third-party add-on), they can ride the trusted RFC connection into the core S/4HANA environment. Since many organizations do not monitor internal RFC traffic, this lateral movement often goes undetected until data is exfiltrated.
If I applied the patch for a Zero-Day, am I safe?
Not necessarily. In 2025, the speed of exploitation meant that many systems were compromised before the patch could be applied. If an attacker deployed a webshell or created a backdoor user during that window, applying the patch later closes the front door but leaves the intruder inside. This is why you must scan for Indicators of Compromise (IoCs) and post-exploit artifacts, not just missing patches.

