SAP Security Notes October '19: Only Nine New Notes, but Two HotNews

Highlights of October’s SAP Security Notes analysis include:
- Two HotNews Notes released by SAP—Critical vulnerabilities with CVSS scores of 9.3 and 9.1 fixed
- High Priority Note addressing Binary Planting vulnerability—Search algorithm used by several SAP Products allows multiple attack options
- Cross-Site Scripting vulnerabilities remain a leading topic—SAP CRM, SAP Financial Consolidation and SAP Business Objects affected
With only nine new and one updated Security Note, SAP has published an unusually low number of Security Notes for October 2019. This is the lowest number of newly published notes in the past five years. Nevertheless, with 2 HotNews Notes and one High Priority Note, this Patch Day deserves special attention as an attacker needs only one vulnerability for a successful attack.
Before describing the most critical notes in detail, a “quiet” month is a good opportunity to remind all SAP customers that there is not much time left to switch to the new SAP Support Backbone infrastructure and to enable transaction SNOTE to handle digitally signed SAP Notes! More information can be found here: Handling of Digitally Signed Notes and Connectivity to SAP’s Support Backbone.
HotNews Note affecting AS2 Adapter
The SAP Security Note with the highest CVSS rating of this month is note #2826015, titled “Missing Authentication Check in AS2 Adapter of B2B Add-On for SAP NetWeaver Process Integration”.
The AS2 adapter is used in SAP PI for communicating with business partners. It allows the secure transmission of business documents via HTTP and S/MIME over the Internet. The adapter specifies a comprehensive set of data security features, specifically data confidentiality and data authenticity, which are aimed at the B2B commerce environment. The configuration of the AS2 adapter allows two different security providers. Depending on the selected provider, a Missing Authentication vulnerability exists that can lead to sensitive data theft or data manipulation as well as to access to administrative and other privileged functionalities. For more information on the affected security provider, check the corresponding Security Note.
The CVSS score of 9.3 reflects the fact that the exploitation of this vulnerability is of very low complexity, does not need any privilege and can be initiated remotely via the network.
Second HotNews Note addresses vulnerability in SAP Landscape Management Enterprise
A critical Information Disclosure vulnerability was published today with SAP Security Note #2828682 for SAP Landscape Management Enterprise, an extra-licensed SAP software component providing a single user interface for the management and operation of heterogeneous and hybrid SAP landscapes.
SAP Landscape Management Enterprise allows the definition of custom operations, such as database refreshes. There is a provider assigned to each custom operation that contains information about the used script and other properties. You can also add further custom parameters to such a provider. SAP Security Note #2828682 talks about a risk of information disclosure if these custom parameters fulfill specific conditions. SAP describes the overall conditions for the existence of the vulnerability as “uncommon”. Nevertheless, it is rated with a CVSS score of 9.1 as the possible impact with regard to confidentiality, integrity, and availability is high.
Binary Planting vulnerability in several SAP software products
High Priority SAP Security Note #2792430, titled “Binary Planting vulnerability in SAP SQL Anywhere, SAP IQ and SAP Dynamic Tiering” describes a common vulnerability in the file search algorithm of these products. The algorithm searches too many directories, even if they are out of the application scope. Possible impacts are path traversals and directory climbings, enabling an attacker to read, overwrite, delete, and expose arbitrary files of the system. This can also lead to DLL hijacking as well as to privilege elevation. The only reason for not being a CVSS 9+ candidate is the fact that an attacker must have access to the local system in order to exploit the vulnerability.
Summary & Conclusions
As we’ve said in the title, this month there is a particularly low amount of fixes for SAP products. Nevertheless, with the existence of two Hot News and one High Priority Note, this month’s Notes should be carefully addressed, and properly prioritized for the most critical ones.
