Build Clean Code Security Gates with Git Repository Scanning
Strengthen Your SAP Code Security at the Source

Strengthen Your SAP Code Security at the Source

Minimize Hidden Risks in modern SAP Custom Code development

Onapsis Control for Code has helped them maintain more compliant and secure system landscapes, contributing to overall stability and risk reduction.

This webinar provides security professionals with an in-depth, educational look at both the latest tactics, techniques, and procedures used by threat actors to directly attack SAP, as well as the next-gen methodologies and tooling required to defend against them.

This webinar provides security professionals with an in-depth, educational look at both the latest tactics, techniques, and procedures used by threat actors to directly attack SAP, as well as the next-gen methodologies and tooling required to defend against them.
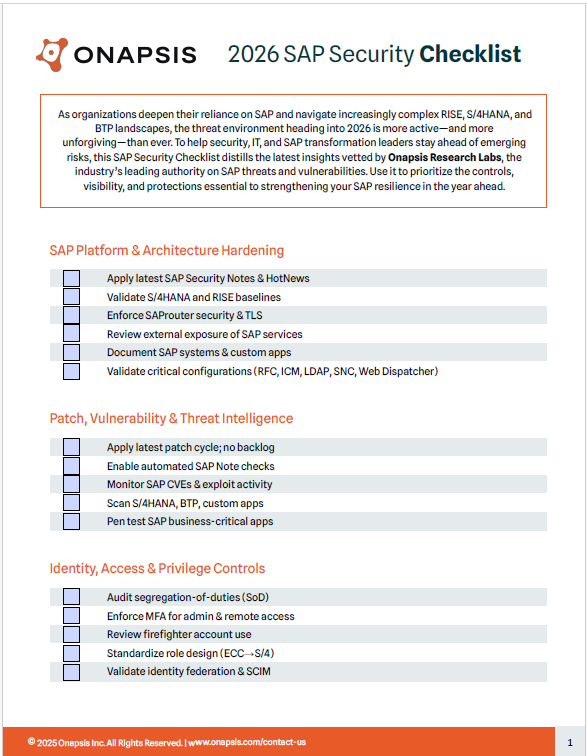
Onapsis 2026 SAP Security Checklist: Secure your S/4HANA, RISE, and BTP landscapes against emerging threats. Prioritize critical controls for platform hardening, patching, access management, monitoring, and cloud security.

JP Perez-Etchegoyen and Paul Laudanski from Onapsis Research Labs (ORL) recap the top SAP security vulnerability trends from 2025, provide an anatomy of real attacks to SAP Applications, and share practical guidance to help you strengthen your SAP defenses for 2026.

JP Perez-Etchegoyen and Paul Laudanski from Onapsis Research Labs (ORL) recap the top SAP security vulnerability trends from 2025, provide an anatomy of real attacks to SAP Applications, and share practical guidance to help you strengthen your SAP defenses for 2026.

Onapsis Defend & Microsoft Sentinel solution for SAP