SAP Security Notes April 2017: Vulnerabilities Affecting SAP TREX
As with the second Tuesday of every month, today SAP released its monthly Security Notes. This month, SAP published 19 new Security Notes, as well as a summary of 28 different notes including ones published last patch Tuesday. For a second month in a row, there’s a ‘Hot News’ item relating to Remote Code Execution.
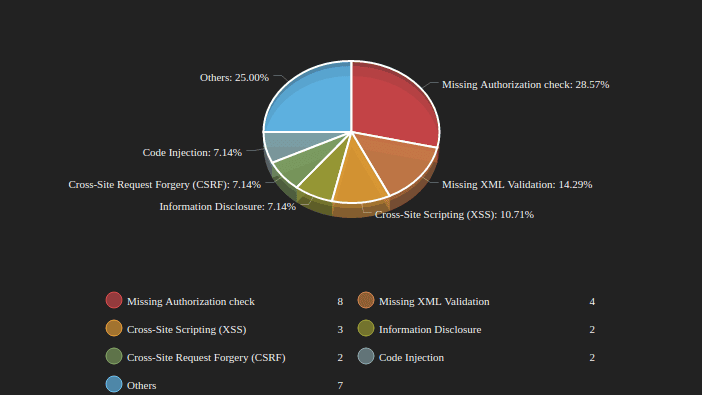
In addition to the most critical notes published this month, there are several types of vulnerabilities relating to Missing Authorization Checks, and Missing XML Validation vulnerabilities. Below, you can see a breakdown of this month’s security notes:
Per usual, let’s review the most critical notes in more detail so you have a thorough understanding of how to prioritize remediation to keep your SAP environment secure.
Hot News: Code Injection Vulnerability in TREX is Back!
There’s only one ‘Hot News’ item this month: SAP Note #2419592 titled “Code Injection vulnerability in TREX / BWA”. This note is part of a series of Security Notes released for TREX, which was originally started by a vulnerability reported by Onapsis in 2015. The TREX internal servers (nameserver, indexserver, preprocessor, and TREX web servers) communicate with each other using TREXNet. TREXNet is an internal communication protocol developed for TREX-internal communications. This protocol does not enforce any kind of authentication and it is required by TREX. Therefore, if it is exposed to malicious users, it may allow an attacker to remotely execute critical commands, not only for querying the system, but also for executing OS commands. As mentioned, the original vulnerability was fixed with SAP Note 2234226. Later, SAP released an update on the same vulnerability with SAP Note 2273881. This new SAP Note marks a third and very similar note released in this series to prevent remote command execution over TREX.
For more information on TREX attacks, you can access several resources from our Research Labs:
-
TROOPERS 2015
Speakers: Sergio Abraham, Security Innovation Lead, Onapsis Juan Perez-Etchegoyen, CTO, Onapsis
*NOTE: a live demo was not presented during this talk as it took place within the 90 day time-frame after SAP released security notes to fix this bug. Onapsis will never release technical details within 90 after the publication of security notes to give SAP customers adequate time to apply the patch.
-
TROOPERS 2016
Speakers: Nahuel Sanchez, Security Researcher, Onapsis
Juan Perez-Etchegoyen, CTO, Onapsis
It is highly recommended to implement SAP Security Note #2419592 as soon as possible. Based on the note description, this is a similar attack to the one patched two years ago, making it more likely that an attacker will be ready to exploit it.
High Priority Notes
Two high priority notes from last month have been updated. These are SAP Security Notes 2391018 and 2407616. New ‘High Priority’ notes from this month include:
CVSS v3 Base Score: not disclosed.
CVSS v3 Base Score: 7.5 / 10
CVSS v3 Base Score: 7.5 / 10
- Unauthorized usage of application functionality (#1450166): several components were patched to prevent client-side web attacks such as Cross-Site Request Forgery. After proper installation of the suggested Support Packages, a new XSRF Protection Framework will be added to the systems. Over 20 older SAP Security Notes are referenced in this note and are impacted by this new framework.
- Missing XML Validation vulnerability in Web Dynpro Flash Island (#2410082): this component is not properly validating XML documents and this could lead to arbitrary file retrieval from the server or even denial-of-service attacks.
- Security vulnerabilities in SAPLPD (#2421287): Security vulnerabilities were found in this component which was used for printing on Microsoft Windows. Since there are newer and more secure printing options, SAP recommends to switch to Frontend Print or Backend Print rather than upgrading this component (only allowed if there are compatibility issues).
- SQL Injection vulnerability in Database Monitors for Oracle (#2319506): updated in note #2418823, support packages correct an SQL Injection attack in the database layer.
CVSS v3 Base Score: 7.2 / 10.
Conclusion
After a pretty significant March Update, which included the highest critical note of the year (SAP HANA Self Service Vulnerability with CVSS 9.8 and other relevant High Priority notes) this is the second month with remote code injection vulnerabilities present. As a result, SAP Security Note #2419592 should be prioritized among the others as it implies a similar attack as the two others previously mentioned that impact TREX.
Also, it is worth taking into account that more than 20 notes can be implemented automatically, without performing the steps manually. This should help your company prioritize the implementation of all new notes, as they will take less time to implement than ones requiring manual steps.
