Daniel Antonelli
Daniel Antonelli is a cybersecurity professional specializing in security research and vulnerability management. With a focus on protecting critical business systems like SAP, Daniel has contributed to enhancing the security posture of organizations across industries. His expertise in identifying and mitigating cyber threats, coupled with a deep understanding of enterprise IT environments, makes him a key player in advancing cybersecurity efforts and ensuring the resilience of complex infrastructures.
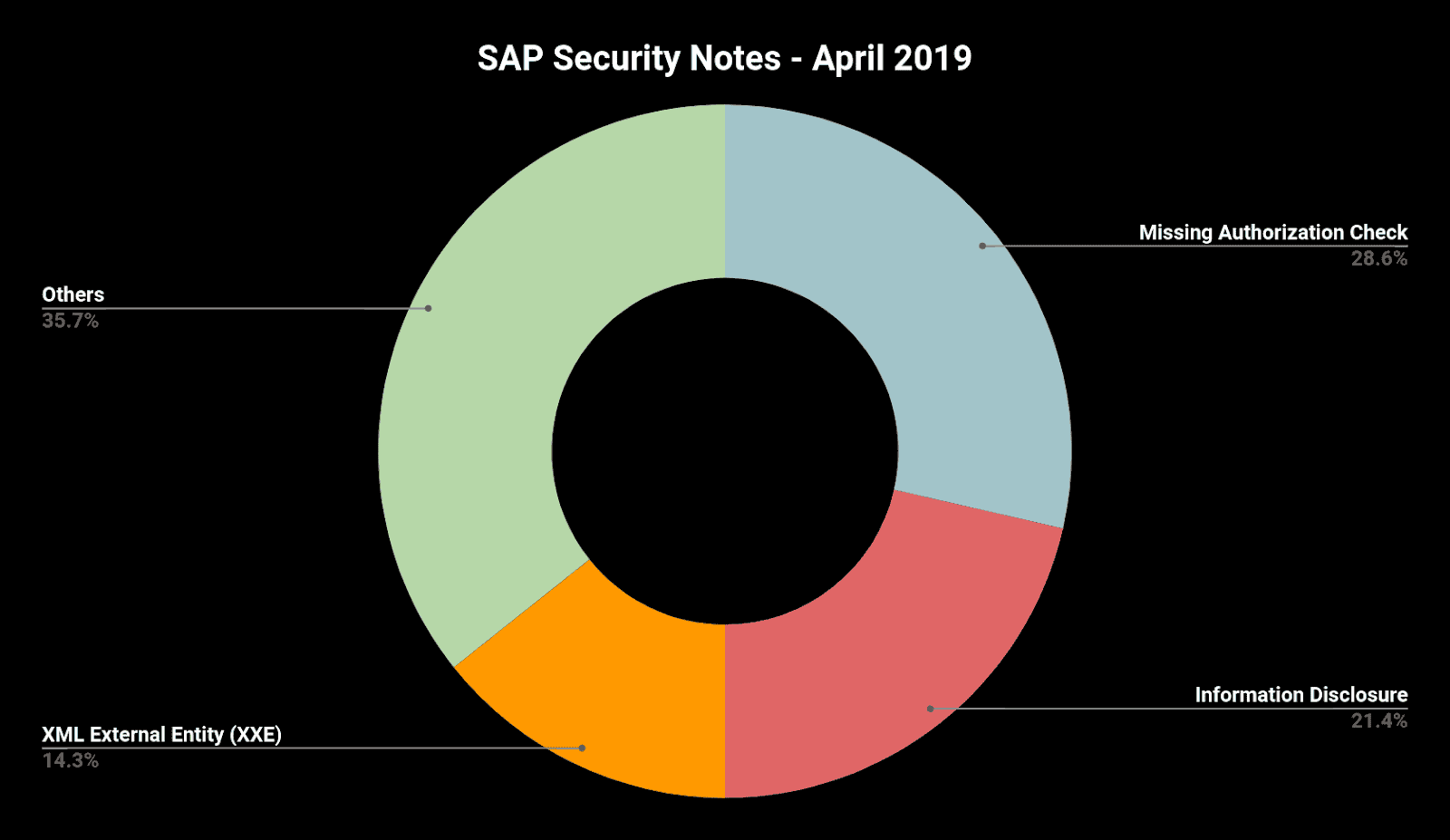
SAP Security Notes April ‘19: SAP Expands XXE Critical Patch to JAVA and HANA
Our monthly report on how to improve your SAP security and take care of your most critical information by exploring the latest SAP Security Notes for April 2019.
