SAP Security Patch Day December 2020: Serious Vulnerability in SAP NetWeaver AS JAVA Requires Immediate Patching

Highlights of December SAP Security Notes analysis include:
- December Summary—14 new and updated SAP security patches released, including four HotNews Notes and two High Priority notes
- Contributions of the Onapsis Research Labs—The Onapsis Research Labs supported SAP in patching seven vulnerabilities, covered by one HotNews, one High Priority and one Low Priority Note
- Critical Patch for AS JAVA—Missing Authentication vulnerability leads to another CVSS 10 vulnerability
SAP has published 14 new and updated Security Notes on its December Patch Day. This number includes four HotNews notes and two High Priority notes.
The SAP Security Year ends with a relatively small number of new and updated SAP Security Notes. With only 14 notes, it is far below this year’s average of 20. Nevertheless, it is worth having a deeper look into the issues that are being patched as almost 50% of them are rated as HotNews or High Priority Note and some of the released notes patch multiple vulnerabilities.
Another remarkable aspect of the December Patch Day is the fact that with SAP Security Note #2974774, we are facing the fifth SAP Security Note in 2020 that is tagged with the highest possible CVSS value of 10. With the exception of the recurring Chromium Note that was updated last month to a CVSS score of 10, all other CVSS 10 notes are the result of the excellent collaboration of the Onapsis Research Labs with the SAP Security team.
In Focus: SAP NetWeaver AS JAVA
The Onapsis Research Labs has recently detected a series of different vulnerabilities in the Cluster Manager component of SAP NetWeaver AS JAVA. These vulnerabilities allow an unauthenticated attacker who is able to connect to the respective TCP ports to perform different privileged actions, such as:
- Installing new trusted SSO providers
- Changing database connection parameters
- Gaining access to configuration information
Abusing some of these actions, an attacker may be able to gain full privileged access to the affected SAP system or perform a Denial-of-Service attack rendering the SAP system unusable.
SAP Security Note #2974774, tagged with a CVSS score of 10, patches the aforementioned vulnerabilities. The patch is not provided for all support package levels and in the attached KBA note #2997167, SAP is explicitly referring to its 24 months rule, stating that security patches will only be provided for support packages not older than 24 months. The good news is that the note also provides a manual workaround that will prevent potential attackers from connecting to the P2P Server Socket port and from spying the communication between the cluster elements. This workaround can also be applied by customers running SAP NetWeaver AS JAVA on a support package level for which no patch is provided.
Further Contribution From the Onapsis Research Labs
The Onapsis Research Labs also contributed in fixing three vulnerabilities in SAP Solution Manager:
The High Priority Note #2983204, tagged with a CVSS score of 8.5, solves a Path Traversal vulnerability and a Missing Authentication vulnerability in the User Experience Monitoring component of Solution Manager. Exploiting both vulnerabilities, a remote attacker having access to an unprivileged user could partially compromise availability in making certain services unavailable. The exploits would even allow the attacker to gain access to sensitive information such as usernames and passwords that can be used to access other SAP systems in the landscape.
SAP Security Note #2938650, tagged with a CVSS score of 3.4, patches an Open Redirect vulnerability in the E2E Trace Analysis application of SAP Solution Manager. The vulnerability would allow a remote attacker to perform a social engineering attack to trick an SAP Solution Manager administrator to click on a malicious link allowing him to steal his credentials and gain access to the SAP system. The provided patch ensures that the application will only send requests to URLs which belong to Solution Manager itself.
