Avoid Import Errors, Business Outages, Downgrades, Security Vulnerabilities and Compliance Violations by Inspecting all Transports Before Import
How Onapsis Transport Inspection Works
Onapsis transport inspection is based on over 150 test cases that have been developed over many years of experience with customer projects, focusing on five main areas security, compliance, robustness, maintainability and data loss prevention. Addressing transport issues from multiple angles helps ensure your applications remain secure, compliant and stable. Below are some examples of what is covered by each area.
Security
- Identifies hidden transport content, deactivation of authority checks, unnoticed execution of reports and function modules after import, manipulation of logical file, path definitions, jobs and OS commands
Compliance
- Reports on missing authorization group in maintenance dialog or table, inadequate settings for table logging and client dependent tables
Robustness
- Checks for completeness of all objects, downgrades, correct versions of referenced objects, accidental deletion and overwriting of table content and forecast of critical database activities
Maintainability
- Detects missing packages and namespace definition, invalid or missing repair key for namespace definition, modification of SAP objects and third-party objects, Cl-includes and append structures of SAP tables
Data Leak Prevention
- Generates warnings in case of table data with password hash values, information about the personal security environment (PSE), HR master data and critical HR customizing
All discovered issues include a level of criticality, an explanation of the vulnerability, business impact and remediation guidance. This gives you essential context to understand if you want to accept the risk and how to prioritize remediation for those findings you elect to fix.
Transports, although essential for SAP change management, can also introduce harmful or incorrectly configured content that puts system security, compliance and stability at risk. Onapsis helps mitigate these risks by inspecting every transport (including third- party) before it is released or imported and continuously monitoring the transport queue for critical security findings.
- Prevent system downtime, damage to target systems, import errors and downgrades
- Protect sensitive data from manipulation and espionage, which could result in security or compliance violations
- Find issues earlier when they are easier and less expensive to fix
- Block transports with harmful content before they are released
- Receive actionable remediation guidance for each issue Inspect third-party transports before importing into your system
Building Onapsis Transport Inspection into Your Processes
There are two main types of implementation for transport inspection-“real time” transport inspection, which addresses all five types of issues described above, and continuous monitoring of the transport queue, which focuses on security and compliance.
Implementation Type 1: “Real Time” Transport Inspection
