Black Hat 2021: Onapsis Research Labs Shares Learnings
Hi everyone!
Yvan, Nahuel and Pablo from the Onapsis Research Labs are back! This time, we’re here to share our experiences at Black Hat USA 2021. This year, we held a four-day training where students started with basic SAP concepts and, over the course of the session, elevated their game to use the most critical, latest, and advanced exploits against these systems.
We had four great days of training in an intimate setting. All of our trainees had a strong technical background; some more focused on pentesting and others focused on SAP security.
During our first day, we started with some SAP basics and the different techniques needed to perform a recognition phase. The first half of the day was familiar to those who had already worked with SAP and knew these basic concepts. So the fun really began during the second half of the day, where trainees learned how to do recon and identify SAP systems and their processes in a black-box way.
By far, the second day was one of the more interesting ones for us. We had the opportunity to teach our students about different vulnerabilities as well as how to assess…and abuse them. We even talked about bugs that the Onapsis Research Labs recently discovered and showed them our discovery path to find them. Sharing our experiences in penetration testing (“pentest”) projects and highlighting which vulnerabilities are usually the ones that allow us to gain access to the system without providing credentials led to some great conversations with the group about their experiences from the SAP administrator side.
On day three, we focused primarily on the “elevation of privilege” phase of a pentest, where students learned several techniques that Onapsis Research Labs use in every pentest we perform. This was, arguably, the most challenging exercise but also the most important part as it demonstrates the most valuable SAP-related tricks used in every successful project.
A big part of the fourth day was devoted to forensics, where we discussed several sources of information SAP provides and how to read and understand them. We finished this section with a big exercise where the students had to detect and track all the steps that a real attacker had made.
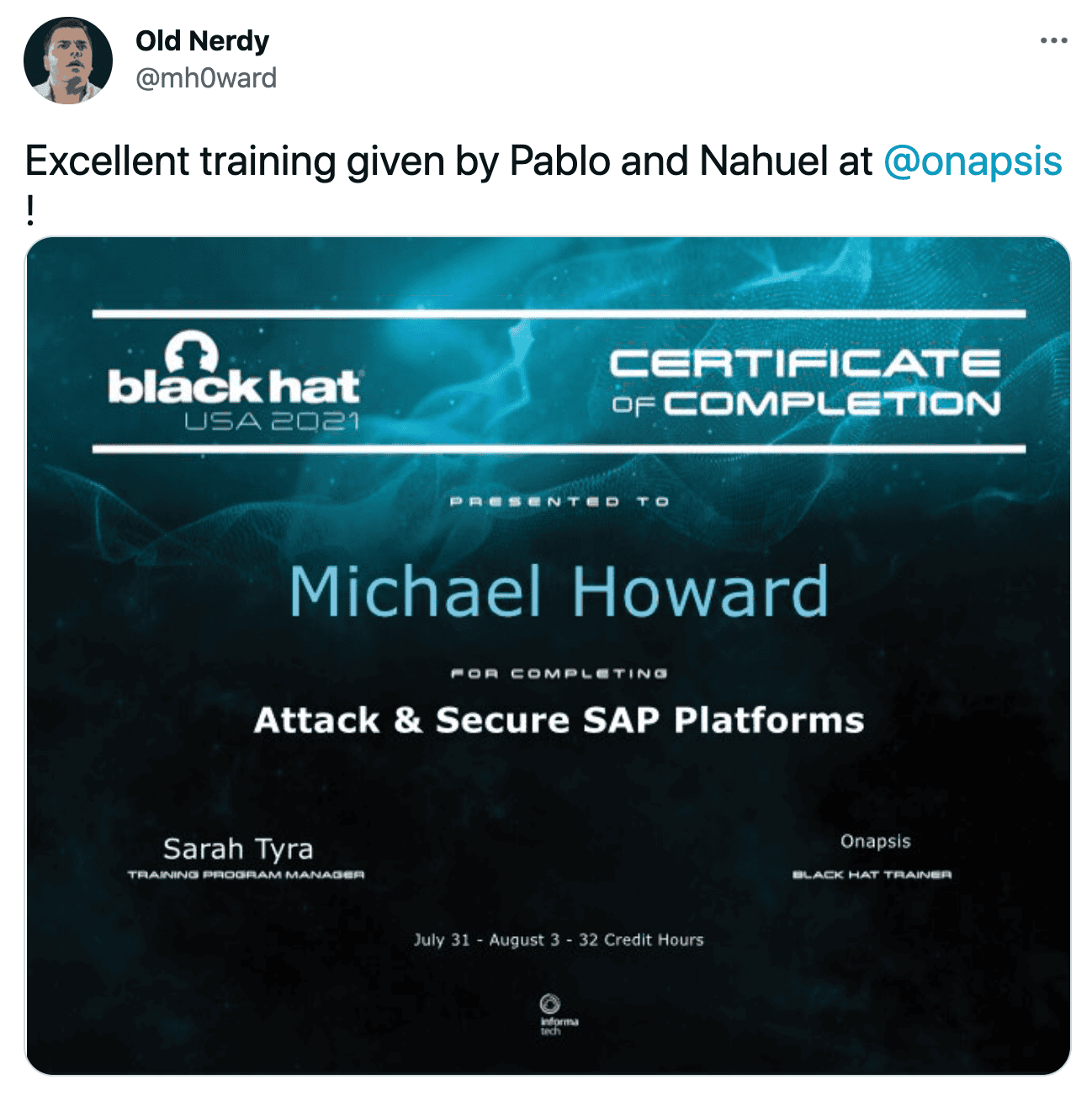
We had a fantastic group of students and we loved working with them throughout the course. Looks like the feeling was mutual too! (Thanks @mh0ward!)

So now, after a really intense few days, it’s time to take a quick rest…but not for long, as we need to keep updating our training with new fresh content and new cutting-edge vulnerabilities. See you in the next training session!
Cheers!
Yvan, Nahuel & Pablo
Additional Resources
- Onapsis Research Labs is continuously updating The Onapsis Platform to incorporate newly published vulnerabilities into the product so that our customers can protect their businesses.
- For more information about the latest SAP security issues and our continuous efforts to share knowledge with the security community, subscribe to our monthly Defender’s Digest Newsletter.
- This joint report from Onapsis and SAP analyzes how threat actors are actively targeting unprotected SAP applications.
- Onapsis and SAP address how to protect your organization’s business-critical applications from the looming threat of ransomware.
