Denial of Service Attacks: SAP Security Notes August 2016
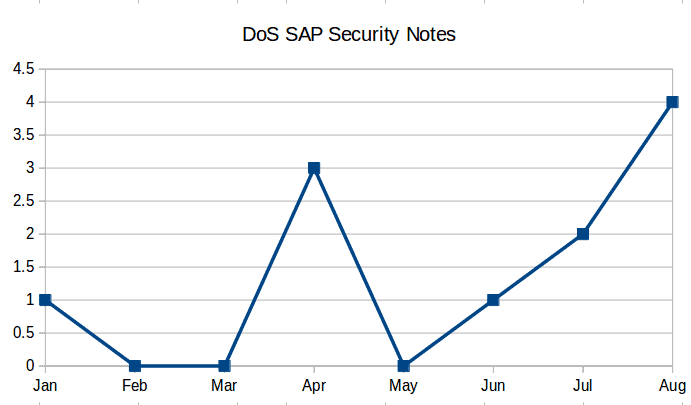
Today, SAP released their latest batch of monthly Security Notes. Despite this month not being specifically critical, Denial of Service attacks are a central point of concern. A Denial of Service (DoS) attack intends to make one or more resource unavailable. In the case of SAP, DoS attacks could be a partial and affect only a specific program or database, or they could be complete, taking all SAP infrastructure offline. This month, there are only 16 new Security Notes, and 13 updates to previously published security notes. The CVSS scores we’ve outlined below were defined by our Research Labs based on a few criteria including impact on availability, and how easy it is to exploit the vulnerability. Out of the 16 new Security Notes released this month, four are categorized as DoS attacks. Of those four, two are considered “high risk” scoring a 7.5 CVSS – one of which was reported by the Onapsis Research Labs.
Denial of Service SAP Security Notes
This month has the largest amount of Denial Of Service Security Notes so far in 2016. Historically speaking, if we take a look at previously released SAP Security Notes, July and August have more DoS vulnerabilities than the entire first half of the year. This year SAP has published 10 of 12 SAP Security Notes historically titled as Denial of Service bugs (there are also other 39 SAP Security Notes marked as “Potential DoS attack”).

This month’s SAP security notes categorized as Denial of Service are:
- 2292714: Denial of service (DOS) vulnerability in Memory Snapshot Creation; CVSS v3 Base Score: 7.5 / 10
- 2313835: Denial of service (DOS) in SAP Internet Communication Manager CVSS v3 Base Score: 7.5 / 10
- 2296909: Denial of service (DOS) vulnerability in BPM; CVSS v3 Base Score: 6.4 / 10
- 2312905: Denial of service (DOS) in SAPCAR; CVSS v3 Base Score: 3.4 / 10
The first two vulnerabilities, (including the SAP Security Note 2292714 reported by Onapsis) have the highest CVSS score for this type of attacks in SAP (including all past security notes). We never publish details of the security notes before 90 days after their publication, due to our responsible disclosure policy, but it is important to mention that the main difference between the ones with the highest score and the other ones are that both can be remotely exploited and with low attack complexity.
How bad can a Denial of Service on SAP systems be?
According to a recent study on SAP cybersecurity released by the Ponemon Institute, systems taken offline can represent an average cost for the company of $4.5 millions dollars. Since business continuity is based on SAP systems staying online, sometimes CVSS scores or vulnerability descriptions are not enough to represent how a simple bug can lead to a significant loss for companies.
Top 5 SAP Denial of Service Security Notes of All Time:
As previously explained, 7.5 CVSS v3 score is the highest scoring of the Denial of Service SAP Security Notes to date. Based on the scoring and affected components, here’s a summary of the most important notes of all time with this scoring. Two of these were discovered by our Onapsis Research Labs. August notes were not included for this analysis:
- 1.#2262710: Denial of service (DOS) vulnerability in HANA DP Agent (Apr16). Discovered by Onapsis, this note corrects how SAP HANA DP handles memory. Initially, the agent allocates memory based on the “packet length” field of that protocol and doesn’t free that memory until all bytes are transmitted. However, by abusing this behavior, a remote unauthenticated attacker could send customized packets to allocate a large amount of memory in the SAP HANA DP Agent server rendering it unavailable to other users. An advisory for this vulnerability will be published soon.
- 2. #2165583: SAP HANA secure configuration of internal communication (Nov15). SAP HANA internal services could be accessed without authentication if the HANA system is insecurely configured and no other security measures are in place. This could allow a full compromise of system availability, among others. An advisory for this vulnerability can be downloaded here.
