Analyzing SAP Security Notes June 2016

SAP systems run an organization’s mission-critical processes, and house an organization’s most sensitive data. Because of this, it is critical that these systems receive the proper security they deserve. This security begins with closing the gap of software vulnerabilities by applying security patches released by SAP in a timely manor.
SAP systems differ from traditional web applications and even operating systems due to their complexity which is caused by customized changes introduced in customer implementations, to better suit business needs (a.k.a. customizations). These customizations can sometimes make it difficult to identify whether a patch has been properly applied to ensure that newly disclosed vulnerabilities are mitigated.
In order to provide a predictable and scheduled flow of vulnerability mitigation information and security patches, SAP releases the major part of their latest Security Notes information on the second Tuesday of every month. Due to this regular disclosure of new security issues that could potentially weaken the security of SAP systems within an organization, it’s highly recommended to carry out periodic assessments on at minimum, a monthly basis.
At Onapsis, we are very concerned about the security of our client’s SAP systems. To better assist our customers, we perform a detailed analysis of the monthly SAP Security Notes, as soon as they are published by SAP. The goal of this is to provide SAP clients with detailed information about each release of new security patches which fix vulnerabilities affecting their SAP systems and help guide testing of these systems within the organization.
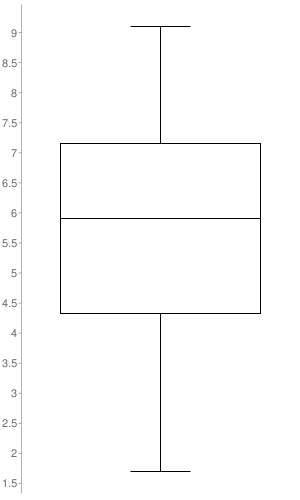
Between the last published SAP Security Tuesday and Today, there were 21 SAP Security notes published by SAP (taking into account 6 Support Packages and 15 Patch Day Notes). The plot graph illustrates the distribution of CVSS v3 scores across the released Security Notes. The only notes taken into account were the ones to which SAP set a CVSS v3 (16 out of the 21 SAP Security Notes). As it’s represented in the graph, the SAP Security Notes range values go from 1.7 to 9.1 with a median of 5.9.
Onapsis Contributions
Onapsis collaborated with SAP in fixing two vulnerabilities, thanks to security researchers Sergio Abraham, Emiliano Fausto and Juan Perez-Etchegoyen:
- 2293958 – 5.7 (AV:A/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:H). Missing communication security for SAP HANA daemon service. Since SPS10, secure internal communication is possible, however these security settings were not being applied to the SAP HANA daemon (which is an internal service used for administrative tasks such as stopping or starting the HANA System).
- 2306571 – 7.5 (AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H). Denial of service (DOS) in SAP Data Services. An attacker could send a crafted packet to generate a denial of service in SAP Data Services, thus preventing legitimate users to access the service properly.
- Update to SAP Security Note: 2252312 – 1.7 (AV:L/AC:L/Au:S/C:N/I:P/A:N). Insufficient logging of RFC in SAL. The RFC Callbacks were being logged in the Security Audit Log with an incorrect severity.
Hot News from SAP
- 2306709 – 9.1 (AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H). Code Injection vulnerability in Documentation and Translation Tools. The component BC-DOC-TER Terminologie/Glossar had a vulnerability that allowed an attacker to inject arbitrary code that would be executed by the application. This could lead to the execution of arbitrary commands in the host operating system, thus, deleting, disclosing or changing information.
SAP Security Notes with higher CVSS scoring provided by SAP
- 2222731 – 8.8 (AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:H). Unauthorized modification of stored content in DesignStudio SFIN use case. Abusing the application Design Studio embedded functionality as used in Simple Finance, an attacker may modify permanently the displayed application content. This Cross-site Scripting vulnerability can be used to potentially obtain authentication information from legitimate users of the application.
- 2308217 – 7.5 (AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H). Missing XML Validation vulnerability in Web-Survey. Web Survey had a security bug in its XML parser, that could be exploited to input a customized XML document to retrieve data or generate a denial of service from the local or a remote server.
- 2256178 – 6.1 (AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N). Cross-Site Scripting (XSS) vulnerability in ecattping. The component Extended Computer Aided Test Tool doesn’t encode properly user input, resulting in a possible Cross-site Scripting attack.
Other attack vectors
- Cross-site Scripting (XSS): Notes 2246608, 2254648, 2255588
- Information disclosure: Note 2197262
- Missing authority check: Notes 2297003, 2303386, 2316249, 2307494, 2160790
- Missing input length validation: Note 2317756
- Spreadsheet formula injection: Notes 1909843, 2272676
- Denial of Service: Note 2308778
- Directory Traversal: Note 2300346
Each month Onapsis updates its flagship product Onapsis Security Platform (OSP) to allow you to check whether your systems are up to date with these latest SAP Security Notes as well as ensuring those systems are configured with the appropriate level of security to meet your audit and compliance requirements.
Stay tuned for next month’s Security Notes analysis from the Onapsis Research Labs.
NOTE:
SAP publishes a monthly post in the SCN space “The Official SAP Product Security Response Space”, providing information about the SAP Security Notes. Here is the link to the “SAP Security Patch Day – June 2016