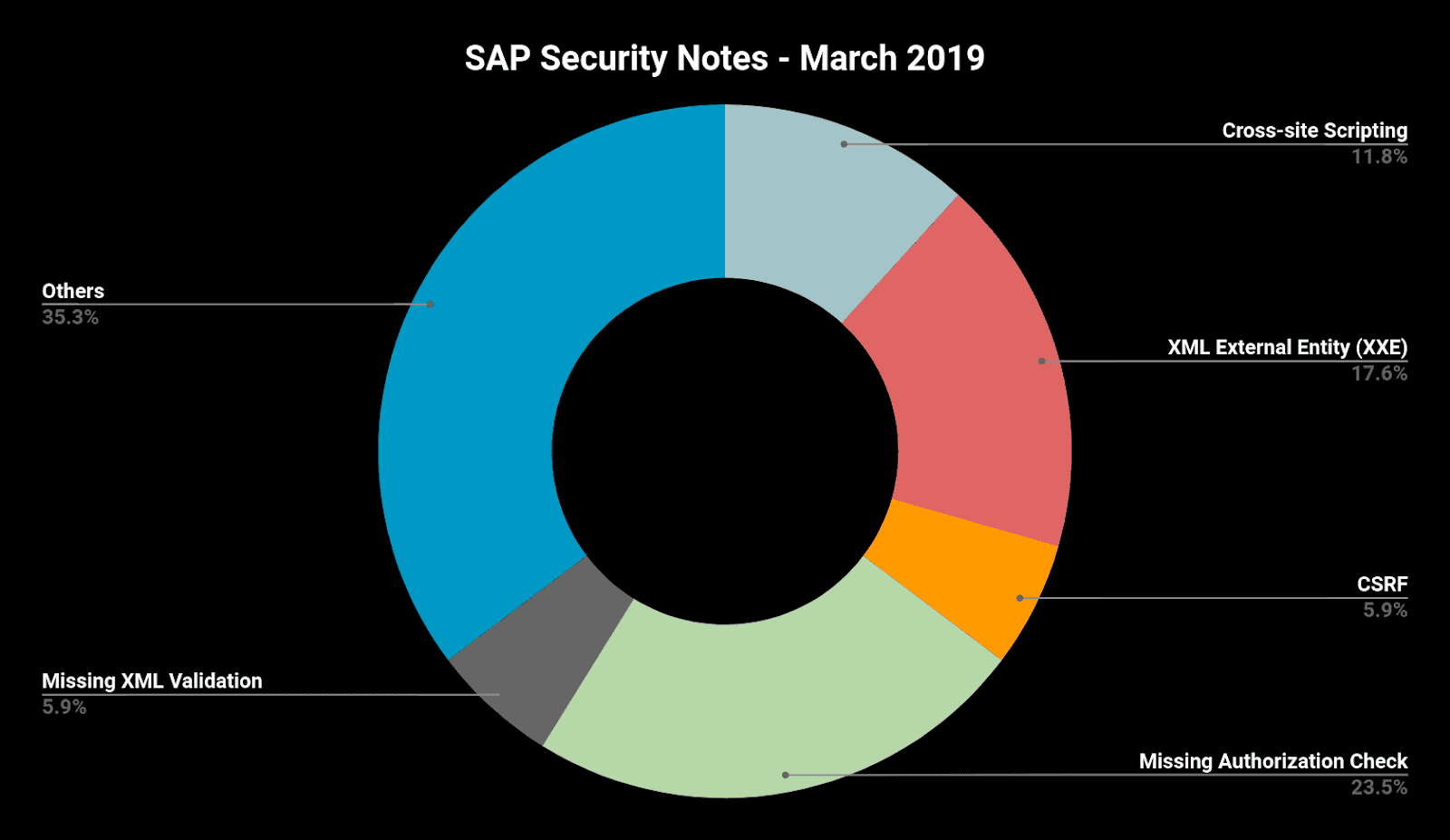
SAP Security Notes March ‘19: Critical Bug Affecting SAP HANA XSA
Our monthly report on how to improve your SAP security and take care of your most critical information by exploring the latest SAP Security Notes for March 2019.
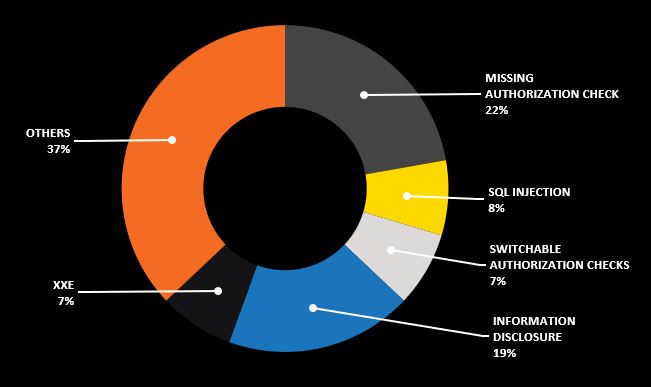
SAP Security Notes February ‘19: Several Critical Onapsis Reported Bugs Patched
Our monthly report on how to improve your SAP security and take care of your most critical information by exploring the latest SAP Security Notes for February 2019.
SAP Security Notes August ‘18: SQL Injection in BusinessObjects and Several High Priority Notes to take care of.
Our monthly report on how to improve your SAP security and take care of your most critical information by exploring the latest SAP Security Notes for August 2018.
