Missing Authorization Checks – SAP Security Notes September 2016
Today is the second Tuesday of September, which means that SAP has released their monthly batch of Security Notes. SAP published 21 SAP Security Notes this month (6 Notes were published after August the 8th, and did not have any Hot News items. Only four Notes this month were considered to be ‘high priority’ (16 were Medium and 1 was Low). Two of the four ‘high priority’ SAP Security Notes are related to the product SAP Adaptive Server Enterprise (SAP ASE – http://go.sap.com/product/data-mgmt/sybase-ase.html):
- The first one, #2358986 “Insufficient error checking in SAP ASE”, has a CVSS v3 Base Score of 8.8 over 10; and may give an attacker the ability to execute arbitrary SQL statements in the affected SAP ASE server.
- The second one #2353243 “SQL Injection vulnerability in SAP ASE”, has a CVSS v3 Base Score of 7.2 over 10. By abusing this vulnerability, a malicious user can create object which contain specially crafted SQL statements and execute administrative commands in the SAP ASE server.
Missing Authorization Checks
Almost half of the Notes released this month are related to Missing Authorization Checks:
- 2318530 – Missing authorization check in FI-LOC-SD-RU (High priority)
- 1627922 – Missing authorization check in SAA_REMOTE_OP_TRANSACTION (High priority)
- 2069820 – Missing authorization check in BW-BEX-ET (Medium priority)
- 2353024 – Missing Authorization check in Item Management (Medium priority)
- 2357695 – Missing Authorization check of Individual Conditions (Medium priority)
- 2357856 – Missing Authorization check of Standard Conditions (Medium priority)
- 2294866 – Missing proper authorization checks in JMS Provider Service (Medium priority)
- 2250863 – Missing authorization check in XX-CSC-IN-MM (Low priority)
What’s a Missing Authorization vulnerability?