- 3. #2306571: Denial of service (DOS) in SAP Data Services (Jun16). SAP Data Services allows an attacker to prevent legitimate users from accessing the Metadata Service from Workbench when attacker sends a crafted packet. Thus causing service disruptions during development of data services jobs.
- 4. #2330839: Denial of service (DOS) in multiple SAP Sybase products (July16). An Open Server application may crash with a segmentation violation preventing legitimate users from accessing the application.
- 5. #2258784: Denial of service (DOS) vulnerability in Enqueue Server (Apr16). Standalone Enqueue Server (ENSA) allows an attacker to prevent legitimate users from accessing a service, either by crashing or flooding the service.
Other Notes Summary
The following box-plot graph illustrates the distribution of CVSS scores across the released Security Notes. As previously mentioned, August notes are not particularly critical compared with last month and the year average:
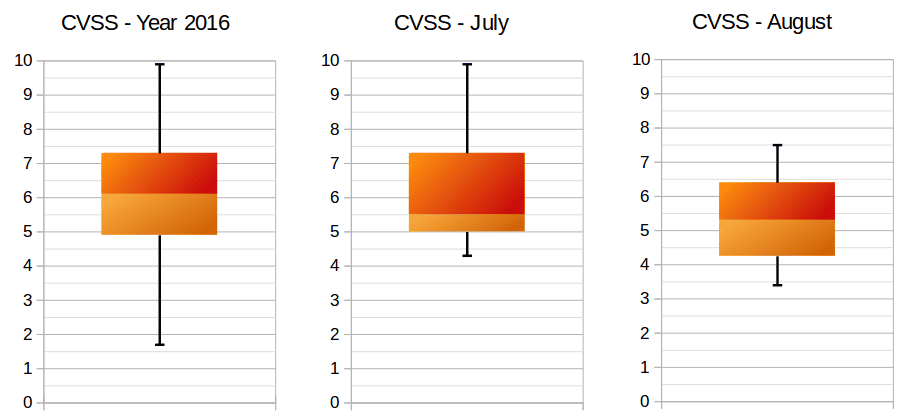
The box-plot graph is used to show where the most vulnerabilities are concentrated, and identifies the most and least critical value notes. In both cases, this month shows lower CVSS scoring compared to July and the year average. Despite what we already explained in the previous section, Denial Of Service bugs can be more dangerous than the CVSS score depicts. The below graph summarizes the types of vulnerabilities fixed this month:
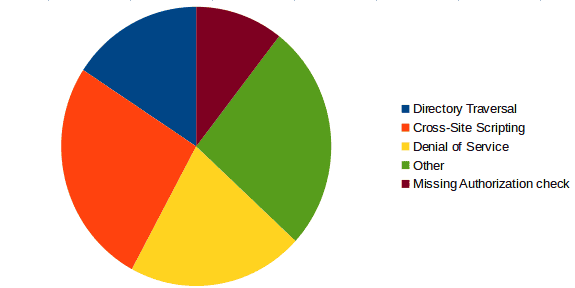
Finally, considering non-DOS notes, there are three high impact notes this month:
- #2319506: SQL Injection vulnerability in Database Monitors for Oracle: this is a traditional SQL injection bug where certain input parameters of function modules are not properly sanitized. Injecting specific malicious queries could lead to sensitive data exposure, and could allow the attacker to modify or delete data from database, among other actions. CVSS v3 Base Score: 7.2 / 10.
- #1477597: Unauthorized modification of stored content in NW KMC: malicious users can abuse this vulnerability and modify application content without authorization. This can lead to stored cross site scripting attacks, where the attacker could render the content automatically without the need of individually target the victims. No CVSS published.
- #1718230: Unauthorized modification of displayed content in StratBuild: an attacker can modify the content without permissions. In this case the attack could lead to a reflected cross-site scripting attack, that can be used for instance, to steal another user’s authentication information. No CVSS published.
The goal of this analysis is to provide SAP clients with the latest information about newly released SAP security notes and vulnerabilities affecting their SAP systems. We hope that this post will help to prompt a timely update to systems in order to ensure that newly disclosed vulnerabilities are mitigated as quickly as possible. The Onapsis Research Labs are currently in the process of updating the Onapsis Security Platform to incorporate these newly published vulnerabilities. This will allow you to check whether your systems are up to date with these latest SAP Security Notes, and ensures that those systems are configured with the appropriate level of security to meet your audit and compliance requirements. Stay tuned for next month’s SAP Security Notes analysis.

