SAP Security Patch Day: May 2023

Highlights of May SAP Security Notes analysis include twenty-five new and updated SAP security patches released, including three HotNews Notes and nine High Priority Notes. Several critical vulnerabilities in SAP 3D Visual Enterprise License Manager’s web interface should be paid close attention. This month also marks the fourth time in a row that Onapsis Research Labs has directly contributed to SAP Patch Tuesday.
HotNews Notes released for SAP 3D Visual Enterprise License Manager and SAP BusinessObjects
SAP has published twenty-five new and updated Security Notes on its May Patch Day (including the notes that were released or updated since last Patch Tuesday.) This includes three HotNews Notes and nine High Priority Notes.
One of the three HotNews Notes is the regularly recurring SAP Security Note #2622660 that provides an update for SAP Business Client including the latest supported Chromium patches. SAP Business Client now supports Chromium version 112.0.5615.121 which fixes twenty-six vulnerabilities in total including thirteen High Priority vulnerabilities. The maximum CVSS value of all fixed vulnerabilities is 9.8. Version 112.0.5615.121 was an emergency security update by Google that fixes a critical vulnerability tracked as CVE-2023-2033. Google confirmed that “an exploit for CVE-2023-2033 exists in the wild”. Based on NIST’s description of the flaw, the vulnerability allows “a remote attacker to potentially exploit heap corruption via a crafted HTML page.”
Two of the High Priority SAP Notes, #3217303 and #3213507, are part of a series of five SAP Security Notes that were initially released in 2022, all patching Information Disclosure vulnerabilities in SAP BusinessObjects. The update explains that HotNews Note #3307833, replaces these five notes. More details can be found in the following HotNews section.
The New HotNews Notes in Detail
SAP Security Note #3328495, tagged with a CVSS score of 9.8, patches five vulnerabilities in version 14.2 of the Reprise License Manager(RLM) component used with SAP 3D Visual Enterprise License Manager. The following table provides a summary of the patched vulnerabilities:
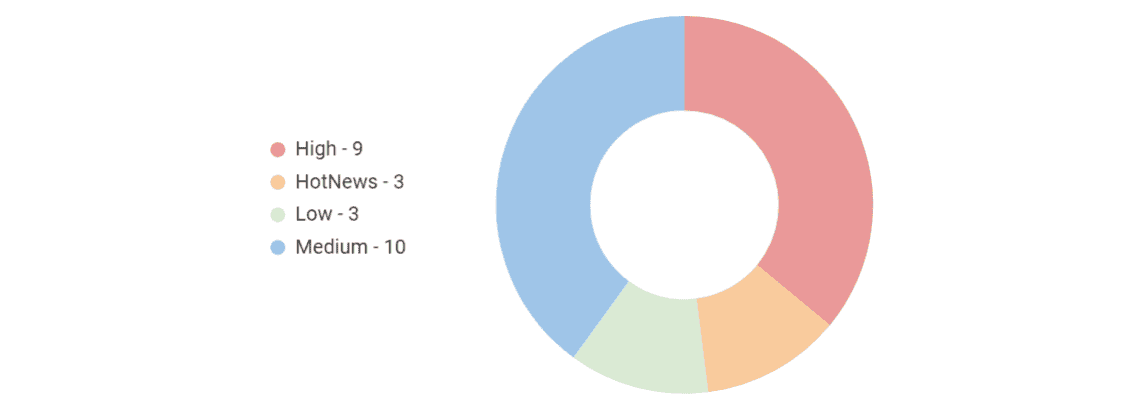
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
More details can be found above in the referenced CVE and CWE links above.
The SAP Note recommends updating SAP 3D Visual Enterprise License Manager to version 15.0.1-sap2. However, it looks like disabling the affected RLM web interface is the decisive activity to solve the issues, since the recommended patch was already released in January 2023. Disabling the web interface is also described as a possible work around. However, it is always a good idea to keep all components up-to-date. The update process provides an option to apply the newest version with disabled web interface and thus replaces the manual steps that would otherwise be necessary.
SAP Security Note #3307833, tagged with a CVSS score of 9.1, includes multiple patches for Information Disclosure vulnerabilities in SAP BusinessObjects Business Intelligence Platform. The newest and most critical one “allows an authenticated attacker with administrator privileges to get the login token of any logged-in BI user or server over the network without any user interaction. The attacker can impersonate any user on the platform resulting in accessing and modifying data. The attacker can also make the system partially or entirely unavailable”. Note #3307833 also replaces SAP Security Notes #3217303, #3145769, #3213524, #3213507, and #3233226. All notes were initially released in 2022 and updated on SAP’s May Patch Day. The update comes with two important statements:
- Customers who have already implemented these SAP Security Notes should also implement SAP Security Note #3307833 for a complete fix.
- Customers who have not yet implemented all of these SAP Security Notes should directly implement SAP Security Note #3307833.
High Priority SAP Security Notes
SAP Security Note #3317453, tagged with a CVSS score of 8.2, patches an Improper Access Control vulnerability in SAP NetWeaver AS JAVA. The vulnerability allows an unauthenticated attacker to attach to an open interface and make use of an open naming and directory API. They can then instantiate an object which has methods which can be called without further authorization and authentication. A subsequent call to one of these methods can read or change the state of existing services, causing high impact on the system’s integrity and low impact on its confidentiality.
The vulnerability was patched by SAP in collaboration with the Onapsis Research Labs. It is part of a series of other vulnerabilities– named P4CHAINS–that were patched by SAP in the last few months in cooperation with the Onapsis Research Labs. More information can be found here.
Another CVSS 8.2 vulnerability was patched with SAP Security Note #3323415. The note fixes a Privilege Escalation vulnerability in the installer of SAP IBP add-in for Microsoft Excel. If not patched, it allows an authenticated attacker to add an InstallScript custom action to a Basic MSI or InstallScript MSI project in order to extract binary files to a predefined writable folder during installation. Due to a privilege escalation, an attacker can run code as an administrator that could lead to a high impact on the confidentiality, integrity, and availability of the system.
The note says that “Users that have already installed the Excel add-in are not affected. Only newly started installations are exploitable.” This seems to be a very vague statement since customers who have used the unpatched installer in the past might already have become a victim of an exploit.
SAP Security Note #3320467, tagged with a CVSS score of 7.5, is potentially the High Priority Note of SAP’s May Patch Day that affects most SAP customers since it affects SAPGUI. It patches a vulnerability that allows an unauthorized attacker to gain NTLM authentication information from a user by tricking it into clicking a prepared shortcut file. Depending on the authorizations of the user, the attacker can read and modify potentially sensitive information after successful exploitation.
SAP Commerce is affected by two High Priority Notes, both tagged with a CVSS score of 7.5.
SAP Security Note #3321309 patches an Information Disclosure vulnerability in SAP Commerce Backoffice. The vulnerability allows an attacker to access information via a crafted POST request that would otherwise be restricted, impacting the confidentiality of the system.
SAP Security Note #3320145 provides a patch that includes a fixed version of the XStream library. Older versions of this library were vulnerable to CVE-2022-41966 allowing a remote attacker to terminate the application with a stack overflow error, resulting in a denial of service.
SAP Security Note #3300624, tagged with a CVSS score of 7.5, solves an issue in SAP PowerDesigner that can lead to a high impact on the availability of the application. The vulnerability allows an attacker to send a crafted request from a remote host to the proxy machine and crash the proxy server, due to faulty implementation of memory management, causing memory corruption.
SAP Security Note #3326210, tagged with a CVSS score of 7.1, patches an Improper Neutralization vulnerability in the sap.m.FormattedText SAPUI5 control, allowing an attacker to read or modify user’s information through a phishing attack.
Summary and Conclusion
With twenty-five new and updated SAP Security Notes, including three HotNews Notes and nine High Priority Notes, SAP’s May Patch Day is a busy one. Special attention should be paid to SAP Note #3307833 since it represents the final fix for five older SAP Security Notes.
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Onapsis Research Labs automatically updates The Onapsis Platform with the latest threat intelligence and security guidance so that our customers can stay ahead of ever-evolving threats and protect their businesses.
For more information about the latest SAP security issues and our continuous efforts to share knowledge with the security community, check out our previous Patch Day blogs and subscribe to our monthly Defenders Digest Newsletter.