As the Common Weakness Enumeration (CWE – https://cwe.mitre.org/data/definitions/862.html) states: “The vulnerability is given when an actor, who interacts with the system, attempts to access a resource or perform certain action in it to which access should be restricted, and the application lacks of a proper control.” Whether or not the application user is authenticated will influence the CVSS vector, thus in the CVSS scoring and priority of the SAP Security Note. Regarding SAP Security Notes (starting from September of 2009), the vulnerability Missing Authorization Check corresponds to approximately a 16 % from the total of Notes.
Summary of September Notes
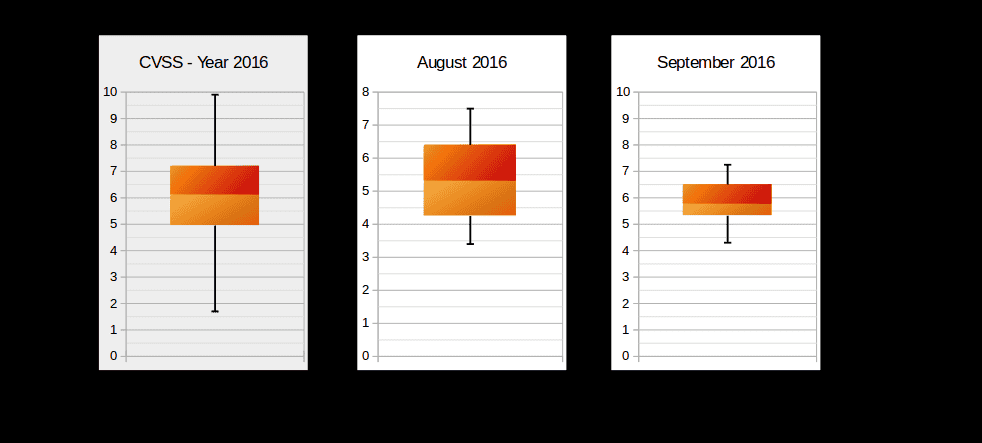
The following box-plot graph illustrates the distribution of CVSS scores across the released Security Notes. As previously mentioned, September notes are not critical compared to previous months and the year on average:
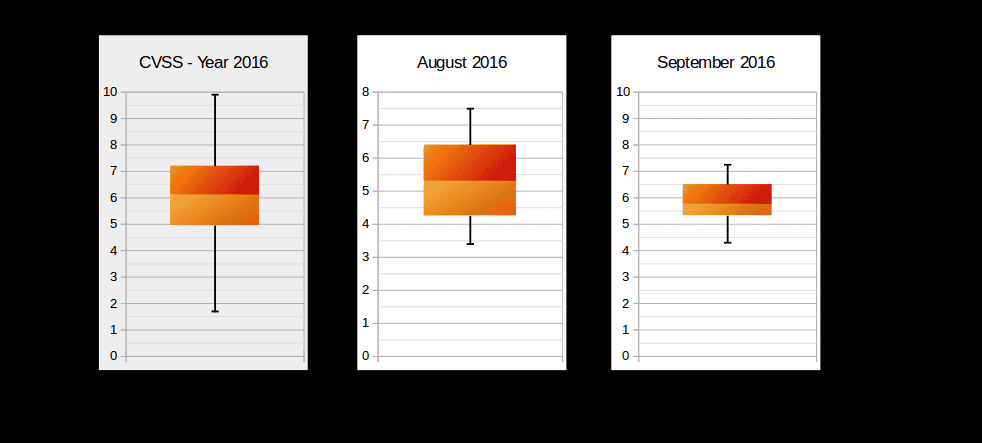
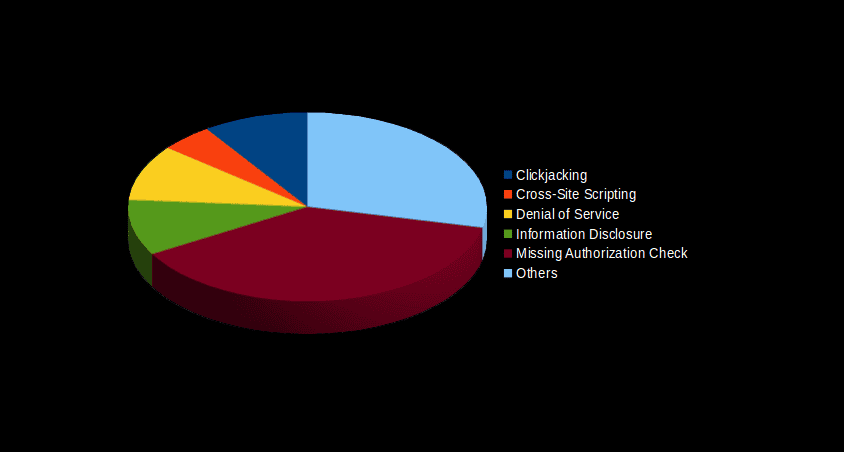
The below box-plot graph shows where the most vulnerabilities are concentrated, as well as identifies the most and least critical value notes. The graph compares the yearly average, and the last month with September. The graph below summarizes the types of vulnerabilities fixed this month: 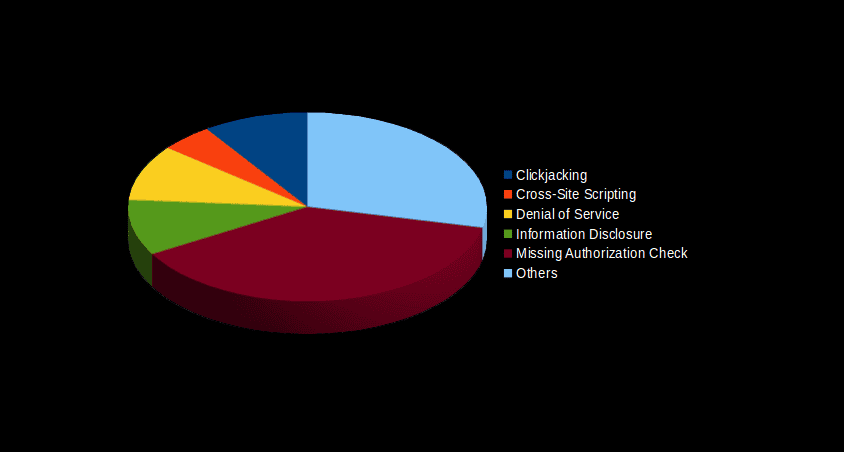
Onapsis Research Labs Contribution
This month, Nahuel Sánchez, one of the Senior Researchers at Onapsis contributed the report of a vulnerability (2347944) found in SAP HANA. By abusing this security bug, a remote unauthenticated attacker could discover the host name and the version of the CCMS agent. The CVSS v3 Base Score is 5.3. The Onapsis Research Labs are currently in the process of updating the Onapsis Security Platform to incorporate these newly published vulnerabilities. This will allow you to check whether your systems are up to date with these latest SAP Security Notes, and ensures that those systems are configured with the appropriate level of security to meet your audit and compliance requirements. Stay tuned for next month’s SAP Security Notes analysis.

