Active Exploitation of SAP Vulnerability CVE-2017-12637

Executive Summary
- CISA warned organizations about the active exploitation of CVE-2017-12637 on March 19, 2025.
- Onapsis Research Labs (ORL) identified active exploitation of this vulnerability via its global SAP Threat Intelligence Network and briefed both SAP and CISA on observed malicious activity.
- This known vulnerability was initially patched by SAP in 2017. However in some cases, installations could be exposed despite the patch being applied, as warned by SAP in 2024.
- This vulnerability affects the SAP Netweaver AS Java Application Server, which is designed to be internet-facing.
- CVSSv3 of this vulnerability is 7.7. That being said, an unauthenticated attacker can use it to fully compromise a vulnerable SAP system, making it absolutely critical to address.
From A CVSS 7.7 to Full SAP Application Compromise
The Onapsis Research Labs has observed that this vulnerability is being actively exploited in the wild, and even more, threat actors have demonstrated extensive knowledge about the affected SAP systems, using the vulnerability to obtain critical SAP configuration files from the operating system.
The nature of this particular directory transversal vulnerability allows an attacker to extract system files including credentials or the SAP Secure Store that can directly result in full system compromise.
Understanding CVE-2017-12637
SAP systems are big and complex, with a lot of components interacting with each other and external systems to provide the high number of services and features that it handles as a critical business application. Consequently, administrators face a challenging task as they must ensure that security measures are implemented effectively. This complexity arises from potential misconfigurations, patches that necessitate manual adjustments such as component deactivation or upgrades, user role management, and access control just to mention some of the security aspects.
A good example of this is the SAP Security Note 2486657, which fixes the vulnerability CVE-2017-12637, a path traversal vulnerability that allows an attacker to retrieve arbitrary files that the SAP system user has access to. This vulnerability affects SAP CPS 8.0 and the note recommendation is to apply the following patches:
- ENGINEAPI 7.50 SP02
- ENGINEAPI 7.50 SP03
- ENGINEAPI 7.50 SP04
- ENGINEAPI 7.50 SP05
Afterward, this specific component was rebranded—from SAP CPS V8 to SAP BPA V9, as described in the SAP Note 2278834 (from 2021)—so an administrator is required to fully replace this component with the new one.
The story doesn’t end there. In 2024, SAP released SAP Note 3476549, which highlights a ‘Directory Traversal’ vulnerability in the SAP NetWeaver AS Java system for a specific URL, even if the system version is higher than the patch level in SAP Note 2486657. The note advises SAP system administrators to verify if the vulnerable component is still active. If so, it provides options and links to previous notes about upgrading or deactivating the component. Simply applying a patch may not be enough, as the vulnerable component could remain active and continue to receive requests.
This demonstrates how complex and dynamic it can be to implement a fix or workaround for an SAP system, and all the required efforts from a security perspective.
With a vulnerability CVSS score of 7.7, a threat actor can abuse this vulnerability to easily escalate the initial access, obtaining critical files that could potentially provide valuable information about the system, or even highly privileged user credentials stored in the system files.
Last week, CISA updated the Catalog of Known Exploited Vulnerabilities (KEV), highlighting the active exploitation of this CVE:
Update to the Catalog of Known Exploited Vulnerabilities by CISA on CVE-2017-12637
Anatomy of the Attack(s)
The exploitation of CVE-2017-12637 is performed over HTTP(s), and its test is straightforward; an attacker can execute a GET method to the affected URL with a typical path traversal exploit.
Due to the fact that SAP Netweaver Java is the base platform for applications like SAP Portal, it is designed and expected to be internet-facing. As a result, the probability and frequency of exploitation of this vulnerability is extremely high.
Attackers targeting a specific SAP application can obtain arbitrary files from the system, and some threat actors observed by the Onapsis Research Labs have demonstrated extensive knowledge of SAP systems.
Attackers probe multiple SAP system URL(s) for known vulnerabilities. Upon identifying a system vulnerable to CVE-2017-12637, attackers immediately begin exfiltrating SAP system-specific files.