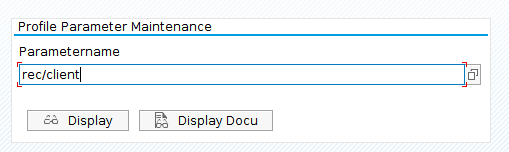
SAP Table Change Logging: Configuration, Security Risks, and Auditing
The goal of this blog post is to help you understand the importance of enabling the Table Change Logging in your SAP system and the risks that exist if you choose not to enable it.
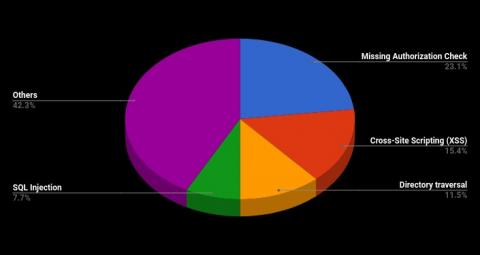
SAP Security Notes Feb ‘18: Onapsis Helps SAP Patch Several Vulnerabilities in HANA XS Advanced
Our monthly report on how to improve your ERP security and take care of your most critical information housed in SAP by exploring the latest SAP Security Notes.
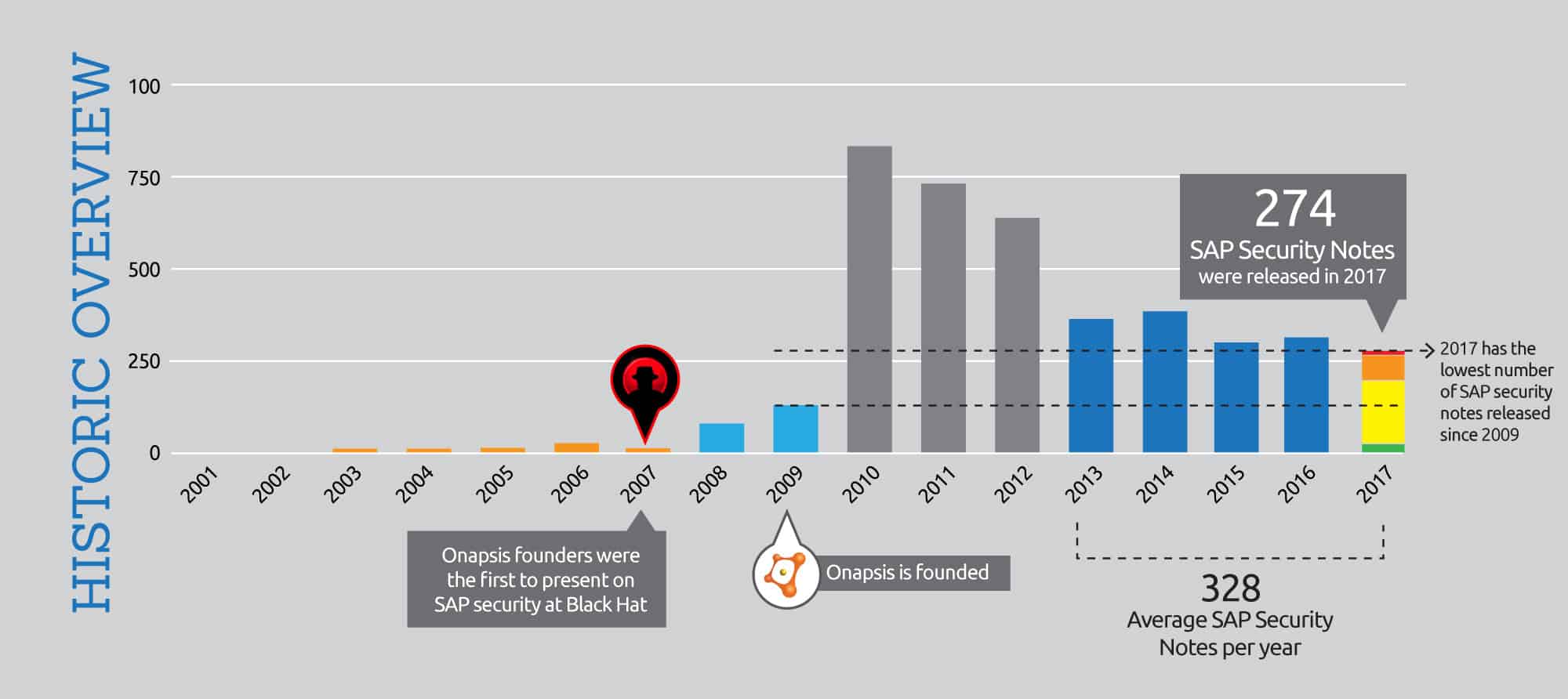
SAP Security Notes 2017: Trends Towards Stability, What it Means For Your Security Strategy
An overview of SAP’s 2017 Security Notes and how it may affect your security strategy for 2018.

TMSADM User with Default Password: Another Risk in Your SAP System
What the SAP security implications of having TMSADM enabled with default passwords and how can you properly protect it?
