Who is Truly Responsible for Securing SAP Systems?
Not too long ago I published a blog which discussed operationalizing your SAP cybersecurity strategy. In that post I discussed the confusion around division of responsibilities, who should own SAP security, and how SAP security gets operationalized within the organization as this is a common problem my team and I have noticed across organizations.
Recently, the Ponemon Institute published a report titled “Uncovering the Risks of SAP Cyber Breaches,” which revealed senior level perceptions of how organizations are truly managing their SAP systems. Interestingly enough, some of the key takeaways from this study support with what my teams and I have been noticing from the gecko – organizations are not aligned when it comes to having an effective SAP cybersecurity strategy in place. Based on both our firsthand experiences, and the results of the Ponemon Institute, it seems that this is a real issue effecting a majority of organizations out there. One that needs to be formally addressed and remedied.
Let’s take a look at a couple of the key findings from Ponemon:
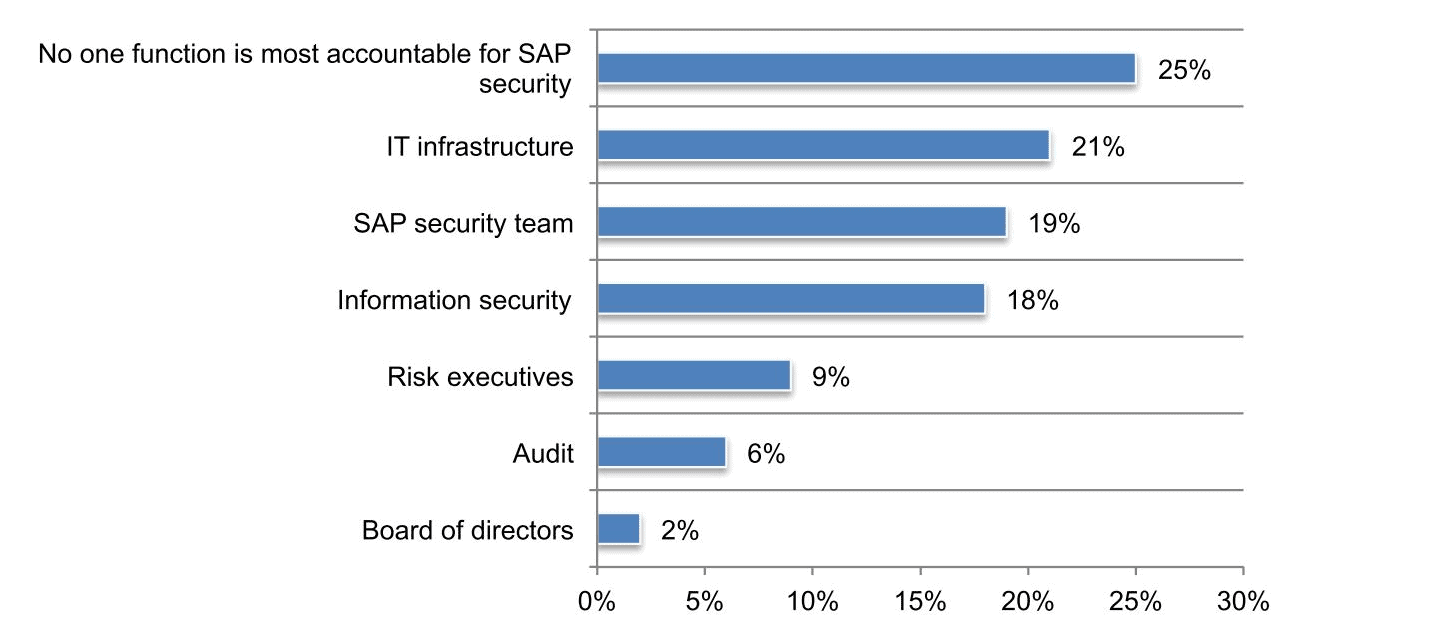
1.) No one function is most accountable for SAP security When asked about which function is the most accountable for ensuring the security of SAP systems, applications and processes, the answers from respondents were all over the map:
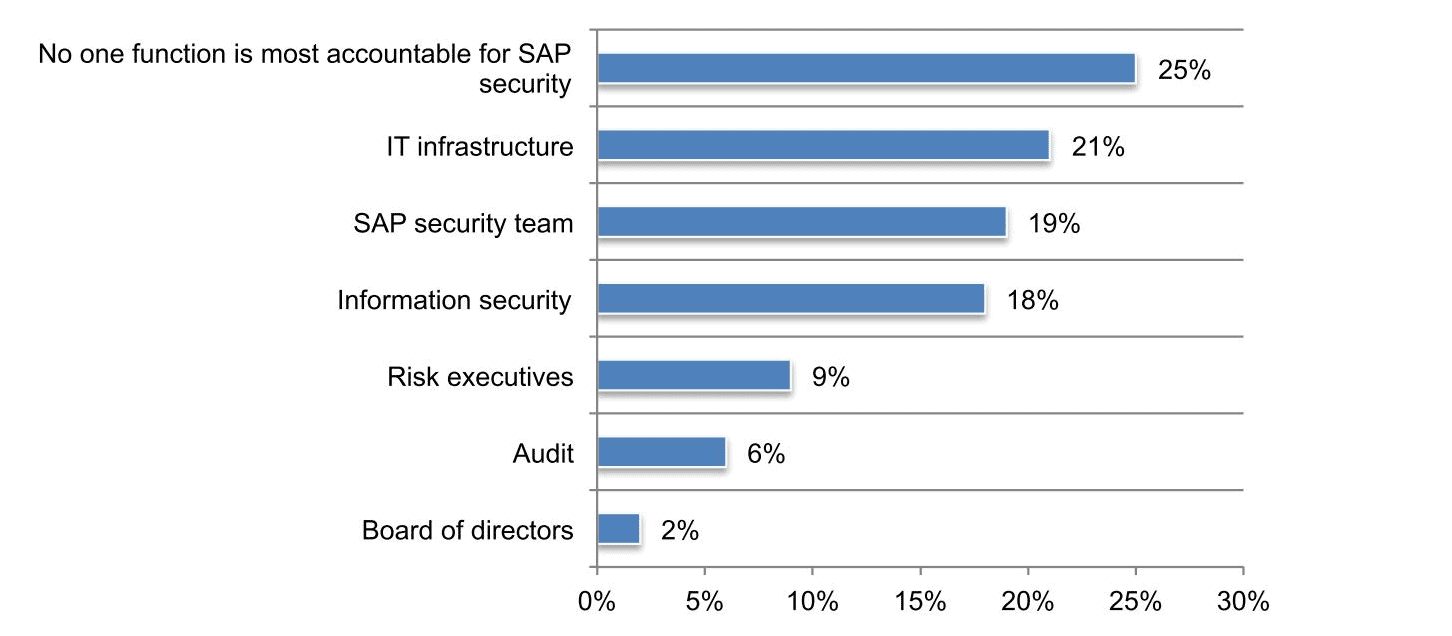
What I find most interesting about these results is that only 19% of respondents believe that SAP security teams are responsible for securing SAP systems. SAP security teams in particular should have knowledge of how attackers could leverage vulnerabilities within SAP systems in order to expose systems. That’s why SAP security teams need to work with other areas of the organization so they can pair their insight with the knowledge necessary to mitigate potential attacks.
