Webinar: How to Protect Your SAP Landscape Against Hackers
My name is Frederik Weidemann, and I am the Chief Technical Evangelist at Onapsis. If you were unable to attend my recent webinar, entitled How to Protect Your SAP Landscape Against Hackers, you may be wondering how your SAP landscape could be the target of malicious attacks through known vulnerabilities. While these vulnerabilities have been patched in prior and publicly available security notes, the reality is that IT teams have yet to do so or haven’t implemented the manual post steps, leaving your more valuable systems at risk.
When people talk about security, a frequent challenge is the debate of security versus stability. It’s the question, do we really want to invest in security, or do we want to move forward? These questions come up frequently within organizations. One of the contributing factors in the stability direction is the value of uptime, because if your system is not available and operating, you could lose out on a significant amount of money. Even a few minutes of downtime in an organization the size of Amazon can cost an incredible amount.
In that same vein, we see that over time, the mindset of the hacking community has changed greatly over the last few years. That means, stability is part of security. 20 years ago, no one was considering the value of ERP security, but in 2012, everything changed. For the first time, the SAP system of an SAP customer was exploited by a hacktivist group and was covered by the public press. Since then, ERP security has become a hot button topic, where the stakes can be extremely high if you aren’t cautious.
Now, when we discuss cyberattacks and cybersecurity, many people wonder how an attacker gains access in the first place. It’s actually much simpler than most people believe. One of the most notorious techniques is known as phishing, where the hacker attempts to gain access from someone or through malicious malware or payload via an email to an internal employee. Specific phishing attempts, known as spear phishing, are when an individual is targeted in order to gain their credentials. Once a phishing incident is successfully executed, even your internal mission-critical systems could be vulnerable to attack. And as systems are being migrated to cloud infrastructure the attack surface increases.
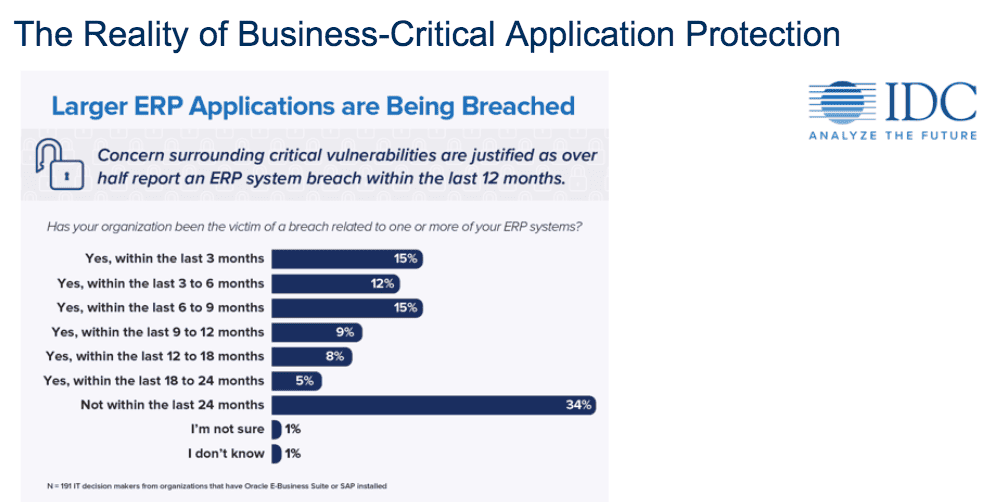
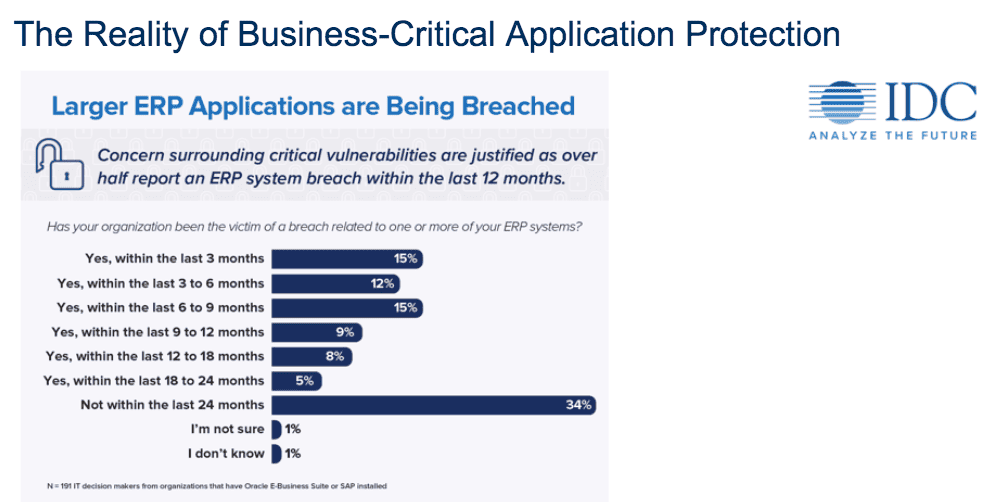
Organizations need to be regularly monitoring and protecting their ERP systems more than ever before. In fact, more than 64% of organizations surveyed in a recent IDC report experienced an ERP system breach within the last 24 months. Don’t let your business become one of them. To learn more about the security vulnerabilities you may have in your SAP landscape, watch my full on-demand webinar now.

