A CISO's Guide to SAP Security on AWS and Azure

The New Frontier: Why SAP Cloud Security is a Top Priority
The migration of mission-critical SAP workloads to public cloud platforms like Amazon Web Services (AWS) and Microsoft Azure represents one of the most significant shifts in enterprise IT. This move offers unparalleled agility, scalability, and innovation, but it also introduces a new frontier of complex security challenges.
For CISOs and security leaders, the core challenge is clear: the attack surfaces and security considerations in the cloud are fundamentally different from those in traditional on-premise data centers. Simply “lifting and shifting” an SAP system without adapting the security strategy can expose the organization’s most valuable assets to new and significant risks. A proactive approach to SAP cloud security is no longer optional; it is essential for a secure digital transformation.
The Foundation: Mastering the Shared Responsibility Model
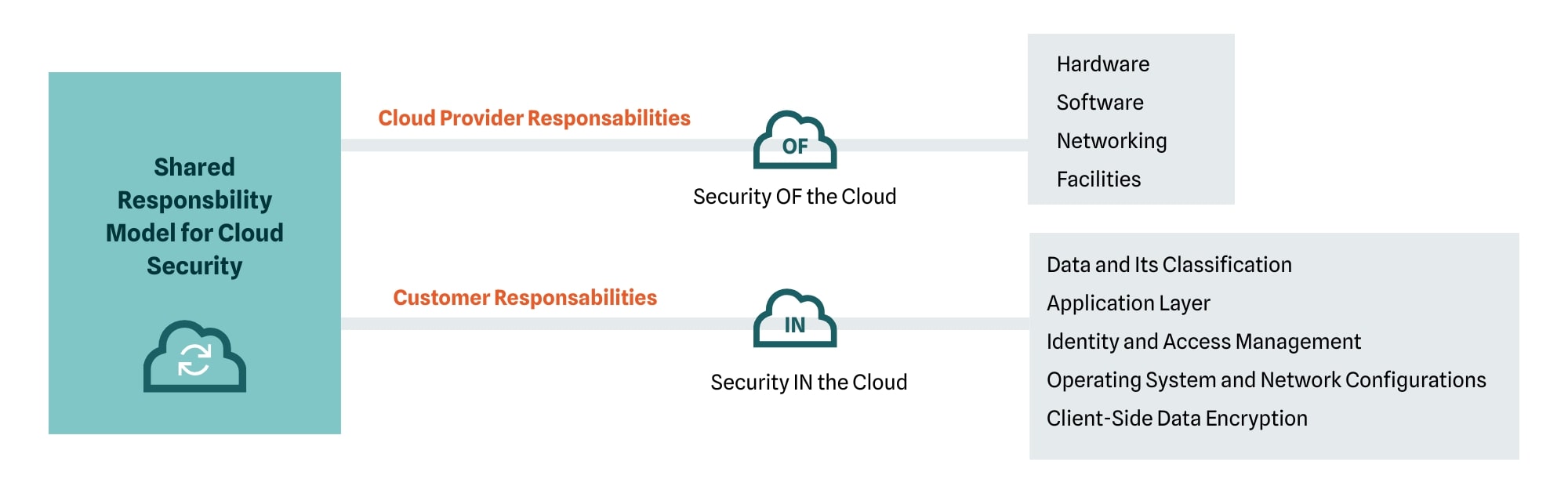
Before deploying or securing SAP in a public cloud, every member of your team must understand the Shared Responsibility Model. This is the foundational security principle that defines the division of responsibilities between the cloud service provider (like AWS or Azure) and you, the customer. Misunderstanding this model is one of the most common sources of security incidents in the cloud.
What is the Shared Responsibility Model?
In short, the cloud provider is responsible for the security OF the cloud. This includes protecting the hardware, software, networking, and facilities that run the cloud services.
You, the customer, are responsible for security IN the cloud. This includes all the data, applications, and configurations you place on the cloud infrastructure, such as:
- Your data and its classification
- The application layer (the SAP software itself)
- Identity and access management
- Operating system and network configurations
- Client-side data encryption
Why It’s Critical for SAP Security
This distinction is absolutely critical for SAP security. AWS and Azure will not patch your SAP systems, manage your user authorizations, or secure your custom ABAP code. The customer is solely responsible for the complete SAP application security layer. This means your team must still handle all traditional SAP security tasks, including vulnerability management, threat detection, and access governance, within the cloud environment you manage.
Key Security Considerations for SAP on Microsoft Azure
When running SAP workloads on Microsoft Azure, security teams can leverage a suite of powerful, integrated tools to protect their environment. The key is to combine Azure’s infrastructure security with a deep understanding of the SAP application’s needs.
Identity and Access Management with Microsoft Entra ID
One of the most significant advantages of using Azure is the native integration with Microsoft Entra ID (formerly Azure AD). By connecting SAP to Microsoft Entra ID, organizations can centralize identity management and dramatically improve security. This enables:
- Single Sign-On (SSO): Users can log in to SAP using their primary corporate credentials, eliminating the need for separate SAP-specific passwords.
- Multi-Factor Authentication (MFA): You can enforce corporate MFA policies for SAP access, providing a critical layer of protection against credential theft.
Network Security Best Practices
Securing the network perimeter for your SAP systems in Azure is fundamental. Best practices involve using Azure Virtual Networks (VNets) to create an isolated network space for your SAP landscape. Within this VNet, you should use Network Security Groups (NSGs), which act as a stateful firewall, to strictly control traffic between subnets (e.g., separating the database, application, and presentation layers) and to and from the internet.