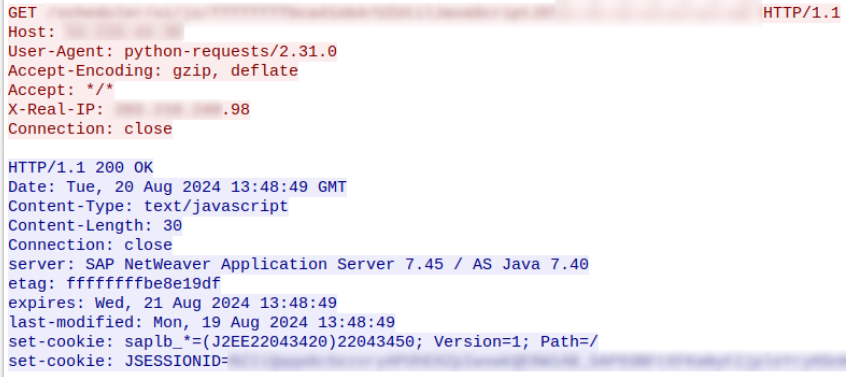
Attacker exploitation with positive result
It’s important to mention that this security flaw allows not only exfiltration of text files, but also binary files, including critical files such as the SAP Secure Store, to obtain highly privileged SAP user credentials.
After downloading the SAP Secure Store, attackers leveraging CVE-2017-12637 are able to use publicly available tools to decrypt the contents of the password storage and obtain highly privileged SAP credentials that would grant them full access to the unprotected SAP application.
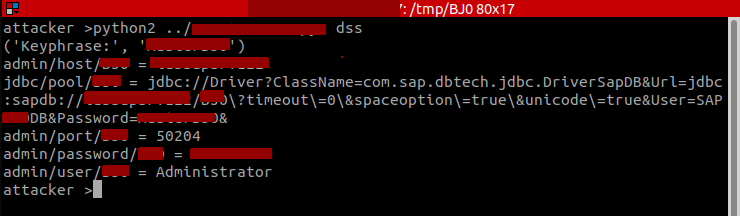
Decryption of the SAP Secure Store file using publicly available tools
After successful decryption, the attacker can login to the SAP Application through a web browser, or the SAP Database depending on the level of connectivity achieved:
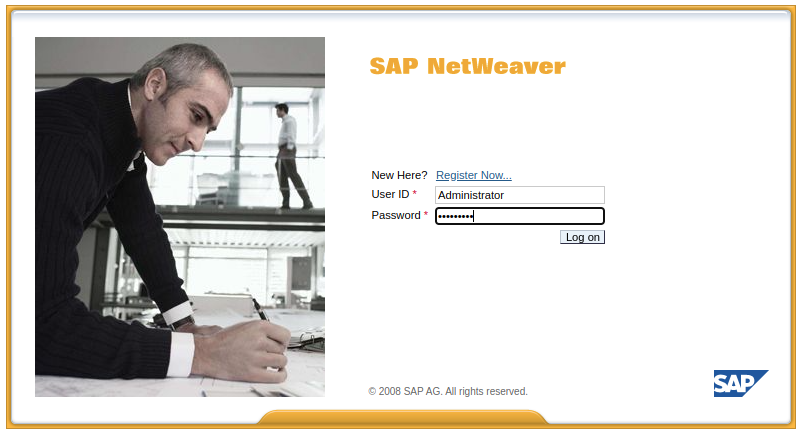
Login to the SAP Application using decrypted credentials.
This demonstrates the importance of having continuous monitoring and proper protection capabilities in place to identify the existence of deprecated components or misconfigurations, including ones related to old SAP security vulnerabilities.
Next Steps & Actions to Take
Listen to our On-Demand Webinar here.
It’s important for organizations to review the relevant SAP Notes: 2486657, 2278834 and 3476549, since a successful exploitation allows attackers to extract any file from the affected system, including ones that might be used to completely compromise the system. Due to the complex nature of SAP systems and the interaction of their numerous components, continuous monitoring and in-depth scans of system configurations and patches are required to ensure comprehensive protection.
For more information on patching and critical SAP security updates, be sure to check our SAP Patch Day archives to stay up to date on the latest fixes and recommendations.
Appendix: MITRE ATT&CK Mapping
Mapping the active exploitation of CVE-2017-12637 to the MITRE ATT&CK framework can help defenders model this behavior and protect organizations against active threats:
| Mitre Technique ID | Technique | Artifact |
| T1190 | Exploit Public-Facing Application | CVE-2017-12637 exploited to perform arbitrary file access on the target Operating System. |
| T1083 | File and Directory Discovery | Through the attempt to access multiple directories and files, the attacker can map available resources at the Operating System level. |
| T1592 | Gather Victim Host Information | Through the exploration of Operating System Files, it is possible for attackers to identify the underlying OS, its version and installed software, to mention a few examples. |
| T1555 | Credentials from Password Stores | The SAP Netweaver Application Server Java stores sensitive information in encrypted password stores, that can be decrypted if access to the OS is possible. |