The first implementation type integrates at two critical steps of the standard transport process-first, before a transport is released and exported from the development system and second, before a transport is imported into production. While the focus of the first integration point is more on security and compliance, the added value of the second integration point lies in the knowledge about which transports will be imported together. This enables the transport inspection to identify potential missing objects as well as any downgrades to be expected.
Step 1: Scan Each Transport Automatically before Export/Release
Focuses on security and compliance. Nevertheless, checks on missing objects are also possible by analyzing the transport’s objects and checking how they fit into the QA system.
- Transport scan is triggered when someone tries to release and export a transport from DEVIf no findings, the transport proceeds as normal to release
- If findings, results are presented in SAP Transport Management System user interface with a description of the finding, business impact, criticality and remediation guidance
- Depending on the Risk Grading associated with the finding and depending on the developers’ authorizations, they can fix these issues and reload, continue or cancel the transport request. Or, they must request an approval, in which case all configured approvers will be notified via SAP Office Mail about this transport
- If one approver approves, the transport is released, and the creator informed. If not approved, the transport is canceled, and the creator informed
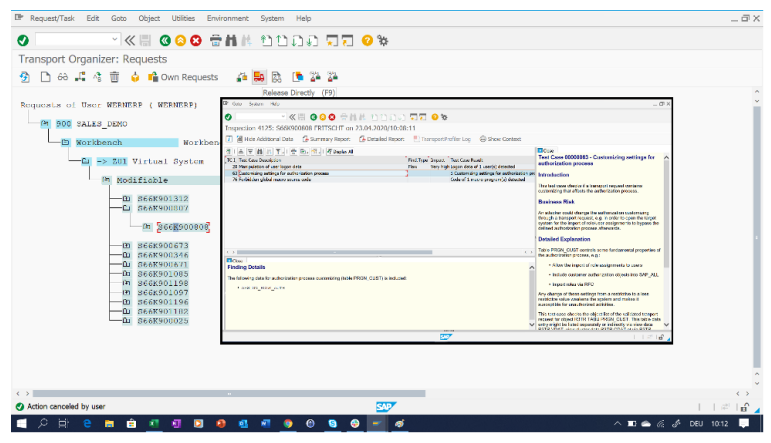
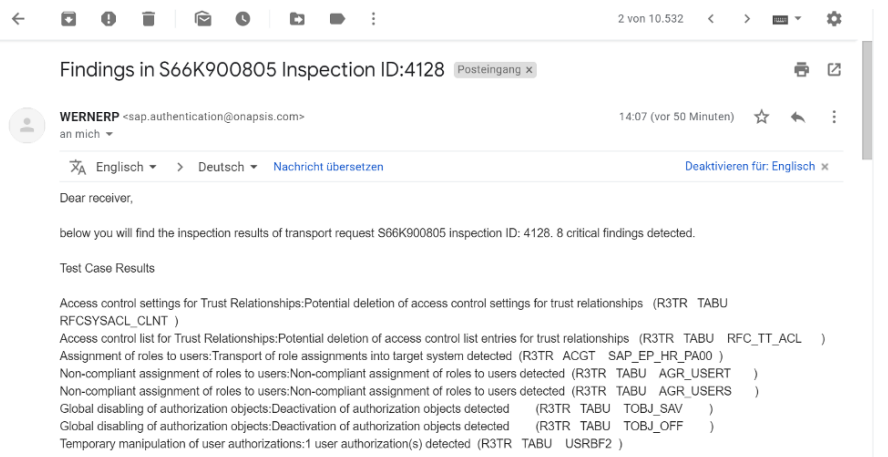
Example “real-time” scan results in Eclipse development environment.
Step 2: Scan Transports Automatically before Import
Focuses on object completeness and consistency. In order to do that, all transports that are marked for import are analyzed together. The aggregated object list of all those transports is checked for referenced objects that are missing-and thus would result in import errors, downgrades, outages and performance problems.
- Transport scan is triggered when someone tries to import one or multiple transports into the system
- If no findings, the import proceeds as normal
- If findings, results are presented in SAP Transport Management System user interface with a description of the finding, business impact, criticality and remediation guidance
- The user who started the import can either accept the findings and continue or he or she can skip the import process to follow the remediation guidance
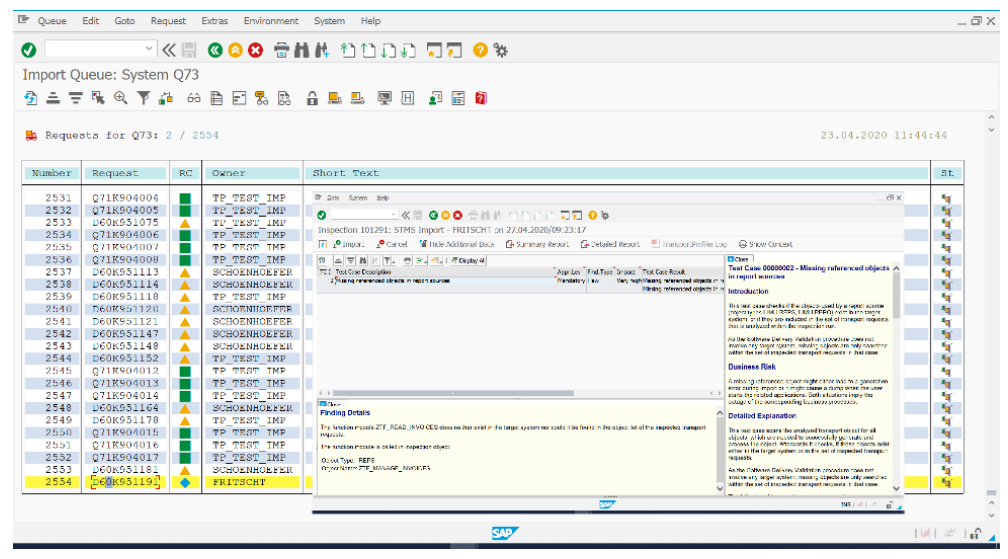
Example inspection results from prior to transport import.
Implementation Type 2: Continuous Monitoring of the Transport Queue
The second implementation type is not directly integrated into the transport process-instead, it is based on continuous monitoring of the transport queue, focusing solely on identifying security and compliance issues (e.g., new objects or content that would bring vulnerabilities into the production environment and potentially harm the system or lead to data theft or data loss).
Steps:
- Transports are scanned in the background once they have been released and exported (these scans can be scheduled to run at regular intervals per user preference)
- If errors are found, notifications are sent to assigned people showing the results of the scan
- Detailed scan results, along with remediation guidance, can be viewed by logging into the system