Threat Detection with Microsoft Sentinel
For unified threat monitoring, integrating SAP with Microsoft Sentinel, Microsoft’s cloud-native SIEM, is essential. By using a certified connector, you can forward critical SAP security audit logs into Sentinel. This allows your security operations center (SOC) to correlate SAP security events with data from the underlying Azure infrastructure, providing a single pane of glass to detect and respond to sophisticated threats that span both the application and infrastructure layers.
Key Security Considerations for SAP on AWS
For organizations running their SAP workloads on Amazon Web Services (AWS), a similar multi-layered security approach is essential. While the principles are the same as with any cloud provider, the specific tools and services are unique to the AWS ecosystem.
Differentiating AWS IAM and SAP Roles
A critical concept to understand is the separation between infrastructure and application access. AWS Identity and Access Management (IAM) is used to control who can access the underlying AWS resources, such as starting or stopping the EC2 instances that host your SAP systems. It does not, however, control what a user can do inside the SAP application. Application-level access is still managed exclusively by SAP roles and authorizations. Granting a user restrictive IAM permissions does not prevent them from misusing their permissions within the SAP application itself.
Securing Your Virtual Private Cloud (VPC)
The networking foundation for SAP on AWS is the Virtual Private Cloud (VPC), which provides a logically isolated section of the cloud. To secure your SAP landscape, you must use a combination of controls:
- Security Groups: These act as a virtual firewall for your EC2 instances, controlling inbound and outbound traffic at the instance level.
- Network Access Control Lists (NACLs): These are an additional layer of defense that act as a firewall for subnets, controlling traffic in and out of one or more subnets.
Best practice dictates placing your SAP database, application, and presentation tiers in separate private subnets with strict rules to control traffic flow between them.
Monitoring with AWS Native Tools
AWS provides powerful native tools for monitoring the security of the infrastructure that supports your SAP systems. Two of the most important are:
- AWS CloudTrail: This service provides a complete audit trail of all API calls and user activity within your AWS account. It is essential for tracking changes to your environment and for forensic investigations.
- Amazon CloudWatch: This service monitors your AWS resources and applications in real time, allowing you to collect logs, track metrics, and set alarms for suspicious or anomalous activity at the infrastructure level.
How Onapsis Enhances SAP Security in the Cloud
While native cloud security tools from AWS and Azure are essential for securing the underlying infrastructure, they have a significant blind spot: the SAP application layer. These tools lack the deep visibility required to understand SAP-specific vulnerabilities, threats, and compliance issues.
This is the critical gap that The Onapsis Platform fills. It provides a consistent layer of security that operates inside the SAP application, regardless of the cloud provider. Onapsis enriches your cloud security posture by:
- Providing Deep Application Visibility: Onapsis identifies and helps remediate risks within the SAP application itself, including custom code vulnerabilities, misconfigurations, and unauthorized access—risks that are invisible to infrastructure-level tools.
- Ensuring a Consistent Security Posture: It allows you to enforce a single, consistent security and compliance policy across all your SAP systems, whether they are on-premise, in a private cloud, or in hybrid and multi-cloud environments as part of a secure cloud transformation.
- Integrating with Cloud-Native Tools: Onapsis feeds critical, context-rich SAP security alerts into cloud SIEMs like Azure Sentinel, allowing your security operations team to get a truly unified view of threats that span from the infrastructure to the application core.
Conclusion: Building a Resilient Cloud SAP Strategy
Securing your SAP landscape in AWS or Azure requires a multi-layered approach. Relying solely on the native security tools provided by the cloud platform leaves the critical SAP application layer exposed. A truly resilient cloud strategy integrates the strengths of the cloud provider’s infrastructure security with specialized solutions that provide deep visibility and control into the SAP application itself.
Ultimately, cloud security is not a one-time project but a continuous process. It demands a strong understanding of the shared responsibility model and a collaborative, ongoing effort between your SAP, security, and cloud teams to protect your most mission-critical assets as they move to the cloud and beyond.
Frequently Asked Questions (FAQ)
Do AWS and Azure secure my SAP applications for me?
No. This is a common and dangerous misconception. Under the Shared Responsibility Model, AWS and Azure are responsible for securing the underlying cloud infrastructure (the hardware, facilities, etc.), but you, the customer, are always responsible for securing everything you put in the cloud. This includes securing the SAP application itself, your data, user access, and configurations.
Can I use the same security approach for both AWS and Azure?
Yes and no. The core security principles are the same for both platforms: you must secure the application layer, manage access according to least privilege, and follow the Shared Responsibility Model. However, the specific tools you use to secure the infrastructure are different (e.g., Azure Sentinel vs. AWS CloudTrail, Azure VNets vs. AWS VPCs). A successful strategy uses the same overarching principles but adapts to the native tools of each specific cloud provider.
How do I get visibility into threats at the SAP application layer when I’m in the cloud?
You need a specialized solution that understands SAP application security. Native cloud provider tools are excellent for monitoring the infrastructure, but they lack visibility into the SAP application layer. To detect threats like custom code vulnerabilities or the abuse of SAP authorizations, you need a platform with Onapsis SAP products that is purpose-built to monitor and protect your business-critical applications.
What’s the biggest security mistake companies make when migrating SAP to the cloud?
The biggest mistake is ignoring or misunderstanding the Shared Responsibility Model. Companies often assume the cloud provider will handle more security than they actually do, leading them to neglect critical application-level security tasks. This can result in a secure infrastructure running a highly vulnerable and exposed SAP system.