2.) No one person in an organization is accountable for an SAP breach When asked who in an organization would be the most accountable in the event of an SAP breach, there was a very clear divide in perception:
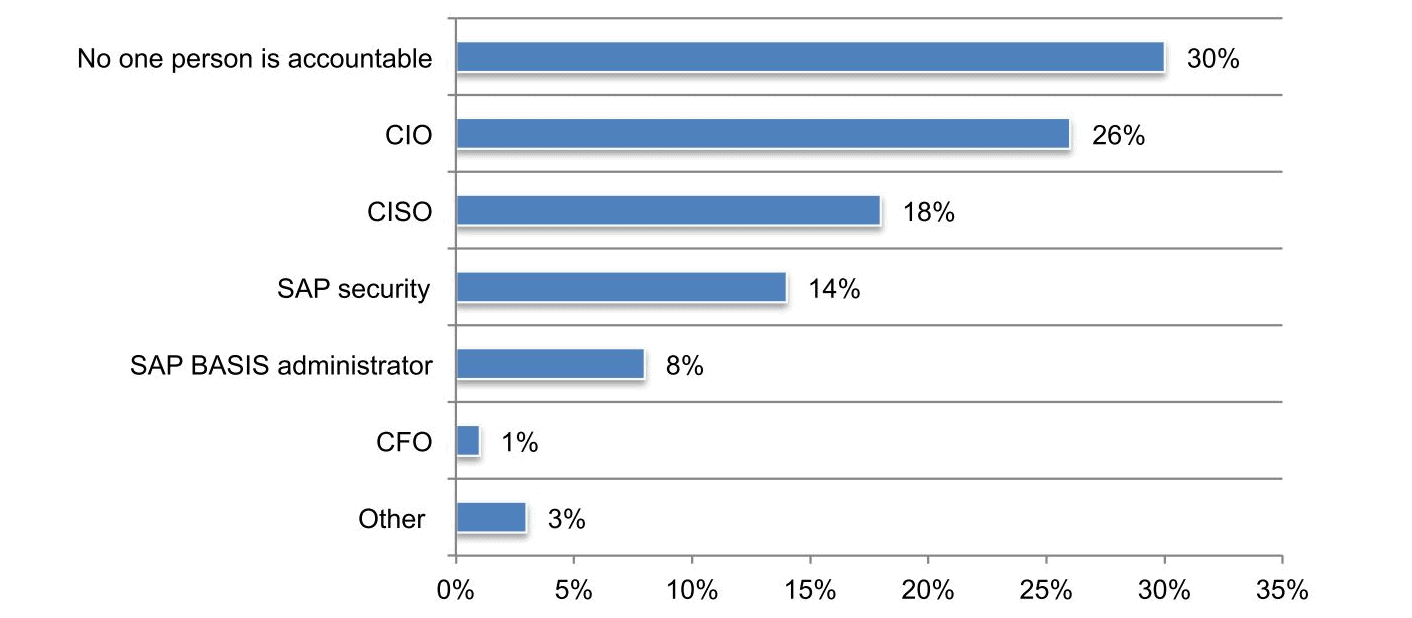
Again, I find these results very interesting. 30% of the respondents indicated no one person is accountable. Without accountability, nothing will be corrected and the problem will continue to manifest itself. It is imperative that ownership and accountability be assigned as quickly as possible within an organization. Especially because more often than not, the CIO and CISO are not even aware that they should be incorporating SAP into their overall security strategy. From an executive standpoint, the responsibilities of CIO’s and CISO’s are set at managing business risk, and business priorities. Often, they are just as disconnected with managing SAP systems as those directly managing ERP systems such as SAP. There is a lot of education that still needs to be done around why CIO’s and CISO’s need insight to SAP systems to understand the reality of the risk posture and to ultimately protect the business.
