Code Vulnerability Analysis
for SAP
Introduction to SAP Code Vulnerability Analysis
SAP Code Vulnerability Analysis plays a pivotal role in ensuring the security and integrity of SAP applications, which are vital components of many enterprises. As organizations increasingly rely on SAP systems to manage critical business processes and sensitive data, the need to identify and address potential vulnerabilities, such as ICMAD and P4CHAINS, becomes paramount. SAP code vulnerabilities can expose applications to a range of security risks, including data breaches, unauthorized access, and service disruptions. Therefore, conducting a comprehensive analysis of the code underlying these applications is essential to proactively identify weak points and mitigate potential threats.
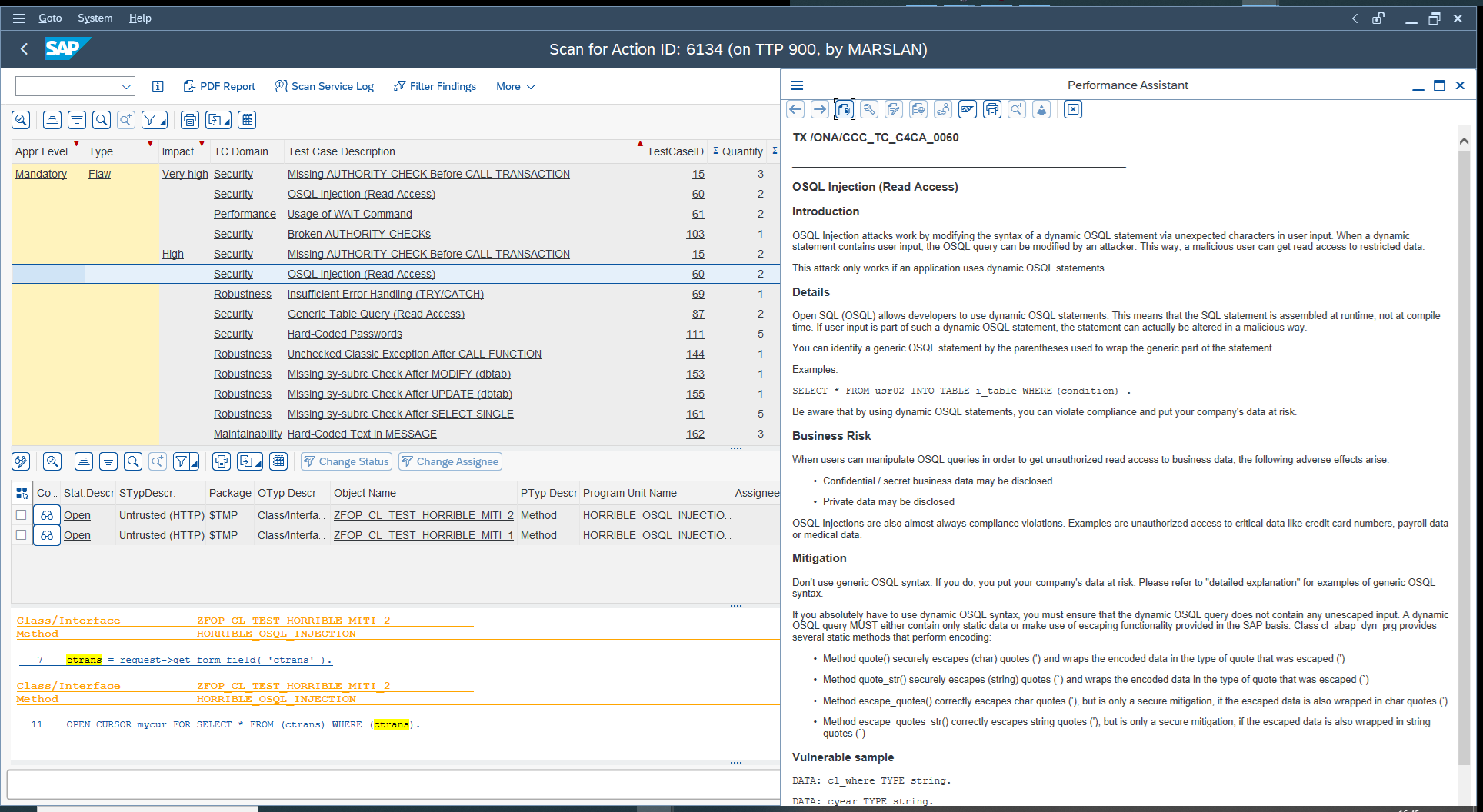
Leveraging static code analysis tools for vulnerability detection
Leveraging static code analysis tools for vulnerability detection is a proactive and automated approach to identifying potential security issues and vulnerabilities in software code during the development phase. Static code analysis involves analyzing the source code of an application without executing it. This process helps developers and security professionals find security flaws, coding mistakes, and vulnerabilities that could be exploited by malicious actors. When applied to SAP development, these tools specifically focus on analyzing the code within SAP applications to uncover vulnerabilities unique to the SAP environment.


Integrating code review into the SAP development lifecycle
Integrating code review into the SAP development lifecycle is essential for ensuring the security, quality, and reliability of SAP applications. Code reviews help identify and address vulnerabilities, improve code quality, and promote collaboration among development teams. Here are just a few ways on how to effectively integrate code review into the SAP development lifecycle:
SAP Code Vulnerability Scanning Tools from Onapsis
Onapsis Control is a platform designed to assess and manage the security and compliance of SAP environments. It helps organizations identify and remediate vulnerabilities, misconfigurations, and compliance issues within their SAP system.
Within Onapsis Control, there are five product aspects:
FAQs about SAP Code Vulnerability Analysis
Part of the Onapsis Platform
Crafted to streamline ERP security, Onapsis offers a renowned, comprehensive application security suite. Fueled by the unparalleled threat intelligence from Onapsis Research Labs and over a decade of ERP security proficiency, the Onapsis Platform unveils the entire SAP or Oracle attack landscape. This empowers global organizations to enhance risk comprehension, safeguard vital systems, promptly counter threats, and ensure uninterrupted operations for business-critical applications and digital transformation endeavors.
Not quite ready for a live demo, but want to see Onapsis Control in action?
View this two-minute on-demand video of Control to see how we can solve your organization’s unique challenges.
In this video, you will: