Oracle Publishes 253 New Vulnerabilities in October 2016 CPU
Yesterday, Oracle released its quarterly Critical Patch Update (CPU) to provide customers with detailed information about the latest vulnerabilities affecting Oracle business critical applications. This post will help Oracle customers better understand and prioritize the implementation of patches and testing of vulnerabilities on these systems within their organization. In this CPU, Oracle published 253 patches which affect 76 different Oracle products. We will analyze the Critical Patch Update and then will focus on the Oracle E-Business Suite vulnerabilities. The below graph summarizes the Oracle business critical applications in this CPU:
- The bars represent the CVSS Average from each Oracle product group.
- The numbers inside the bar represent the count of vulnerabilities for these Oracle product groups.
- The point represents the maximum CVSS for these Oracle product group.
- The color of the bars and the points represent the CVSS risk: Green is low, Yellow is medium, Orange is High and Red is critical.
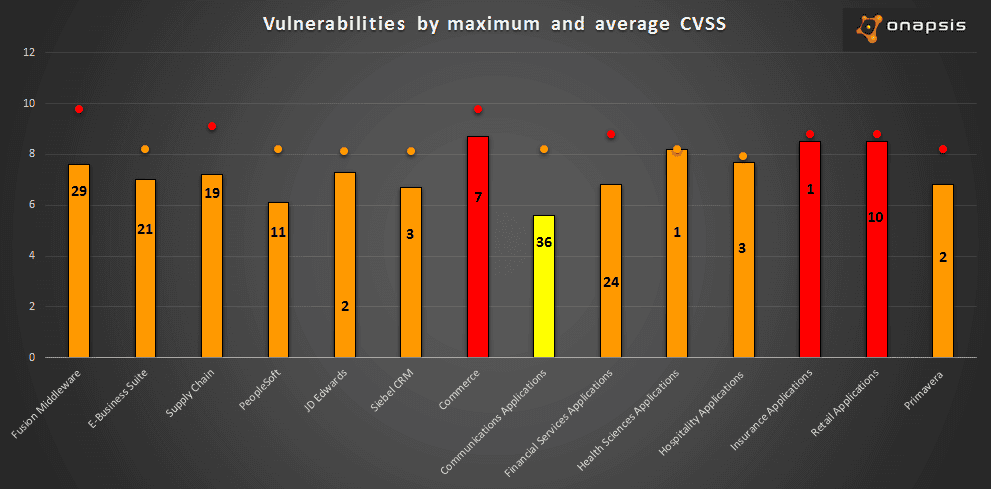
As pictured in the graph, there are a total of 169 vulnerabilities which affect Oracle business critical applications. Another important detail to note is that more than 50% of these vulnerabilities are remotely exploitable without authentication. This means that an attacker with network access could compromise these business critical applications. In this Critical Patch Update, Oracle fixed one vulnerability in Oracle E-Business Suite reported by our Research Labs. The vulnerability is related to a Cross Site Scripting attack and there is something specific on it: the bug exists in a specific servlet. Oracle, which is part of the CVE Numbering Authority (CNA) in Mitre organization, assigned the CVE: CVE-2016-5557. In the following section, we will explain why it is important to understand the attack surface in Oracle E-Business Suite, and how to mitigate the application exposure.
Attack Surface in Oracle E-Business Suite
The attack surface in Oracle E-Business Suite is very large. This is because there are a lot of applications and services installed by default in the product, and therefore are several entry points that an attacker could use to compromise the system or the company information. Some of these entry points include:
- More than 8000 JSP Java Server Pages files: These files could expose the source code and vulnerabilities. This is critical because the attacker could have the information to exploit the vulnerability.
- More than 70 servlet pages: The vulnerabilities in servlet pages are more difficult to discover and exploit for an attacker because the servlet is implemented in Java classes. To exploit, the attacker needs access to the classes, and needs to understand the relationship between the class and the exposed servlet. Then, the attacker will have to decompile it in order to view the source code and find out if there are any vulnerabilities present. Finally, the attacker has to prepare or develop the exploit.
Taking into account the size of the attack surface, and aiming to reduce it, Oracle introduced a new feature in version 12.2.2 with a whitelist to reduce the surface attack regarding the JavaServer Pages (JSP files). As with every whitelist, this allows access to the explicitly defined items and denies the rest of them. This specific case is based on the fact that most customers probably have a large amount of exposed JPS files that are not being used by the company, therefore increasing the attack surface with no benefit on usability. In version 12.2.2, the default configuration offers basic protection with minimal effort, and allows users to enlarge security by customizing the whitelist (recommended). Beginning with version 12.2.6 (release update pack), the Allowed JSPs feature is ON by default. Another way to mitigate risk posed by this vulnerability is to implement firewall configurations to restrict the access to specific urls. The vulnerability reported by our Research Labs was discovered in a specific servlet. In future advisories we will publish the full advisory with more details regarding this bug. Stay tuned for the next upcoming Critical Security Update Day, scheduled for January 2017.