Other Critical SAP Security Notes in December
There were another three HotNews Notes released on December’s Patch Day:
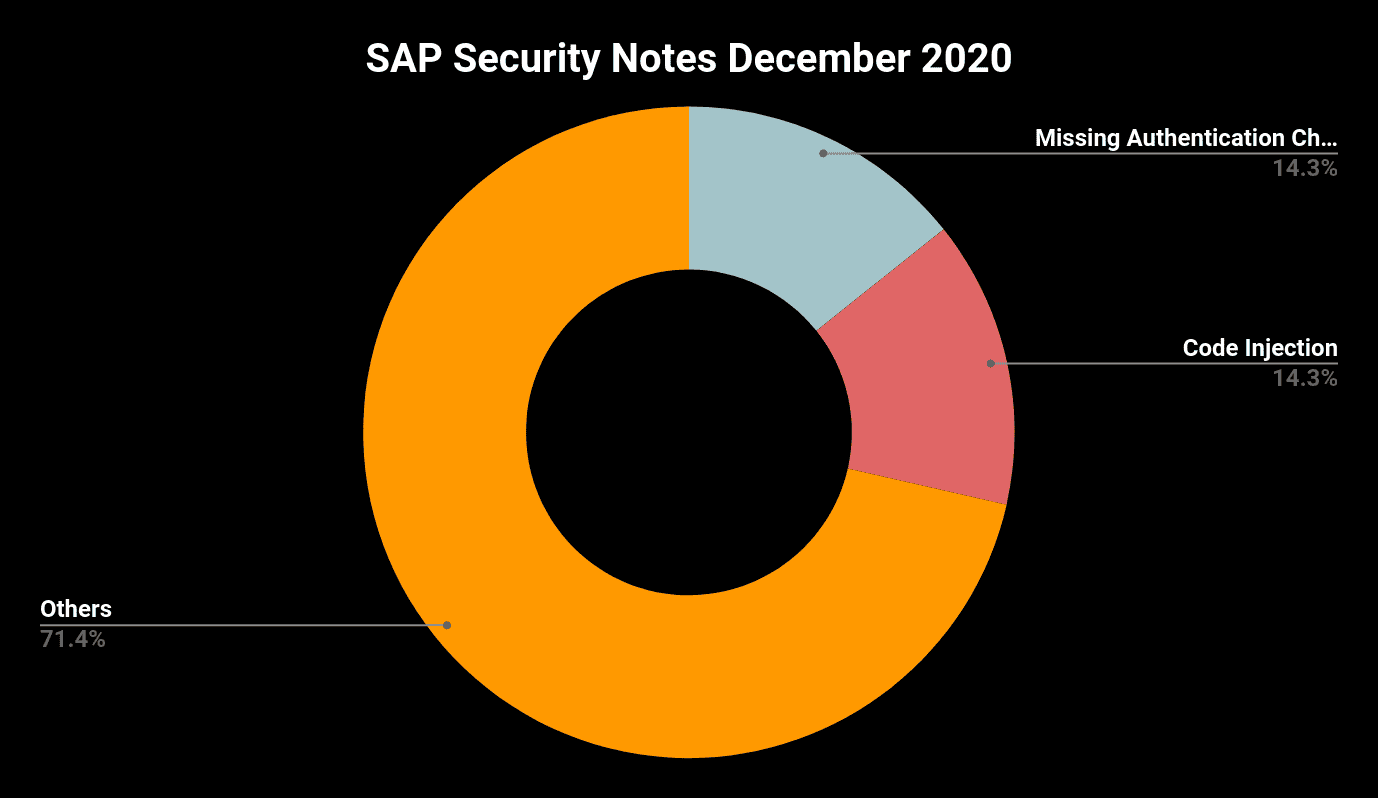
SAP Security Note #2989075, tagged with a CVSS score of 9.6, fixes a Missing XML Validation vulnerability in the Crystal Report component of SAP Business Objects. An exploit would allow an attacker with basic privileges to inject arbitrary XML entities leading to the disclosure of internal files and directories and allowing Server Side Request Forgery(SSRF) as well as Denial-of-Service (DoS) attacks.
SAP Security Note #2973735, tagged with a CVSS score of 9.1, was already released one day after SAP’s November Patch Day. The patched vulnerability affects the SAP Landscape Transformation(SLT) component of SAP NetWeaver AS ABAP and S/4 HANA systems and allows a remote attacker to inject and execute arbitrary code and thus taking complete control of the affected system.
SAP Security Note #2983367, also tagged with a CVSS score of 9.1, describes another Code Injection vulnerability which affects SAP BW Master Data Management and SAP BW4HANA. Only the fact that an attacker requires high privileges prevents the vulnerability from becoming the sixth CVSS 10 vulnerability in 2020. Having these privileges, an attacker can submit crafted requests to generate and execute arbitrary code without any additional user interaction and thus, potentially leading to a full compromise of the system’s confidentiality, integrity, and availability.
High Priority Note #2993132, tagged with a CVSS score of 7.6 fixes another issue in the SLT component of SAP NetWeaver AS ABAP and S/4 HANA systems. A missing explicit authorization check-in a remote enabled function module allowed a high privileged user to execute functions to which access should be restricted.
Summary & Conclusions
With 220 released SAP Security Notes in 2020, we are facing an increase of 23% compared to 2019 (179) and a similar number as in 2018 (215). Looking at the number of HotNews notes, there is another trend that is worth attention. With 27 HotNews notes in total, the number of notes that were tagged with a CVSS score between 9 and 10 has been more than doubled compared to 2019 (13) and is more than 5 times higher than in 2018 (5). This is reason enough to begin marking the second Tuesday of every month now in your 2021 calendars. Let’s collectively help keep SAP protected by practicing excellent patch hygiene.
As always, the Onapsis Research Labs is already updating The Onapsis Platform to incorporate the newly published vulnerabilities into the product so that our customers can protect their businesses.
For more information about recent vulnerabilities in SAP Solution Manager and how the Onapsis Research Labs is helping keep your SAP landscape protected, download our latest SAP Security In-depth publication, Preventing Cyberattacks Against SAP Solution Manager.