3.) It would take up to a year to detect an SAP breach When asked how soon it would take to detect a breach within the SAP platform, only 25% of respondents felt confident or very confident such a breach would be detected immediately:
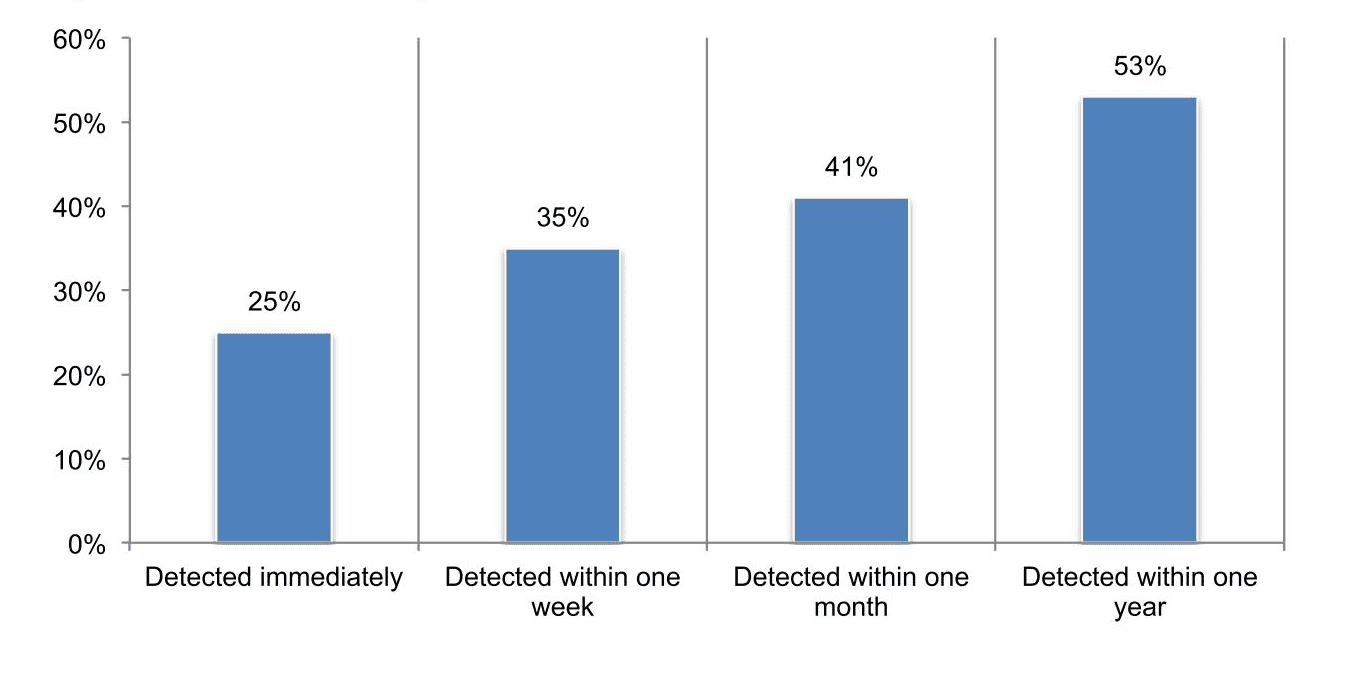
After a full year, only 53% of respondents felt confident or very confident that a breach would be detected. A full year of unknown access to arguably a company’s most impactful sources of information. The damage could be catastrophic! I guess I’m not surprised by these results however, as they support what my team is seeing throughout the industry. As attacks continue to become more advanced, it is critical that organizations start to make SAP security a priority.
As a whole, there is a lot of work to be done by organizations in order to transform their SAP security activities to become a cross-functional responsibility. SAP applications are among the most valuable assets an organization has. These systems are responsible for housing critical business processes and data in which the organization depends upon including tangible assets, customer data, financial records and personal records. Currently, there’s a gap between those who are primarily responsible for SAP itself and those who are responsible for the overall security of an organization. Security teams, and C-level executives need to come together to understand that proper security of SAP systems needs to be an aligned effort. SAP professionals need to gain insight into the vulnerabilities they need to mitigate from real world attacks, while C-level execs need insight into the reality of the risk posture facing information stored on SAP systems.
Once organizations start to take a hard look at how their SAP security strategy is structured, they can begin to find gaps within this strategy and take steps to bridge them. I’ve outlined a few of these steps in my previous blog post which can be read here.