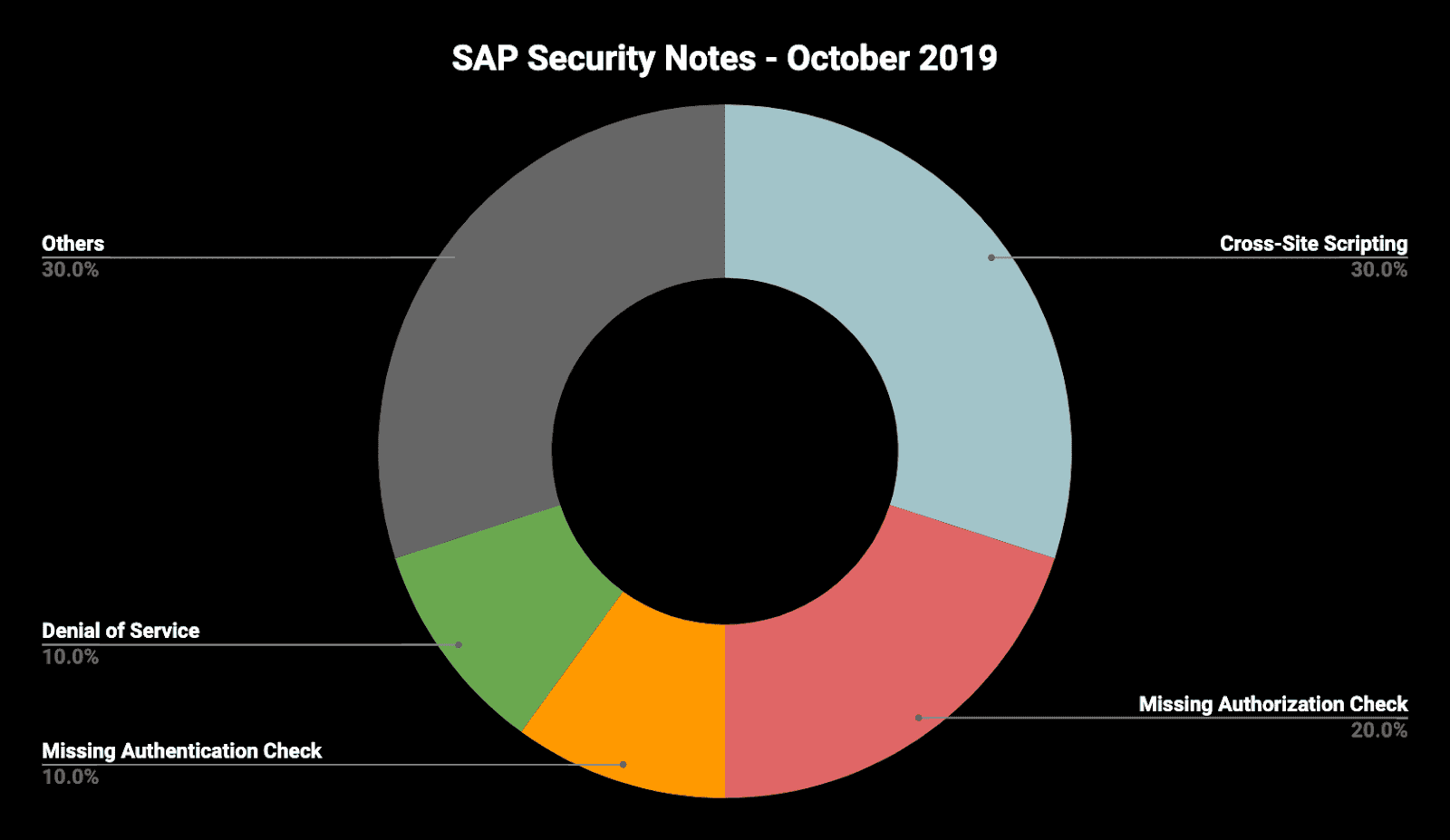
Finally, with three reported Cross-Site Scripting and two Missing Authorization vulnerabilities in various SAP software products, these two categories represent once more the majority of the published issues. This should be a wake-up call for all SAP customers to check their custom code for such vulnerabilities. Compared to the high impact of these vulnerabilities, the effort to mitigate them is highly acceptable:
As always, the OnapsisResearch Labs is already working to update the Onapsis Platform to incorporate these newly published vulnerabilities into the product so that our customers can check missing notes during their security assessments.
To learn more about the October 2019 SAP Security Notes, join the upcoming SAP Patch Day Review webinar on Tuesday, October 15. The Onapsis Research Labs will analyze the October patches and discuss how to implement them in your SAP systems.
For more information about the latest SAP security issues and to stay in tune with our continuous efforts to share knowledge with the security community, subscribe to our monthly Defender’s Digest Onapsis Newsletter.



